Without Us Vulnerable Plugins Would Remain in the WordPress.org Plugin Directory
A couple of the important things we do when it comes to vulnerabilities in WordPress plugins came together the other day, providing an example of what happens if we were not doing it. One of the ways we keep track of what plugin vulnerabilities are out there is to monitor our websites apparent hacker activity. Through that we came across a request for the readme.txt for several plugins, including the plugin Gallery Objects, that we didn’t have installed. That type of request is usually an indication that hackers are probing for usage of the plugins before attempting to exploit something in it.
While trying to figure out what the vulnerability the hacker might be targeting in the plugins, we thought there might be some connection between the vulnerabilities in all of them. After spotting what looked to be a SQL injection vulnerabilities in several of them, we took a look at the others to see if they might contain them as well. When we got to Gallery Objects we easily found one. After we had done that, we did a check to see if there were any other vulnerabilities that had previously been disclosed in the plugin and found that the same SQL injection vulnerability we found had already been disclosed in July of 2014, which was before we started collecting data for our service (so our data for that time period is more limited than it is for newer vulnerabilities).
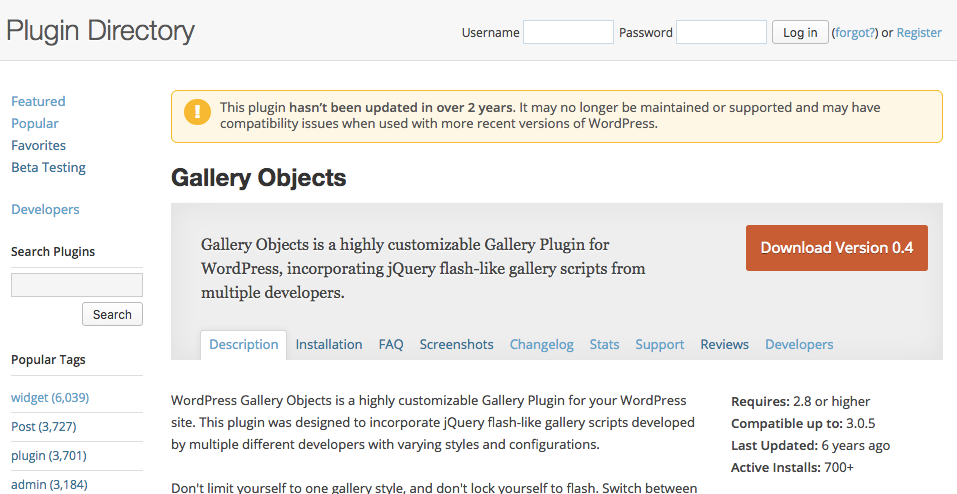
When we come across a disclosed vulnerability that exists in the current version plugin we usually notify the developer (unless they appear to be long gone) and if they don’t respond or we didn’t notify them first, we notify the wordpress.org Plugin Directory. At that point, unless it is really minor vulnerability, they will pull the plugin pending a fix. If anyone else had been doing the same at the time this vulnerability was disclosed the plugin shouldn’t currently be in the Plugin Directory, but it still was there as of the other day:
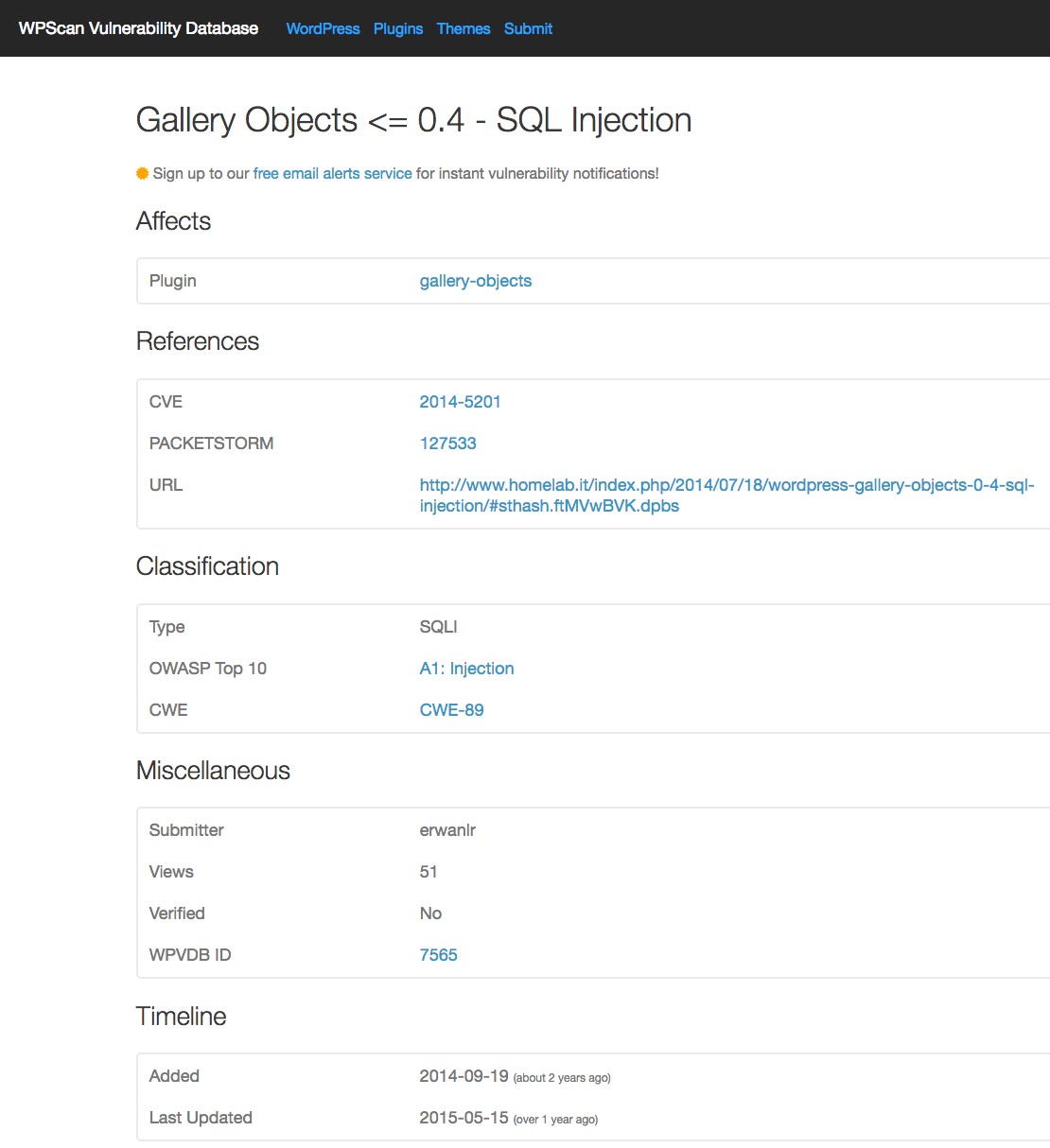
After we notified the Plugin Directory the plugin was removed within half an hour, further confirming that no one had previously notified them. It isn’t that others didn’t know, for example the WPScan Vulnerability has had the vulnerability in their data for over year:
But they must have never bothered to notify the Plugin Directory, which would have lead to the plugin being being removed and protected anyone who would have otherwise installed that known vulnerable plugin (we give them credit for having the vulnerability in their data before us, though).