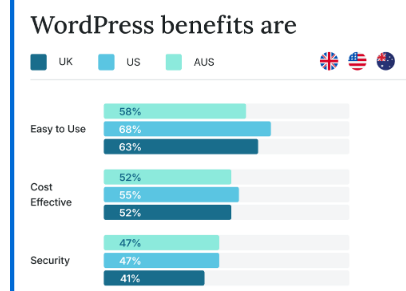
WordPress Firewall Plugin Claimed to Protect Against “Any Threat” Doesn’t Stop Even One Simulated Attack From Firewall Testing Tool
Starting late last year, there has been a significant increase in the number of plugins being submitted to the WordPress Plugin Directory. That appears to be largely caused by the ease of AI to generate WordPress plugins and not growth of WordPress ecosystem. That has multiple implications for the security of WordPress websites. One is that yet more security plugins making great promises as to the protection they offer, while not delivering on it. Or even introducing additional security risk.
Considering that AI builds things based on existing code, you would likely also see that these plugins would be focused on common security features already known to offer limited to no security value. While we can’t say which new security plugins are generated by AI, we can say that new security plugins that could have been generated by AI are providing useless protection. Both WPS Protect: Login URL & Security Headers, which was released last week, and Iron Security, which was released in March, claim to offer additional protection by adding the security header X-XSS-Protection to websites. That clearly isn’t going to offer protection considering that no web browsers support that header anymore: [Read more]