On Tuesday we had what appeared to be a hacker sending multiple requests to our website attempting to access code that we found was in a WordPress plugin with 100,000+ installs, Relevanssi. (We don’t use the plugin.) Looking at the code, we found that the related code was not secure in the latest version of the plugin. Several steps later, we found that it was supposed to have been secured over a year ago, but wasn’t. That involved a claimed security researcher and another WordPress security provider, both of which don’t provide the needed information to vet their claims and make sure things actually get fixed (or make sure they are actually vulnerabilities). This is a reoccurring problem and to help warn about that, we are now compiling a database of claimed WordPress security researchers with warnings if they are causing problems like that (or a notice that they are a reliable source, for the few that are). After doing work we shouldn’t have had to do, we were able to work with the developer of the plugin to get the problem properly addressed.
Missing Capability Check
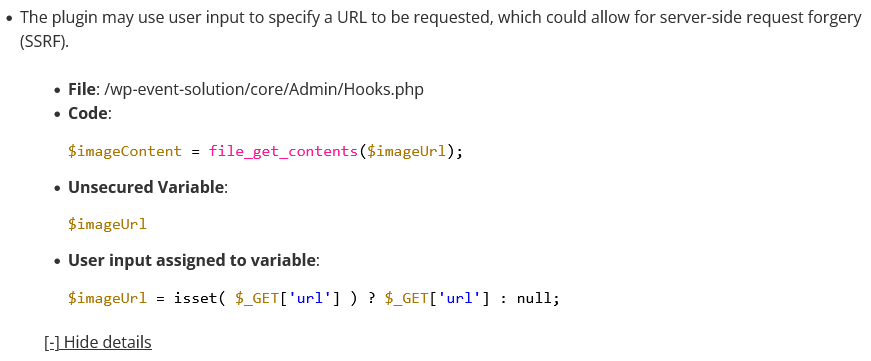
Getting back to the code being targeted, in the plugin’s file /lib/init.php, the plugin has the function relevanssi_export_log_check() run after active plugins have been loaded while WordPress is generating a page: [Read more]