Closure of Modula Image Gallery Leads to Disclosure of Authenticated Persistent Cross-Site Scripting (XSS) Vulnerability in It
Last week we started monitoring for closures of the 1,000 most popular WordPress plugins and that alerted to us the plugin Modula Image Gallery, which has 40,000+ active installations and was closed yesterday. There have been two new versions released since it was closed. The first 1.3.4 has a changelog entry of “wp.org review” and there are quite a few security related changes made in that version.
In a quick check over the code none of them stood as being obviously related to a vulnerability as opposed to general security improvement and no possible security issues were picked up with our Plugin Security Checker, so we moved on to installing a copy of version 1.3.3 and seeing if there were any easy to spot vulnerabilities we could see by checking things that way. We almost immediately found that the plugin has had an authenticated persistent cross-site scripting (XSS) vulnerability, but a closer look showed that part of this isn’t fixed as of version 1.3.5.
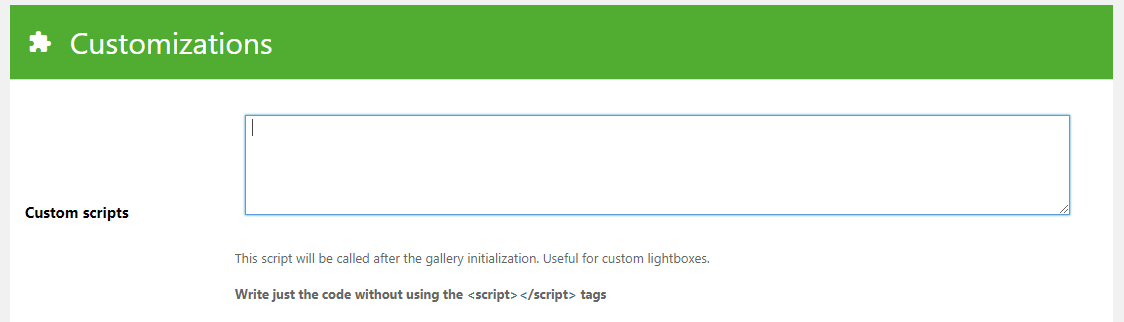
The plugin allows users with the “edit_posts” posts capability to create new photo galleries, so normally users with the Contributor and Author roles would be among those allowed to do that. Those users normally wouldn’t have the “unfiltered_html” capabilities so they shouldn’t be allowed post JavaScript code in to pages, but they are allowed to do just that due to the “Custom scripts” portion of the gallery configuration:
As of version 1.3.4 there is some sanitization done with that, which limits some JavaScript code from being entered, but as the proof of concept below shows, JavaScript code can still run.
Due to the moderators of the WordPress Support Forum’s continued inappropriate behavior we are full disclosing vulnerabilities in protest until WordPress gets that situation cleaned up, so we are releasing this post and then only trying to notify the developer through the WordPress Support Forum. You can notify the developer of this issue on the forum as well. Hopefully the moderators will finally see the light and clean up their act soon, so these full disclosures will no longer be needed (we hope they end soon).
Also we hope this type of public disclosure might teach the WordPress folks that closing plugins and then having the changes made public before they are reopened is counterproductive to their stated goal with the handling of security issues in plugins (in one recent incident it looks like it led to websites being hacked).
Proof of Concept
When you set the “Custom scripts” portion of the gallery to the following an alert box when any available cookies to be shown in an alert box on the page with the gallery’s shortcode:
alert(document.cookie);