The WPScan Vulnerability Database “Verified” False Report of Vulnerability in WordPress Plugin
In the past we have noted that among the many lies told by the company behind the Wordfence Security is that data they take from the WPScan Vulnerability Database (without disclosing it as the source) was “Confirmed/Validated”. At the time they did that, that data source was explicitly stating that they were not verifying vulnerabilities. More recently they have claimed to do that, but as shown again with a claimed vulnerability in the plugin WP Google Review Slider it turns out they are not actually doing that.
With the vulnerability they claim it is verified:
And even provide information that indicates they looked into things:
But if you look at the actual report for this you see something is off, as they provide this as the proof of concept for it:
GET/wp-admin/admin.php?page=wp_google-templates_posts&tid=1&_wpnonce=***
&taction=edit HTTP/1.1One of the URL parameters in that is “_wpnonce” with the value set to “***”. That URL parameter would usually need to be set to something different as it should be a valid value for a nonce, which is used to prevent cross-site request forgery (CSRF). In trying this out we found that it didn’t work as shown and that was because a valid nonce was not provided, as before the insecure code runs a nonce check is done:
68 69 70 | check_admin_referer( 'tedit_'); //get form array $currenttemplate = $wpdb->get_row( "SELECT * FROM ".$table_name." WHERE id = ".$tid ); |
So the report as given is not correct, but there could still be a vulnerability depending on who would have access to the relevant URL and access to a valid nonce. To be able to access the relevant page it turns out you need the “manage_options” capability:
206 | $capability = 'manage_options'; |
223 224 225 226 | $submenu_page_title = 'WP FB Reviews: Templates'; $submenu_title = 'Templates'; $submenu_slug = 'wp_fb-templates_posts'; add_submenu_page($menu_slug, $submenu_page_title, $submenu_title, $capability, $submenu_slug, array($this,'wp_fb_templates_posts')); |
Only Administrators have that capability and if you have that capability you already have the ability to do the equivalent of SQL injection, so there isn’t a vulnerability here.
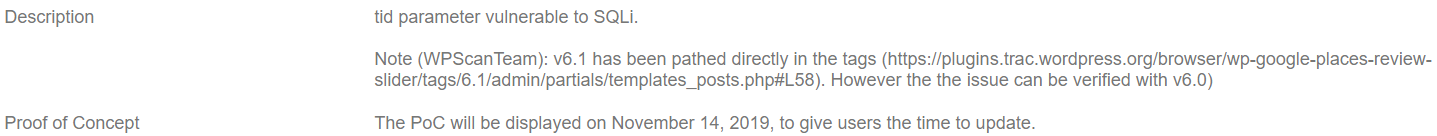
It is also worth pointing out the strange element of the WPScan Vulnerability Database’s data as they state this:
The PoC will be displayed on November 14, 2019, to give users the time to update.
The proof of concept is already public, so what is going on there? Making this worse is that if the provided the proof of concept people could see that their claim there is false.
If you are looking for data on vulnerabilities in WordPress plugins that is actually verified, so you are not being unnecessarily warned about things that are not vulnerabilities, we actually provide that.