Microsoft, Cyber Security Works, and Patchstack Don’t Understand a Basic Element of Security
Recently a security company we had not heard of before, named Cyber Security Works, released a report on a claimed stored cross-site scripting vulnerability that had been in the WordPress plugin Microsoft Clarity. The report is a mess.
They list the “affected vendor” as “WordPress 5.8.1”, while the actual vendor is Microsoft.
Like a lot of reports on claimed vulnerabilities in WordPress plugins these days, there wasn’t really a vulnerability, since the attacker would need to be logged in to WordPress an Administrator. An Administrator can do basically anything they want since they are an Administrator.
Security Needs to be Server Side
The biggest problem here, though, is that the change made that was supposed to fix this, doesn’t.
The claimed vulnerability being that JavaScript code could be saved to the plugin’s setting. It was supposed to have been fixed in version 0.4 of the plugin. The only substantive change made in that version, which changed HTML code shown on the plugin’s settings page.
Previously it was this:
62 | <input type="text" name="clarity_project_id" value="<?= $p_id_option; ?>"> |
That was changed to:
63 64 65 66 67 68 | <input type="text" name="clarity_project_id" value="<?= $p_id_option; ?>" pattern="[0-9a-z]+" title="Clarity project id should only contain numbers and letters."> |
What that does is cause a web browser to restrict the value that can be set for the plugin’s settings to only numbers and letters. That doesn’t address the vulnerability as an attacker can get around that in multiple ways, including through a web browser’s developer tools.
What should happen here, regardless of it being a vulnerability, is that the value should be validated when being saved and should also be escaped when output. We are in the process of trying to notify Microsoft about that.
It is concerning that both Microsoft and Cyber Security Works didn’t understand that since this involves basic security, not relying on client side security, since that can be bypassed by an attacker.
They are not alone in not understanding that. Here is an entry on a competing data source on vulnerabilities in WordPress plugins, Patchstack, claiming that this is a vulnerability and was fixed:
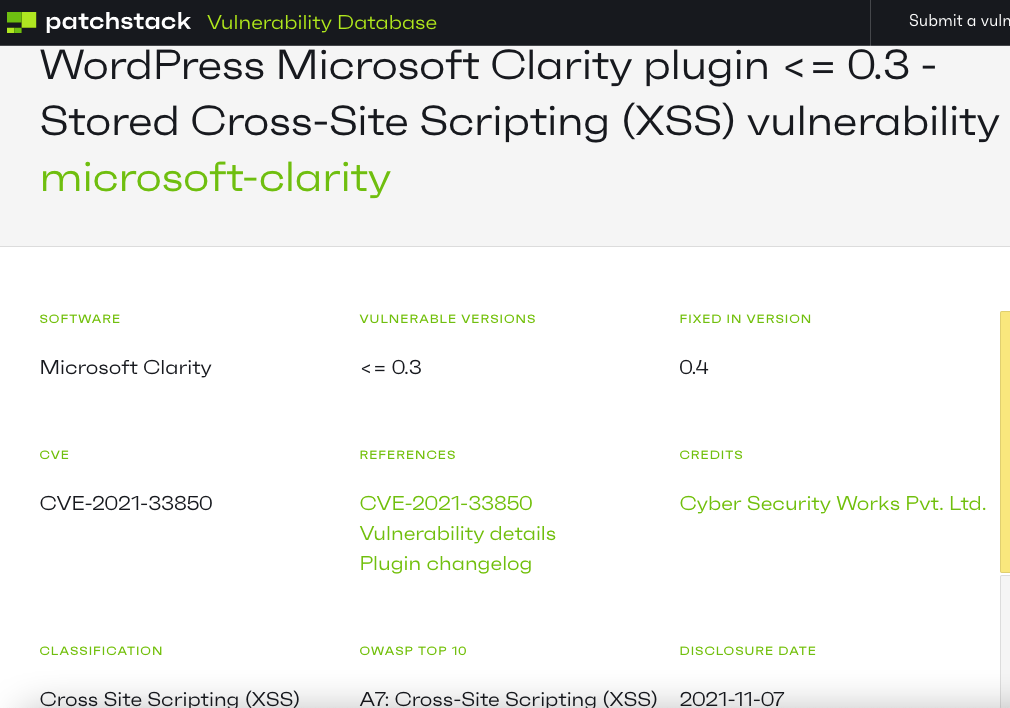
They market their database as:
Hand curated, verified and enriched WordPress vulnerability information
That continues to not be true.
How is Cyber Security Works a CVE Numbering Authority?
As this situation shows, Cyber Security Works seems have to have a problem with getting basic information right, yet as we went to look to see who they are, we found on the homepage they are a CVE Numbering Authority:

According to the CVE website, “The mission of CVE Program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities”. It seems like a bad idea to have a company that can’t basic information right involved in that. Again, according to the CVE website, that is “sponsored by the U.S. Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA)“. Why is the US government funding something that appears to have incredibly lax standards?