More Evidence That the Data in the WPScan Vulnerability Database Isn’t All That Reliable
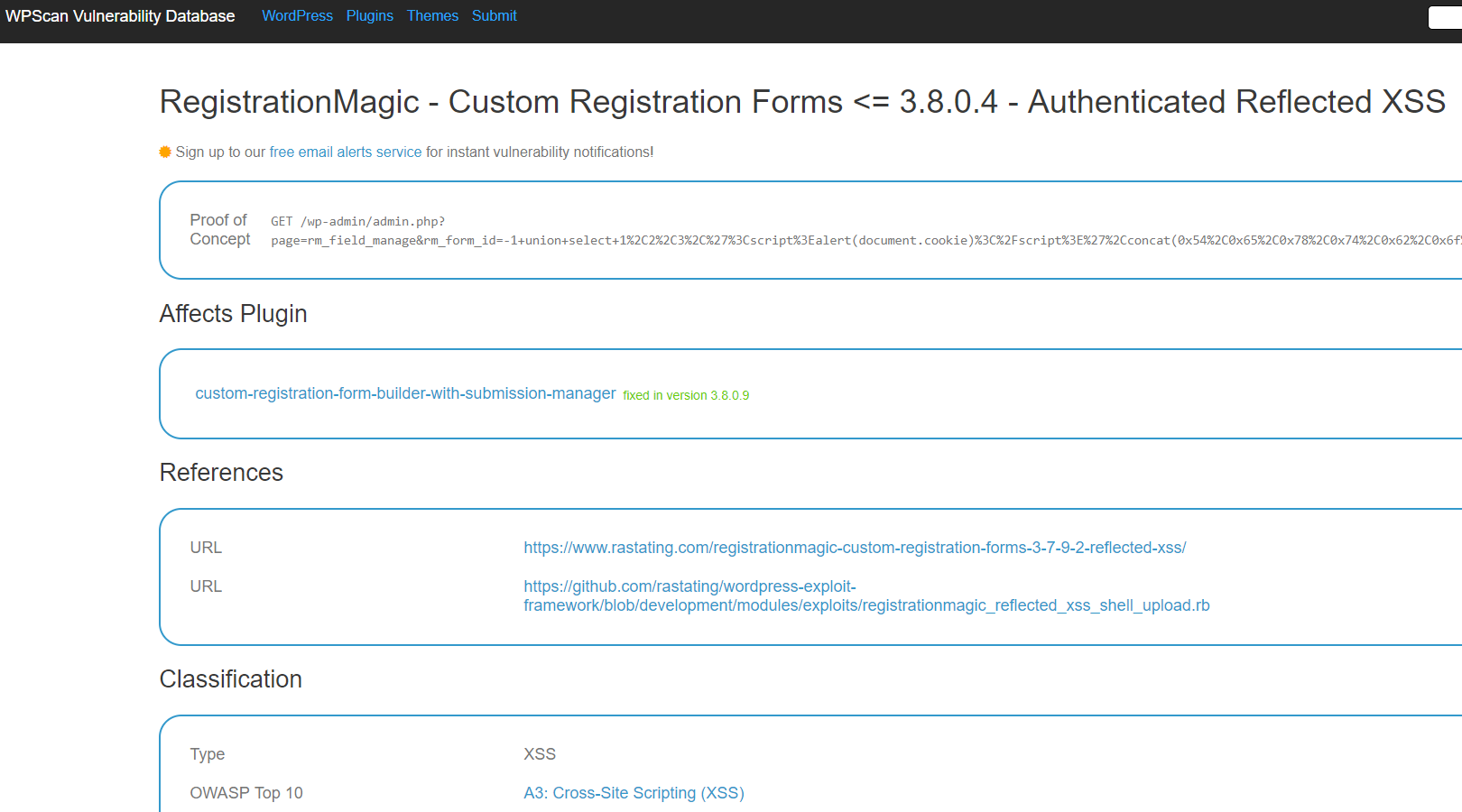
Yesterday we noted how the WPScan Vulnerability Database had incorrectly labeled a reflected cross-site scripting vulnerability discovered by Robb Carr in the plugin RegistrationMagic as having been fixed. While it would have been easy to check the proof of concept provided with the report on the vulnerability and see that the vulnerability still existed, as we did, they pretty clearly didn’t. That lack of testing is a big issue, since if you are relying on their data, you really need to test out any vulnerabilities in the plugins you use to make sure they truly have been fixed (or just use service that test vulnerabilities when adding them to their data set, of which we seem to be the only one that exists).
Looking at the entry for that in their database today, they have changed the entry to indicate that the vulnerability has been fixed as of the version released after we notified the developer of the issue:
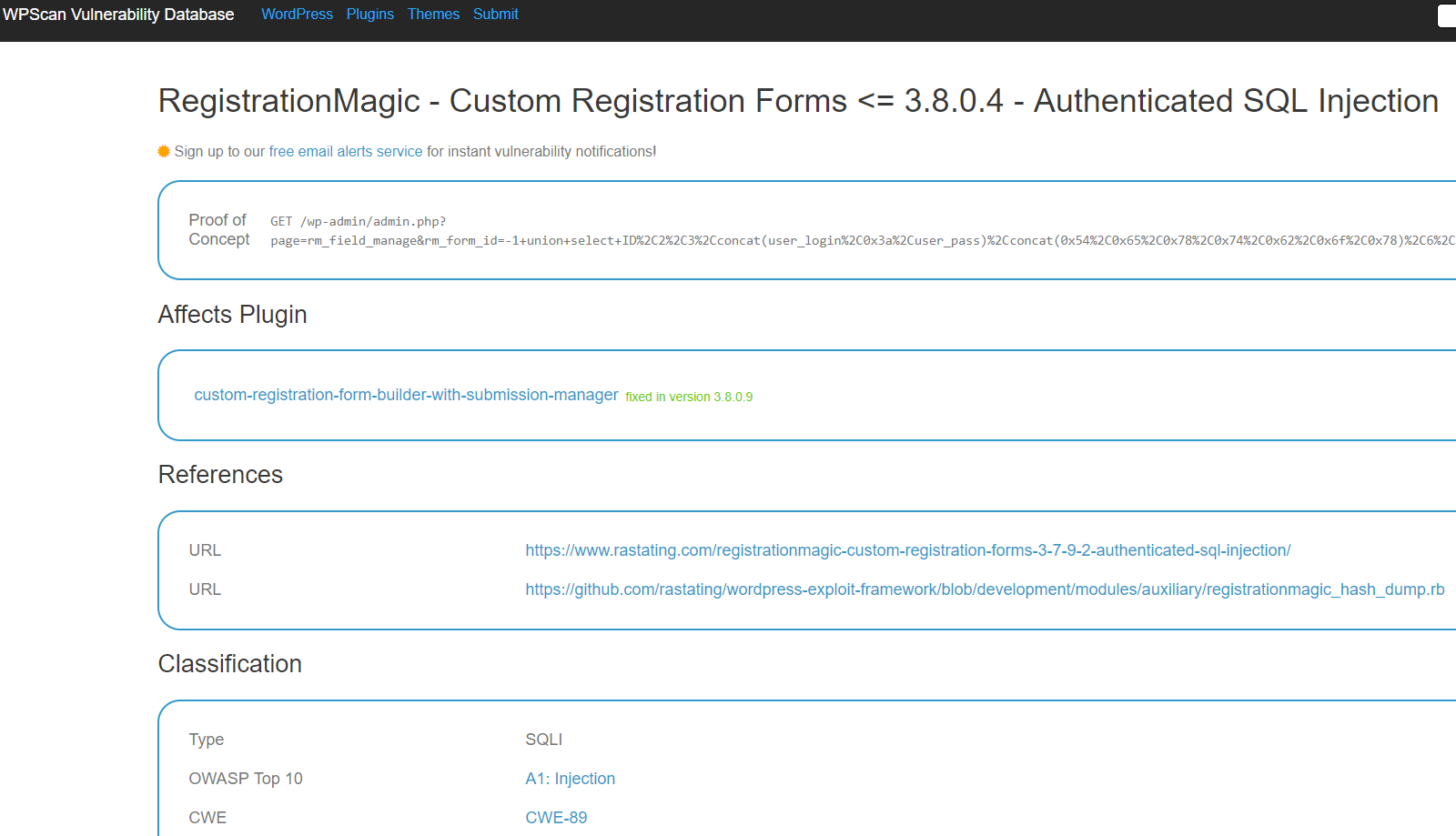
They also changed the entry for a related claimed authenticated SQL injection vulnerability in the plugin to indicate it was fixed in that version as well:
That seems to be incorrect and an indication that they still didn’t bother to test things out.
As was mentioned in our previous post, we wouldn’t consider what was claimed to be vulnerability there to be a vulnerability, as the issue could only be exploited by Administrators, who normally would be able to do the equivalent of this (or to change a plugin to remove security code). But if you consider it a vulnerability, then it looks to us that it was fixed in the version that WPScan previously listed it as having been fixed in. As with the other vulnerability this would be easy to test out. All that they would have needed to do that would be to install version 3.7.9.2 and visit the proof of concept URL and see that it worked, then switch to version 3.7.9.3 and see that it didn’t work. Looking at the underlying code, it looks like that version 3.7.9.3 fixed it as well.