Developer of Really Simple Security WordPress Plugin Failed to Fully Address CSRF Vulnerability
In January, the developers of the 4+ million install WordPress plugin Really Simple Security vaguely disclosed they had attempted to fix a vulnerability in the plugin. That was done through one of the changelog entries for version 9.2.0, “Fix: Added nonce check to certificate re-check button.” That is a reference to addressing a cross-site request forgery (CSRF) vulnerability. Checking on that months later, we found that the fix had been incomplete and that competing vulnerability data sources had failed to properly vet this and claimed that the issue was fully addressed. That includes the data source used by Really Simple Security, so their own users have not been warned the plugin is still vulnerable.
Looking at the changes made in that version, the changelog references a change made in the file /class-admin.php. That file is run during admin_init, which makes it accessible to anyone:
65 | add_action( 'admin_init', array( $this, 'recheck_certificate' ) ); |
The function included a capability check to limit access, but didn’t include a nonce check to prevent CSRF:
426 427 428 429 430 431 432 433 | public function recheck_certificate() { if ( ! rsssl_user_can_manage() ) { return; } if ( isset( $_POST['rsssl_recheck_certificate'] ) ) { delete_transient( 'rsssl_certinfo' ); } } |
Without the nonce check an attacker could cause someone with access to take the function’s action without intending it.
The version added that missing nonce check:
448 449 450 451 452 453 454 455 456 457 | public function recheck_certificate(): void { if ( ! rsssl_user_can_manage() ) { return; } if ( ! isset($_POST['rsssl_recheck_nonce_field']) || ! wp_verify_nonce(sanitize_text_field( wp_unslash( $_POST['rsssl_recheck_nonce_field' ])) , 'rsssl_recheck_nonce') ) { return; // nonce failed, do not proceed } |
A basic part of fixing a vulnerability in a WordPress plugin or vetting that someone else has done that is to make sure that similar issues don’t still exist. That didn’t happen here.
We found that three functions that are registered to be accessed through admin_init were in version 9.2.0, and still are in the latest version 9.3.1, continue to lack a needed nonce check. A fourth has a nonce check too late in the function. That is despite the security policy for the plugin claiming that “The security of our software products is essential to us and our customers. ” These issue would be caught during a security review, so security appears to be less than essential.
One of those exists in the code that is supposed to warn about vulnerable plugins, like this plugin. In the file /security/wordpress/vulnerabilities.php, the function force_reload_files() is registered to run during admin_init:
244 | add_action( 'admin_init', array($this, 'force_reload_files')); |
That includes a capability check, but no nonce check:
190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 | public function force_reload_files(): void { if ( ! rsssl_admin_logged_in() ) { return; } \security\wordpress\vulnerabilities\Rsssl_File_Storage::DeleteOldFiles(); if ( isset($_GET['rsssl_check_vulnerabilities']) || get_option('rsssl_reload_vulnerability_files') ) { delete_option('rsssl_reload_vulnerability_files'); $this->reload_files_on_update(); update_option('rsssl_clear_vulnerability_notices', true, false); set_transient('rsssl_delay_clear', true, 1 * MINUTE_IN_SECONDS ); } if ( get_option('rsssl_clear_vulnerability_notices') && !get_transient('rsssl_delay_clear')) { RSSSL()->admin->clear_admin_notices_cache(); delete_option('rsssl_clear_vulnerability_notices'); } } |
We have reached out to the developer about this and offered them free help to fix this.
Security Providers Didn’t Vet This
Here is Automatic’s WPScan’s listing presumably for this issue:
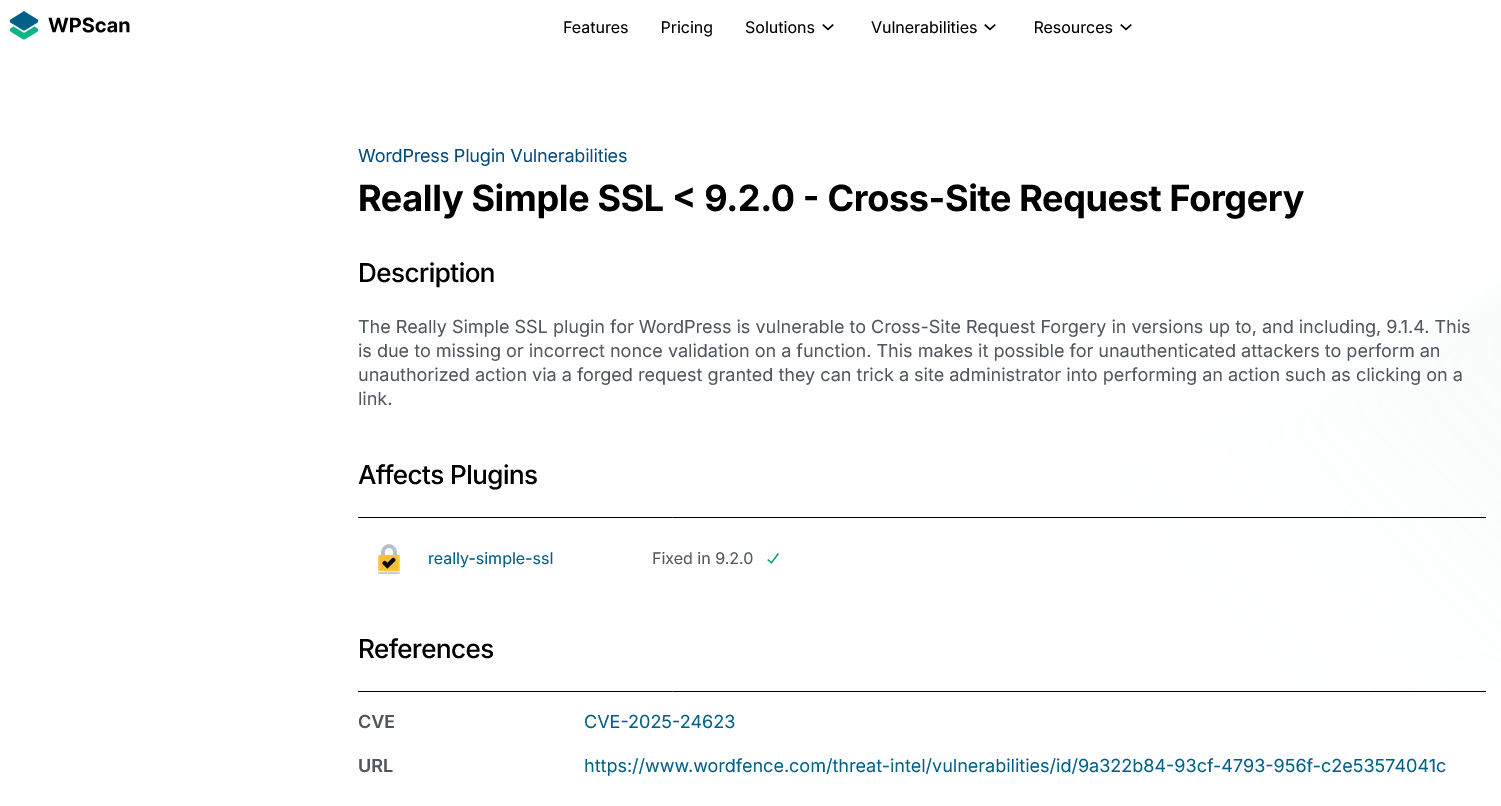
They provide no details for anyone to vet their information, but the type of vulnerability and version number match up with what is described above. They have curiously copied their information from a competitor, Wordfence, which also hasn’t provided details to vet their information:
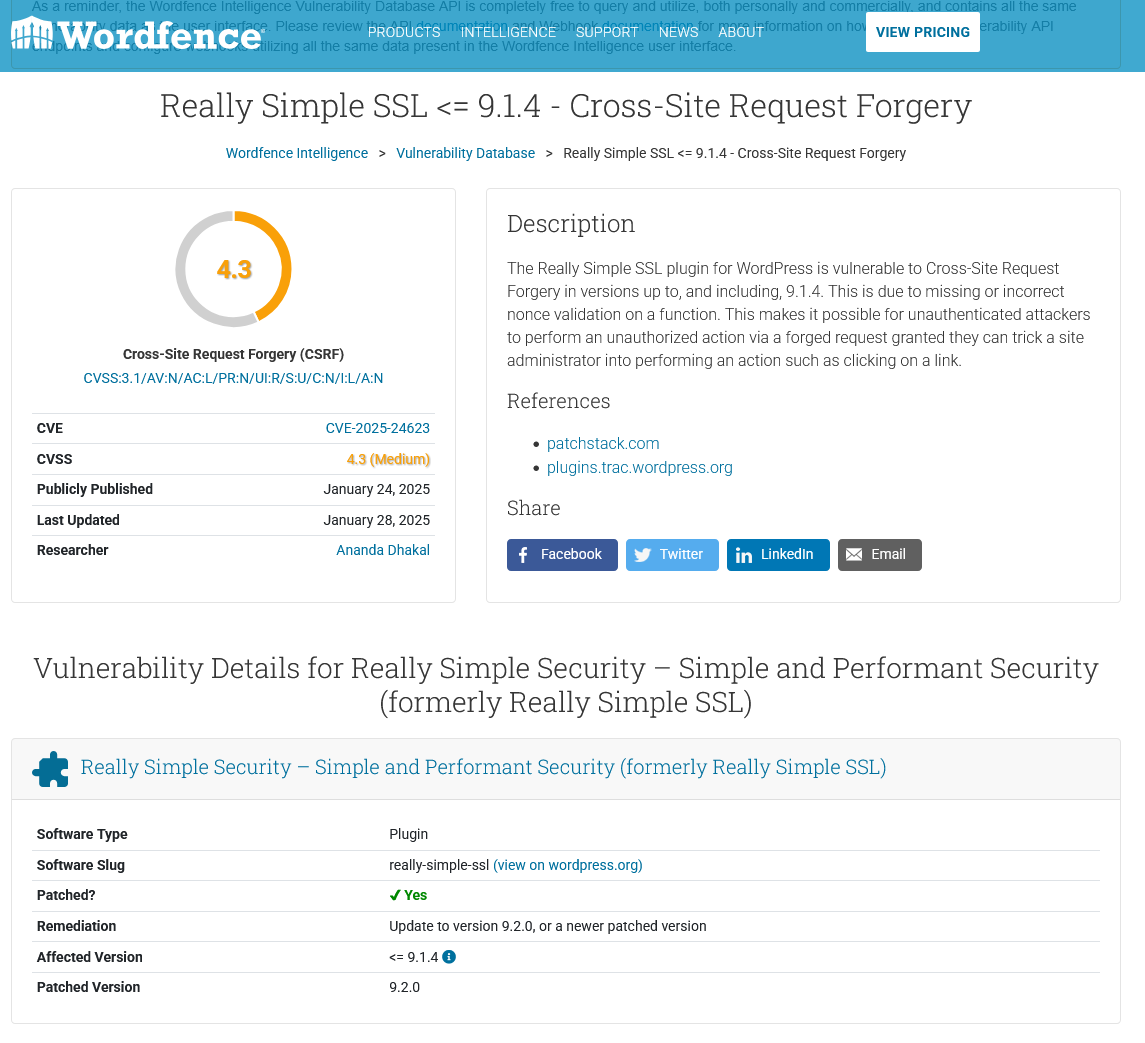
They have, in turn, curiously copied their information from yet another competitor, Patchstack, which also hasn’t provided details to vet their information:
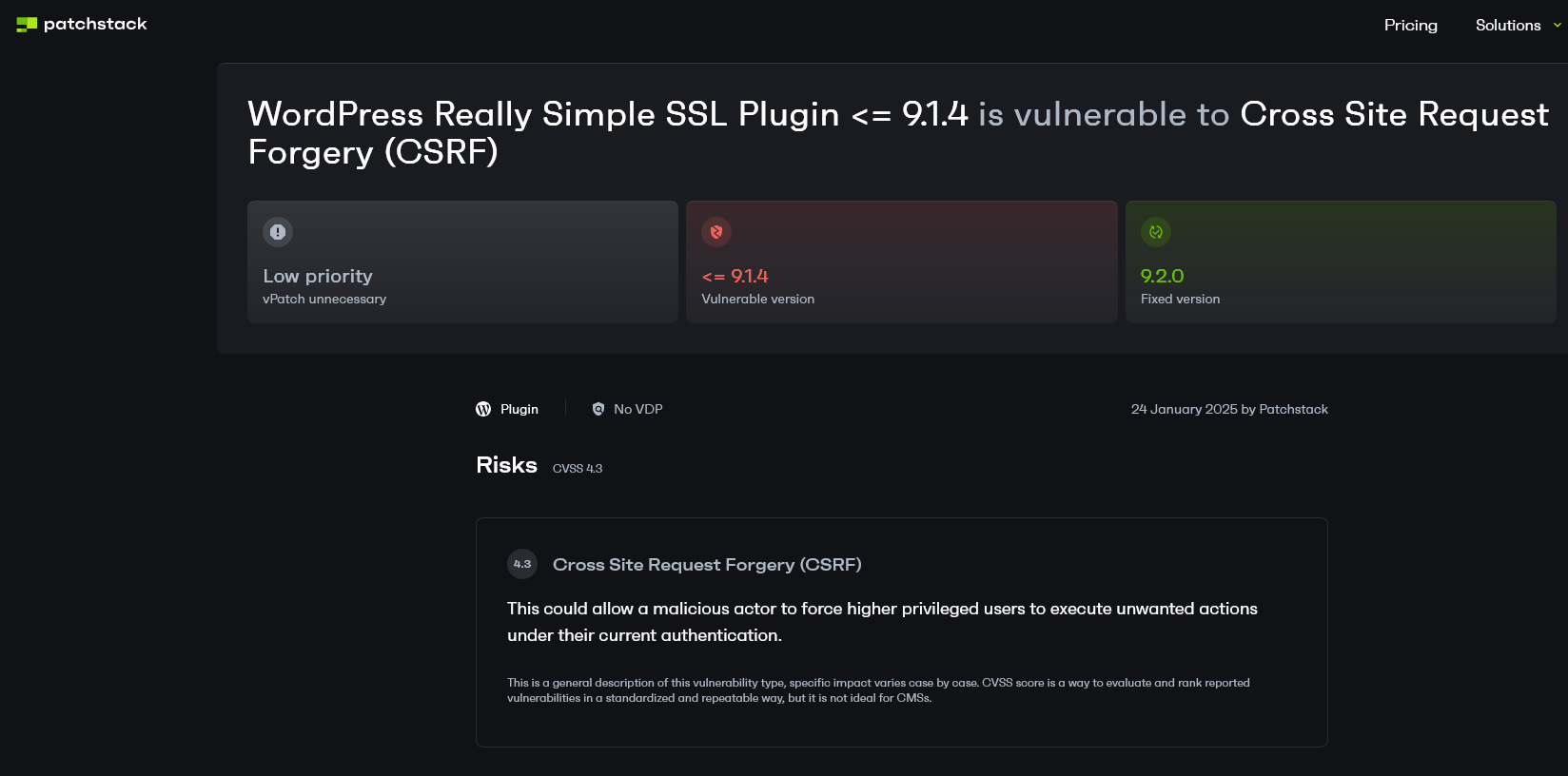
Really Simple Security Didn’t Vet Their Data Source
Really Simple Security’s vulnerability data comes from WPVulnerability, which claims under a heading, “Data reliability”, that information in their database “comes from different sources that have been reviewed by third parties.” That isn’t true. For this vulnerability, they list three sources who all claiming that the vulnerability was fixed in 9.2.0. Those sources being CVE, Patchstack, and Wordfence.
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade