Sucuri and Others in Security Community Vastly Overstate Threat of WordPress Plugin Vulnerability
When it comes to dealing with web security, one of the big problems we see if that people don’t have a good understanding of what the risk of various threats are, often that seems to be due to security companies and others in the community. At its worst security companies are peddling false threats, but with real threats often seem more interested in driving up fear instead of providing accurate information. A good example comes from a vulnerability the web security Sucuri recently found, which in reality is almost no threat to the average website. But Sucuri and others would lead you to believe otherwise.
It Is an Authenticated Vulnerability
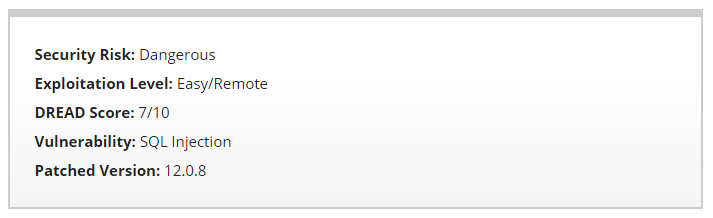
The problems start with the title of Sucuri’s post “SQL Injection Vulnerability in WP Statistics“, which isn’t accurate as the vulnerability is in fact an authenticated SQL injection vulnerability. That makes a big difference since the vast majority of WordPress websites don’t allow untrusted individual access to accounts, so only a small portion of those using the plugin could have been vulnerable.
That is particularly important when there is incorrect emphasis on how many are using a plugin when considering the threat of a vulnerability. That can be seen in some of the top tweets for this particular vulnerability:
This is a big issue. WP Statistics is one of the most popular WordPress plugins https://t.co/CjS9lUMZxT #WordPress #SQL pic.twitter.com/brPDXXEXeW
— Catalin Cimpanu (@campuscodi) June 30, 2017
SQL Injection flaw in WordPress Plugin WP Statistics potentially exposed 300,000+ Sites https://t.co/NNb3b8Pil2 #security pic.twitter.com/kpi9MI4fwg
— Eric Vanderburg (@evanderburg) July 1, 2017
#SQLInjection flaw in #WordPress Plugin WPStatistics potentially exposed 300,000+ Siteshttps://t.co/bbUGpTX5kM#securityaffairs #hacking
— Security Affairs (@securityaffairs) July 1, 2017
Do you use the #WordPress plugin #WPStatistics? Update that plugin now! /via @thehackersnews https://t.co/ATQ7d5PQpO #infosec
— Avira (@Avira) July 1, 2017
Oh shit there goes the weekend.
WordPress plugin WP Statistics has a SQL Injection vulnerability.
Over 300,000 websites are vulnerable https://t.co/y0yfHb8uZ7
— Victor Gevers (@0xDUDE) June 30, 2017
Popularity Isn’t a Major Factor in What Vulnerabilities Get Exploited
The focus on the amount of installs was also emphasized by Sucuri, they even bolded the amount installs in their post:
While working on the WordPress plugin WP Statistics, we discovered a SQL Injection vulnerability. This plugin is currently installed on 300,000+ websites.
Unlike Sucuri we do monitoring to try to catch zero-day vulnerabilities in WordPress plugin (vulnerabilities that hackers are exploiting before the developer is aware of them), so we are aware of what vulnerabilities are actually being targeted. SQL injection vulnerabilities in general are not a common target and what could be done with this vulnerability is something we just don’t see hackers targeting against the average website. It could used in a targeted attack, but very few website are targeted, so the there is little risk from this vulnerability.
The reasons for this are not that complicated to understand. Hackers are generally looking to gain access to as many websites as possible, so they have interest is easy to exploit vulnerabilities and don’t have an interest in gaining access to a particular website. With this vulnerability someone could slowly read out the contents of the database, which alone won’t grant access to the website, since WordPress passwords are not stored in the database. Instead a hash of the passwords is stored in it, which a hacker would then need to crack to gain access.
Sucuri doesn’t come close to accurately reflected threat. Their rating way overblown:
Then in the section on if you are at risk is quite bad:
Are You at Risk?
This vulnerability is caused by the lack of sanitization in user provided data. An attacker with at least a subscriber account could leak sensitive data and under the right circumstances/configurations compromise your WordPress installation.
If you have a vulnerable version installed and your site allows user registration, you are definitely at risk.
That second sentence seems to be written in a way that while it is accurate, way overplays things. The reality is you are only at risk if you “have a vulnerable version installed and your site allows user registration”, but even then you wouldn’t be likely have the vulnerability exploited.
There isn’t any requirement that a security company overstate the threat of a vulnerability, we disclosed a vulnerability in this plugin back in April without having to go that route.
The popularity of a plugin matters so little that we see hacker trying to exploit vulnerabilities in plugins with less 100+ active installs. One of those attempts that we looked at explain part of why that is, hackers don’t even bother testing out vulnerabilities before exploiting them, so there is a good chance they don’t even know how many websites are using them. If you see someone making a big deal of the threat based on amount installs, that is good indication they don’t know what they are talking about or they are intentionally misleading.
Telling People to Update a Particular Plugin is a Bad Idea
In looking at the tweets there was big emphasis on needing to update the plugin, which is bad. It isn’t bad to update the plugin, but you really need to be keeping all of your plugins up to date at all times. As you often will not know if a new version of a plugin is a security update. For example, just last week when a security vulnerability in a security plugin we discovered was fixed the changelog entry for that was “bugfix”. That isn’t an outlier, as in 2015 we found that in a fifth of fixed vulnerabilities in WordPress plugins were not mentioned in the changelogs.