Authenticated Persistent Cross-Site Scripting (XSS) Vulnerability in Responsive Lightbox & Gallery
Over the weekend, a forum topic was created for the WordPress plugin Responsive Lightbox & Gallery about Wordfence claiming there was a vulnerability in the plugin:
Hi, I have just received a critical error in my wordfence dashboard that
‘The Plugin “Responsive Lightbox” has a security vulnerability … To protect your site from this vulnerability, the safest option is to deactivate and completely remove “Responsive Lightbox” until a patched version is available
Issue Found October 13, 2022 08:54’
Do you have a patch for this error, as the site is now vulnerable, and as I do like this plugin I do not want to remove it.
It seems rather unhelpful for Wordfence to be claiming that there is a vulnerability in a plugin with 200,000+ installs, but provide no information whatsoever for anyone to check on their claim. As we noted last week, they are making claims about vulnerabilities being in plugins without having any idea if the claim is true. The situation is highly problematic.
As at least one of our customers is using the plugin, we tried to figure out what was going on. In the past Wordfence’s data was mostly, if not entirely, really WPScan’s data. Wordfence didn’t disclose that, instead claiming that they were using “official” data. (Wordfence says a lot of things that are not true.) The most recently listed vulnerability for the plugin in WPScan’s data is from 2017, so that seems unlikely to be the source.
Looking around elsewhere, we didn’t find anything else that seems like it could be the source for the claim. For example, Wordfence’s own vulnerability advisory page has no listing for vulnerabilities in the plugin.
We took a look over the plugin for both serious vulnerabilities, as well as things that might not really be a vulnerability, but something Wordfence has been known to claim is a vulnerability. What we found is that the plugin contains a minor vulnerability. We do mean minor, as it would probably only be exploitable on a small number of websites, if any. That vulnerability is similar to things that are not really vulnerabilities that Wordfence would cite as vulnerabilities. We don’t know if that is the issue, but we can at least warn our customers there is an issue. If someone knows about another, please get contact us.
One of the plugin’s settings pages permits giving low-level WordPress users access to the various capabilities of the plugin:
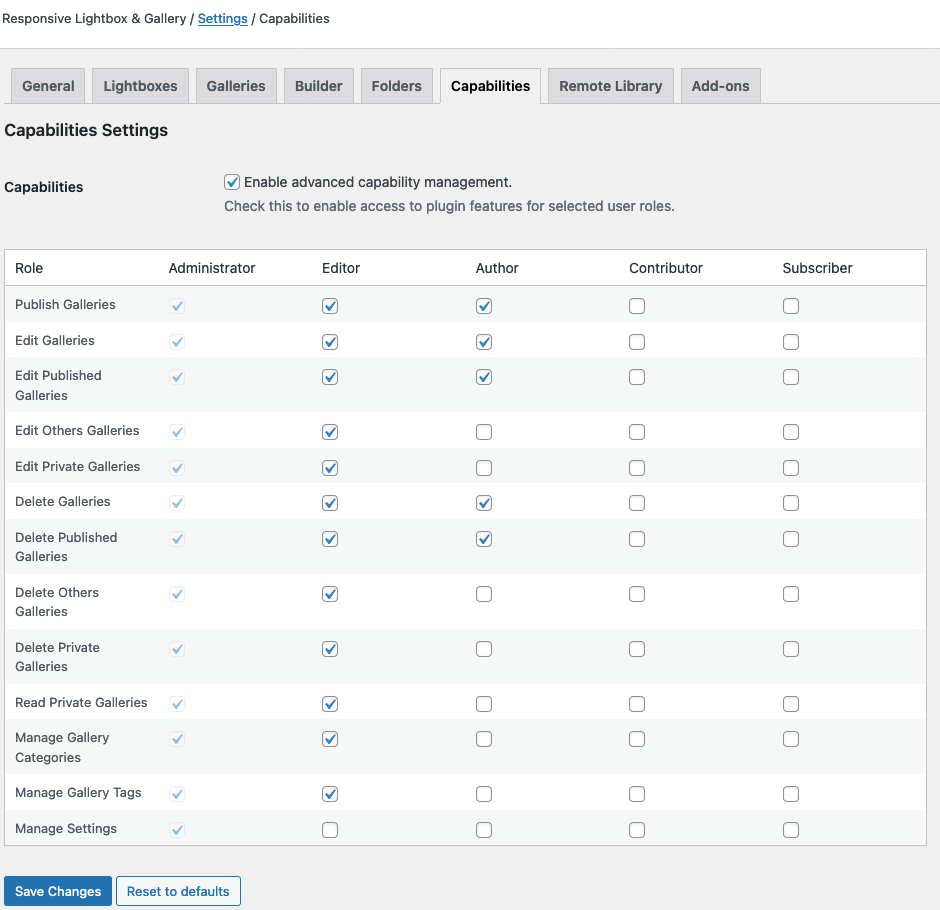
One of those is the ability to manage the plugin’s settings.
We found that with at least one of those settings, “Custom events”, on the General Settings page, you can place JavaScript code in the setting that can then run when someone accessing that page. A low-level user being able to do that is an authenticated persistent cross-site scripting (XSS) vulnerability.
WordPress Causes Full Disclosure
As a protest of the moderators of the WordPress Support Forum’s continued inappropriate behavior we changed from reasonably disclosing to full disclosing vulnerabilities for plugins in the WordPress Plugin Directory in protest, until WordPress gets that situation cleaned up, so we are releasing this post and then leaving a message about that for the developer through the WordPress Support Forum. (For plugins that are also in the ClassicPress Plugin Directory, we will follow our reasonable disclosure policy.)
You can notify the developer of this issue on the forum as well.
Hopefully, the moderators will finally see the light and clean up their act soon, so these full disclosures will no longer be needed (we hope they end soon). You would think they would have already done that, but considering that they believe that having plugins, which have millions of installs, remain in the Plugin Directory despite them knowing they are vulnerable is “appropriate action”, something is very amiss with them (which is even more reason the moderation needs to be cleaned up).
If the moderation is cleaned up, it would also allow the possibility of being able to use the forum to start discussing fixing the problems caused by the very problematic handling of security by the team running the Plugin Directory, discussions which they have for years shut down through their control of the Support Forum.
Update: To clear up the confusion where developers claim we hadn’t tried to notify them through the Support Forum (while at the same time moderators are complaining about us doing just that), here is the message we left for this vulnerability:
Proof of Concept
On the plugin’s Capabilities settings page, /wp-admin/admin.php?page=responsive-lightbox-capabilities, set a low-level role to have the Manage Settings capability.
Log in with a user with the low-level role. On the plugin’s General settings page, /wp-admin/admin.php?page=responsive-lightbox-settings, set the “Custom event” setting to the following:
" onmouseover="alert(document.cookie);
After that, when scrolling over that setting, will cause an alert box with any available cookies to be shown.