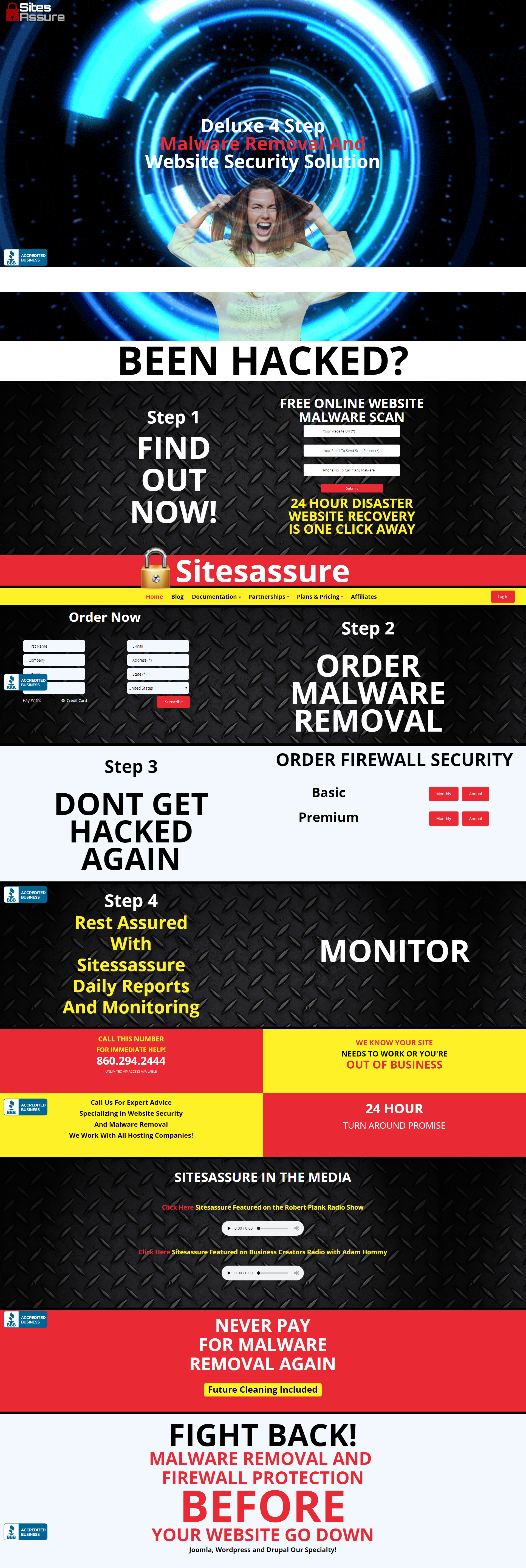
When A Security Vulnerability Is Only One of the Issues With a WordPress Security Plugin
We don’t think too highly of the security industry and we are often reminded of why that is, as was the case when we did a quick check of the plugin Sitesassure WP Malware Scanner. We had run across the plugin on the website of a company, 911websiterepair.com, which offers to clean up hacked websites, where it was listed as their plugin. The plugin didn’t mention anything about that website instead it was connected to another website and the look of that website didn’t exactly give us a good feeling about the potential quality of the plugin:
We then did a quick check of the plugin. What we found was poor security and a minor security vulnerability in the plugin. We will get to those in a moment, but first we want to bring up a couple of questionable items.
In looking over the code one thing that we quickly noticed was that there was a significant amount of code in the plugin for accessing a scanner from a company named Quttera. Oddly, nowhere in the description of the plugin or in the plugin is there any mention of that company. As far as we can tell that is actually who is doing the scanning. Considering that Quttera provides their own plugin (which we also recently found contained a vulnerability) it looks like Sitesassure’s plugin mainly serves as advertisement for them and to collect information on people using it, rather than providing a capability that isn’t available elsewhere.
As to the data collection, when you take various actions not only does the plugin connect to the Sitesassure website but it also sends out an email to someone. That seems like it might be a violation of one of the developer guidelines for WordPress plugins, but what seems odder is that the current email address doesn’t have an obvious connection with the plugin. As an example of that is the code run when the plugin is deactivated:
function swms_sitesassureDeactivate() { $site_domain = get_bloginfo('url'); $req_url = SWMS_REQUEST_URL; $response = wp_remote_post( $req_url, array( 'method' => 'POST', 'timeout' => 45, 'redirection' => 5, 'httpversion' => '1.0', 'blocking' =>; true, 'headers' => array(), 'body' => array("action" => SWMS_UPDATE_REQUEST, 'domain' => $site_domain, "status" => SWMS_INACTIVE_STATUS), 'cookies' => array() ) ); if ( is_wp_error( $response ) ) { $error_message = $response->get_error_message(); _e("Something went wrong: $error_message","swms"); } else { if($response['response']['code'] == 200 && $response['response']['message'] == "OK") { $message = 'Hi SA Admin, '.$site_domain.' is deactivated the WPSASCANNER plugin'; swms_sendEmail(array('to' => 'nagaraj@spinzsoft.com','subject' => $site_domain.' Deactivated Message','message' => $message)); } } |
That code first sends a request to the Sitesassure website and if that request is successful an email is sent to nagaraj@spinzsoft.com. The website at spinzsoft.com doesn’t seem to be connected to the Sitesassure website. Up until June 13, when version 2.0 of the plugin was released, emails were instead sent to support@sitesassure.com. Prior to release of 2.0, the last update made to the plugin was in December of 2015.
One common area of security issues in plugins is functionality accessed through WordPress’ AJAX functionality. Often due to allowing those not logged in to WordPress to access functionality only intended for those logged in or due to allowing low level users access to functionality they are not intended to have access to. In the case of this plugin both of those issues occur.
In one of the functions that is accessible to anyone logged in WordPress despite only being intended to be accessed by Administrators there was a security issue not related to allowing lower level users to access it. Instead the issue was that user input is output without being sanitized or escaped, which could allow reflected cross-site scripting (XSS) to occur. That occurred in the function swms_get_admin_url(), which is located in the file /sitesassure-wp-malware-scanner.php:
494 495 496 497 498 499 | function swms_get_admin_url(){ $swms_scanned_url = $_POST['data']; $swms_admin_url = admin_url("admin.php?page=swms_scanner_report_page&swms_url=$swms_scanned_url"); echo $swms_admin_url; exit; } |
Two days after we notified the developer of the issue a change was to fix it, but the version number was not changed, so no one already using version 2.0 will be prompted to update. We had also notified of the developer of the more general lack of security in the plugin, lack of restriction on who can access AJAX accessible functions and lack of protection against cross-site request forgery (CSRF), but no changes have been made related to those yet. We have yet to receive any response from the developer.
The vulnerability was fixed by passing the user input through the esc_url() function:
494 495 496 497 498 499 500 | function swms_get_admin_url(){ $swms_scanned_url = $_POST['data']; $swms_scanned_url = esc_url($swms_scanned_url); $swms_admin_url = admin_url("admin.php?page=swms_scanner_report_page&swms_url=$swms_scanned_url"); echo $swms_admin_url; exit; } |
Proof of Concept
The following proof of concept will cause any available cookies to be shown in alert box, when logged in to WordPress. Major web browsers other than Firefox provide XSS filtering, so this proof of concept will not work in those web browsers.
Make sure to replace “[path to WordPress]” with the location of WordPress.
<html> <body> <form action="http://[path to WordPress]/wp-admin/admin-ajax.php?action=swms_get_admin_url" method="POST"> <input type="hidden" name="data" value="<script>alert(document.cookie);</script>" /> <input type="submit" value="Submit" /> </form> </body>
Timeline
- June 25, 2018 – Developer notified.
- June 27, 2018 – Change made to version 2.0 to fix vulnerability.