The Limited Capability of Existing Plugins for Checking the Security of Plugins
As we have been looking at what more we can do with our new tool for doing security checks of WordPress plugins, one of things we have been looking at is what existing tools are out there that provide similar functionality. In doing that we found a couple of plugins that do security checks of other plugins, though their capability is rather limited.
WP Plugin Security Check
The first plugin is WP Plugin Security Check, which was last updated seven years ago. The plugin is described as:
WP Plugin Security Check checks plugins for bad practices and possible security holes limiting the risk of a compromised WordPress installation to a ‘hate to say I told you so’.
The description doesn’t spell out what types of things are looked for. In looking at the underlying code we found it checks for three items:
- Usage of the variable $_SERVER[‘REQUEST_URI’]
- Usage of the function eval()
- Usage of variable functions
Warning about usage of eval() seems reasonable enough as the documentation for that states:
The eval() language construct is very dangerous because it allows execution of arbitrary PHP code. Its use thus is discouraged. If you have carefully verified that there is no other option than to use this construct, pay special attention not to pass any user provided data into it without properly validating it beforehand.
Though the tool just checks for its usage, not say if the usage might be exploitable.
Variable functions could potentially allow arbitrary PHP functions to be executed, though we can’t recall coming across them with any vulnerable or intentionally malicious code, so we are not sure if that would be of much use to check for.
The check for use of $_SERVER[‘REQUEST_URI’] is rather odd as that variable just provides with the address of the page being requested. That does include user input, so it does need to be properly handled (though as we noted before, the value is usually encoded, limiting issues that can come from improper use of it), but what the “bad practices and possible security holes” involved with that are is something we can’t think of. That variable is used in many of the most popular plugins, so it would cause a lot of those plugins to be flagged for a reason that isn’t clear to us.
Plugin Inspector
The second one is Plugin Inspector, which was last updated 12 months ago. The plugin is described as:
The Plugin Inspector plugin is an easy way to check plugins installed on your WordPress and make sure that plugins do not use deprecated WordPress functions and some unsafe functions like eval, base64_decode, system, exec, etc. Some of those functions may be used to load malicious code (malware) from the external source directly to the site or WordPress database.
Some of the functions it checks for usage of seem like they could accurately be described as being unsafe, as was already mentioned with eval(), but others seem more problematic as they just are functions that make requests to other websites.
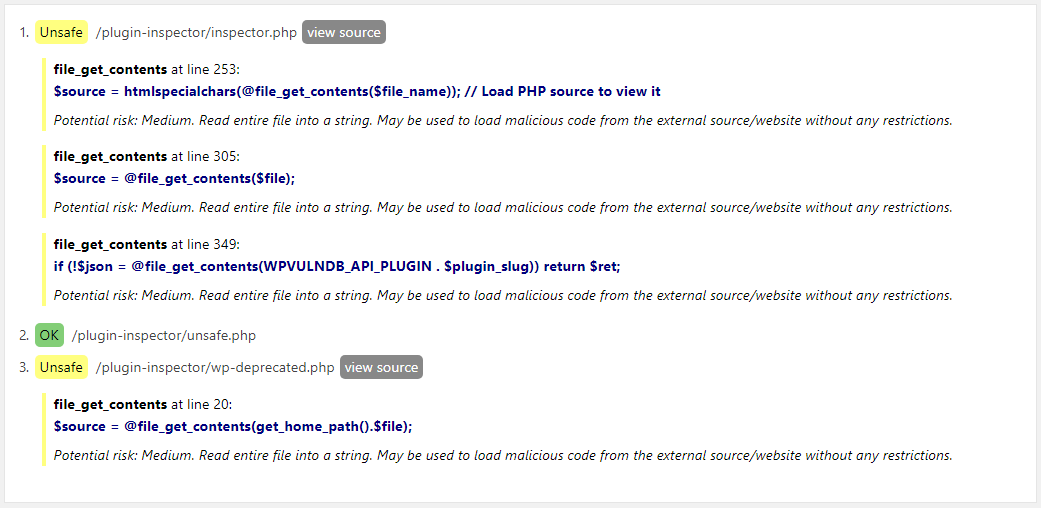
The problems with its usage can probably be best seen by the result when the plugin scans itself and the developer’s response to that result. Here is the result when the plugin is scanned by itself:
When the developer of the plugin was asked about this they responded:
What is the question? This is just a warning, not an issue.
You can ignore all Unsafe messages if you trust the author and the source of this plugin.
Just because you trust the author and the source of the plugin, it doesn’t mean the plugin is safe.
There is also the issue that the checks are rather simply done. As an example of this, in one of the screenshots provided for the plugin you can see that a line of code that uses a function to making a request to another website, the plugin states that it could “load data from any external server”:
Since a variable is used, you can’t tell just by the line what websites or website requests might be through it. But below that in the screenshot is another line with the same message despite the code in that line making a request for a specific web address:
This tool does seem useful for someone with some level of expertise that wanted to have a better understanding of what a plugin might do, but for others it seems the checks are of limited value.