Web factory Ltd’s Sleazy Promotion of Their Security Ninja Plugin
One of things we think is important to understand about why security is in such bad shape these days is due to the poor state of security companies. If you were to comes up with a list of phrases to describe bad companies most security companies would match at least one of those. An example of a security company decidedly acting badly we came across recently is Web factory Ltd. They have website named WP Loop and we recently received a visit to our website from a page on their website entitled “Hacked, dangerous & vulnerable WordPress plugins”.
The page starts by stating:
With over 47 thousand plugins in the official WordPress repository and thousands more available on various other marketplaces and sites, finding those that work well is a daunting task. Finding those that are secure and won’t endanger your site is an even harder task due to the complex nature of WordPress security and often massive plugins with thousands of lines of code.
That is true, hence the value of our service. The next paragraph starts:
Although we can’t help you avoid every single bad plugin, we can pinpoint those who have known, confirmed vulnerabilities and security issues.
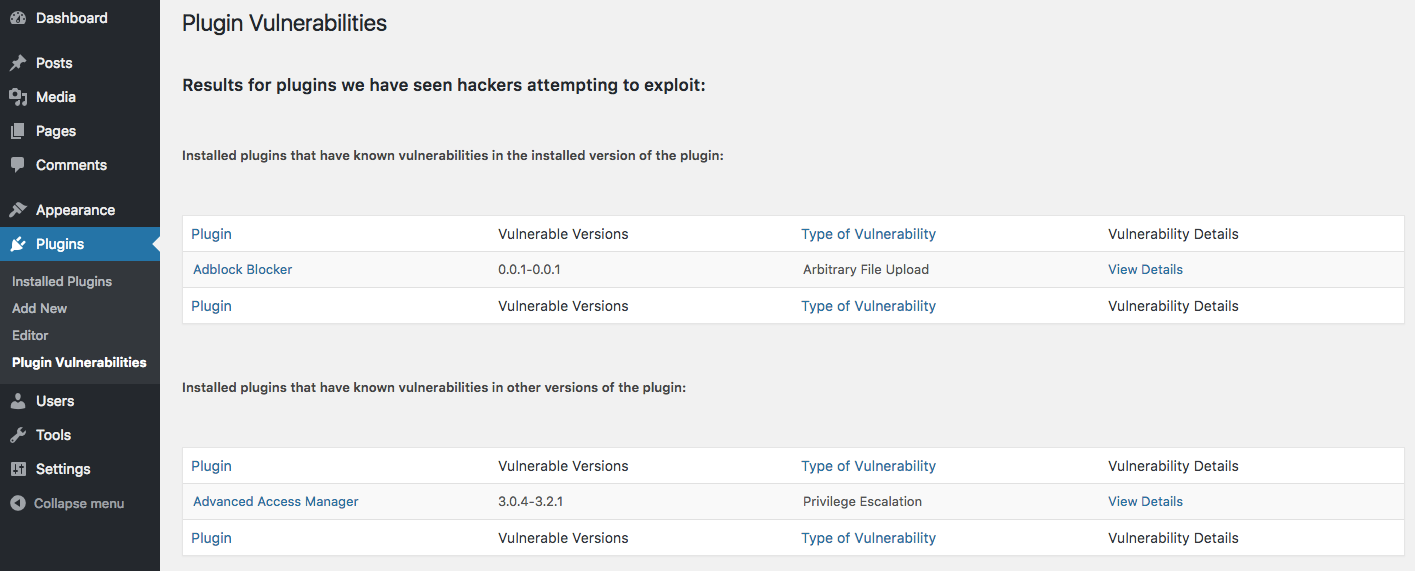
They then go on to provide a list of vulnerabilities that have been in WordPress plugins that you are supposed to check the plugins you use against:
How to use this page and the list of vulnerable plugins?
If you’re using any of the listed plugins, double-check the version number and confirm that it’s the one with known problems. If so – remove the plugin immediately! This includes deactivating it and deleting. Not just deactivating. You can also contact the author and ask him if the problems have been fixed and if not urge him to do so.
That seems really inefficient way to check for vulnerable plugins when there are a number of tools that can do that for you. Then as we started looking over the list what became almost instantly clear is that list consist almost, if not entirely, of data that comes from the free data in Plugin Vulnerabilities plugin. The vulnerable version numbers listed really give it away, since we are the only data source that provides those. So instead of wading through their list you could have just installed the plugin and it would do the same checking for you (when you sign up for the service among other things, you get access to data on more vulnerabilities than just the ones we are seeing hacking attempts against already):
It seemed odd that they clearly knew about our plugin, as the listing comes directly from it, but didn’t tell people just to install it. So why not? Well once you get past the list you get to them promoting their plugin:
Have your WordPress site been hacked?
Don’t despair; it happens to the best of us. It’s tough to give generic advice without having a look at your site, but if you can still login into your WP admin, we suggest installing the free Security Ninja plugin. It’ll perform +40 tests on your site, and with the Core add-on, you can validate the integrity of your core files by comparing them to the secure, master copies stored on WordPress.org. It’s an invaluable tool for any WordPress site!
Worth noting is the fact that they don’t mention that they are in fact the developers of the plugin, which seems relevant when promoting a product. (The plugin also isn’t entirely free, as portion are paid add-ons)
They do gives us a bit of credit on the page, but only as the last listed source, despite most, if not the whole list, being simply taking directly from our plugin:
Sources
The list of latest dangerous and vulnerable WordPress plugins is compiled from various sources including:
Notably they link to our website and not the plugin’s page, which would allow people to see there is a better option for doing the checking and maybe they would also figure out where the data actually came from.
The Opposite of Impossible
They also have a companion blog post that advertises that page, which makes this ridiculous claim:
You can help your WordPress website a lot by installing a free Security Ninja plugin, but you still have to be aware of the plugins you’re using. Until now, it might have been impossible for a regular user to know how to find a bad plugin, but that’s where we step in to help you.
Again they are using our plugin’s data, so they knew that it was possible to do before.
More Misleading Promotion
It turns out this isn’t the end of the misleading promotion of their plugin. On the plugin’s page on the Plugin Directory they have the following section on the Description page:
What others say about the plugin
You can see that they are citing the WP Loop as an “other” despite it being them, the link to “Web smush” redirects to the same page as the WP Loop link.
Security Ninja Doesn’t Prevent a Zero-Day Exploit Attack
On that page they also make a number of bold claims with no supporting evidence to back them up. One that stands out is the claim that the plugin will “prevent 0-day exploit attacks”. A zero-day exploit is an exploit that is being exploited before the developer is aware of it. To be able to prevent those you would need to be able prevent any sort of exploit from succeeding, which is highly unlikely to be possible.
But we did quick check to see if it might prevent one instance that type of thing by we testing to see if the plugin could protect against the same persistent cross-site scripting (XSS) vulnerability we had tested a number of other security plugins against earlier this week. The vulnerability could have been a zero-day, as a hacker appears to have been looking for usage of the plugin when the vulnerability was in the plugin and it looks the type of vulnerability that hackers would target. Of the 11 security plugins we tested it against originally, only two provided any protection, and for those two we easily found a way to bypass the protection. The result for Security Ninja is that it did not prevent exploitation of the vulnerability.