The Failure to Update Vulnerable Plugin is Reminder of Security Industry’s Apparent Lack of Interest in Making Sure Websites Are Secure
Something we have recently been thinking might be a helpful way to explain why security is in such bad shape despite the amount of money being spent on it, is to think of the security industry not as the “security industry” but as the “insecurity industry”. By that we mean that most of the security industry seems to not be focused not trying to make things secure, but on selling people on the idea that insecurity is very much the natural state of things, that you are under constant attack, and that while they can offer you the best security, you shouldn’t expect that the protection provide by that is actually all that effective.
As an example of that, take something from Wordfence recently, where they seem be describing a situation where some web hosts had failed at doing a basic of security for their service and allowed customers to access to other customers’ files. Not only is that a failure at a basic level for a web host, what they seem to be describing is something that was huge issue with web hosts a number of years ago, so there would be even less excuse for that still happening in 2018. To Wordfence though the situation was very different:
It’s important to note that vulnerabilities are a fact of life in any service, system or software. Finding, confidentially disclosing and fixing vulnerabilities is how industry works with the information security community to improve the products and services we use and keep the public safe. The process that we use is well established and is widely used by organizations that include Google’s “Project Zero” and Cisco’s “Talos” security group.
When vulnerabilities are found and vendors are responsive, you benefit as a customer of those vendors and can know that your vendor reacts quickly to fix security problems and will likely do so long term, keeping you and your data safe.
A disclosure like this is not an opportunity for “vendor shaming” or a witch hunt. All developers who write enough code write vulnerabilities at some point in their career. It is in fact a moment to celebrate responsive vendors and a well handled incident that left customers and the online community safer.
At Wordfence, we are excited when a vendor works closely with us to fix a vulnerability and responsive vendors garner the greatest respect from our engineering team.
If you read over the whole post and the comments it seems pretty clear that Wordfence doesn’t even know what the underlying cause of the issue was, so the idea they worked closely with the web hosts to fix it seems to be something we see fairly common with them, a hyperbolic statement overstating what they are doing.
What makes this worse is that it is likely that Wordfence’s keeping quiet on this allowed the problem to fester when if it had publicly disclosed promptly there would have been more pressure on the web hosts to promptly fix this. By not doing that there was an upside for Wordfence though, as they could get more people to pay them to clean websites, when the web host really should have been handling cleaning them up since they caused the problem in the first place. You also have to wonder about Wordfence not seeming to understand that disclosing something is being exploited already is not the same as discovering something that hackers don’t appear to know off yet, where a limited delay of disclosure can make a lot more sense.
Also notable, one of the comments doesn’t paint such a great picture of Wordfence’s handling of this:
My client got hacked several times on Hostway and neither Hostway or Wordfence’s cleaning team figured out this was the issue at the time. We changed hosting providers and have been safe ever since. I’m glad you found this both to validate my diagnosis that the weak link was Hostway and so that Hostway’s customers will now be safer.
60 Percent Insecure
If we are wrong about this and the most of the security industry is in fact concerned about security, they don’t seem to be acting in a way that matches that. To show how even the basics of security are still failing to happen, while security companies don’t seem to acting as if there is a crisis and instead trying to sell people on more advanced solutions (for which there is little to no evidence are actually more effective or effective at all) takes something we just ran across.
Several days ago we had a request at one of our other websites for a file that would be located at /wp-content/plugins/smart-google-code-inserter/smartgooglecode.php, which is a file from the plugin Smart Google Code Inserter. That was likely a request probing for usage of that plugin before trying to exploit a vulnerability in it. After noticing that we went to try to figure out what a hacker might be interested in trying to exploit in the plugin.
In looking over the current version we didn’t see anything that looked like it might be targeted by a hacker.
On January 1 Benjamin Lim had disclosed a persistent cross-site scripting (XSS) and a SQL injection vulnerability had existed in earlier versions of the plugin. The persistent cross-site scripting XSS vulnerability seems like it could be something that a hacker might be interested in since that would allow a hacker to get malicious code to be served up on the frontend pages of vulnerable websites and just that type of issue has been something that has been exploited before.
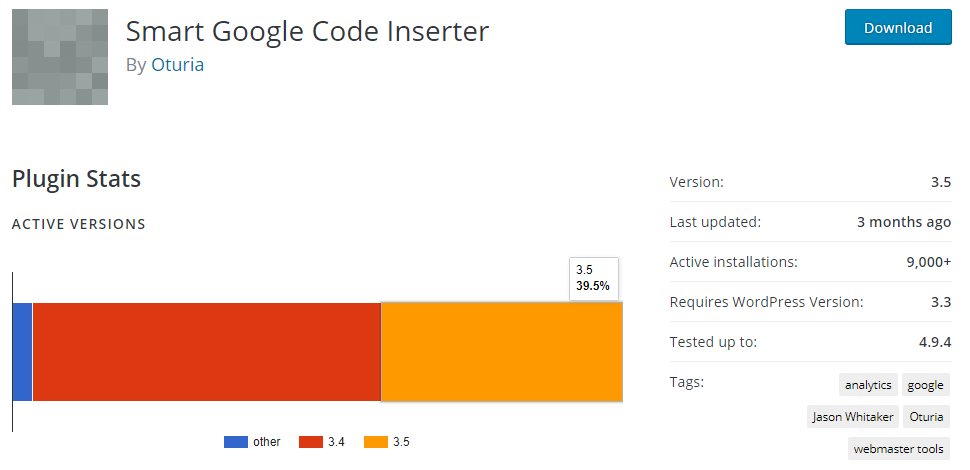
Those vulnerabilities were fixed on November 29, so if people were doing the security basic step of keeping software up to date, attempts to exploit this shouldn’t be of much concern since it shouldn’t impact many of the 9,000+ active installations of the plugin (according to wordpress.org). Unfortunately, if the wordpress.org data is accurate, about 60 percent of the installs of this plugin are still not using the fixed version, 3.5:
The Wrong Focus
To bring this back around to Wordfence, also in November, we wrote about how their behavior relates to just this issue:
When it comes to improving the poor state of security, what can be seen over and over is that the focus needs to be on the basics. Take for instance the widely covered breach of Equifax, which was a situation where simply keeping their software up to date would have prevented the breach from happening. But the security industry isn’t focused on that and doesn’t seem to ever consider that what they are doing is far too often part of the problem, even when it impacts them.
That type of issue applies with WordPress plugins, where many hacks involve exploitation of vulnerabilities that have already been fixed. So what is probably going to provide you better protection then any security product or service would be to simply keep your plugins update at all times (many of the security plugins don’t seem to provide any protection against those vulnerabilities), which can be done with things like our Automatic Plugin Updates plugin. But telling you that doesn’t help the security industry to sell their products and services, so you don’t often here that from them.
As example let’s take a look at a post from yesterday from Wordfence about vulnerabilities in several plugins, which ends:
We encourage you to share these vulnerabilities with the larger WordPress community to help keep site owners safe from exploitation.
If you read through the rest of the post they don’t ever say that you should be keeping your plugins up to date at all times, which is actually the best advice when it comes to the vulnerabilities mentioned there. Instead they tell you the plugins they are mentioning now should be updated “immediately”, which for one of the plugins is well after a hacker had started trying to exploit one of the vulnerabilities that had been in it. The three plugins they mention are far from the only recent updated plugins that had updates that fixed security vulnerabilities, so only mentioning that people should update those isn’t all that helpful.
The rest of the post is like so much from Wordfence, mainly an ad for their services, which seems to be the real reason they want people to share it. As well get to in a moment one of the vulnerabilities in the plugins they mention is an example of the poor quality of what Wordfence paid service provides over doing the basics and the post shows again that Wordfence has very limited security knowledge, despite claims to the contrary.
A couple weeks later we wrote something along the same lines involving another well known name in WordPress security, Sucuri.
To see another indication of the lack of understanding of the important of keeping software up to date at all times from the security industry, checkout a comment from another posts of ours from someone that describes themselves as a “Web application security and accessibility evangelist.”
By comparison, well before we ever created this service, we had introduced the aforementioned Automatic Plugin Updates plugin, which turns on WordPress’ abiltiy to automatically update plugins.