Not Really a WordPress Plugin Vulnerability – Week of November 30, 2018
In reviewing reports of vulnerabilities in WordPress plugins we often find that there are reports for things that don’t appear to be vulnerabilities. For more problematic reports we release posts detailing why the vulnerability reports are false, but there have been a lot of that we haven’t felt rose to that level. In particular are items that are not outright false, just the issue is probably more accurately described as a bug. For those that don’t rise to level of getting their own post we now place them in a weekly post when we come across them.
Arbitrary File Deletion Vulnerability in WP-DBManager
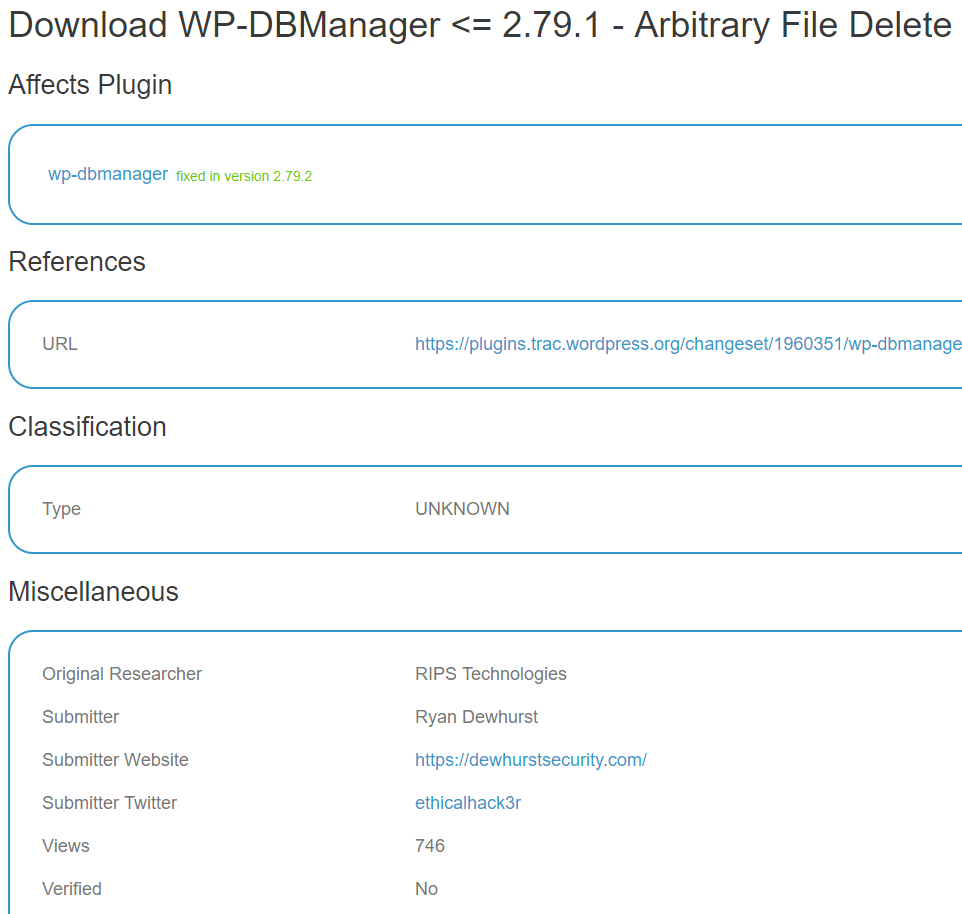
When you combine two entities that don’t seem to be concerned about the accuracy of their claims of vulnerabilities related to WordPress not surprisingly the results could be bad. Earlier this week the WPScan Vulnerability Database added this entry for a claimed arbitrary file deletion vulnerability in the plugin WP-DBManager:
They have only linked to the changes made in version 2.79.2 , so it seems possible all they actually looked at is what was mentioned in the changelog for that, “FIXED: Arbitrary file delete bug by sanitizing filename. Props RIPS Technologies.”. It isn’t clear if the lack of mention of that being vulnerability by the developer is intentionally or not.
The relevant functionality runs when accessing the file /wp-dbmanager/database-manage.php, which is done through the plugin’s Manage Backup DB admin page, which is accessible to those with the “manage_database” capability:
47 | add_submenu_page('wp-dbmanager/database-manager.php', __('Manage Backup DB', 'wp-dbmanager'), __('Manage Backup DB', 'wp-dbmanager'), 'manage_database', 'wp-dbmanager/database-manage.php'); |
That capability is normally only give to users with the Administrator role (in the function dbmanager_activate()):
462 463 464 465 466 | $role = get_role( 'administrator' ); if( ! $role->has_cap( 'manage_database') ) { $role->add_cap( 'manage_database' ); } |
Then before you get to the relevant code in that file there is a check for a valid nonce (to prevent cross-site request forgery (CSRF):
22 | check_admin_referer('wp-dbmanager_manage'); |
That nonce is only displayed on the same admin page.
So the only way for this to exploited normally would be intentionally by an Administrator and considering that Administrators could, for example, normally install code that would already allow them to delete arbitrary files, this wouldn’t really be a vulnerability.
Database Disclosure Vulnerabilities in Absolutely Glamorous Custom Admin, Jazzy Forms, Pods, and Universal Post Manager
Related reports of claimed database disclosure vulnerabilities were released for Absolutely Glamorous Custom Admin, Jazzy Forms, Pods, and Universal Post Manager. While the person behind these reports believes that the file they are listing for each of the plugins is a database backup, in reality they are files that came with the plugins. It hard to understand how they didn’t realize that as the contents are exactly the same for the same plugin file on every website they listed, but they apparently didn’t.