The WPScan Vulnerability Database Is Missing a Lot of New Vulnerabilities
If you are looking for data on vulnerabilities in WordPress plugins you appear to have a lot of options, but in reality many sources actually just reuse data from the same source, the WPScan Vulnerability Database. The true source of the data is often is not disclosed by the provider. Even when they are upfront about that, we have yet to see a provider that is also upfront about the major limitations of that data source. Sometimes things are worse, whether it is Wordfence (aka Defiant) falesly and baselessly claiming that the data is “official” and “Confirmed/Validated” or MainWP stating that “The Vulnerability database updates itself real-time so you don’t miss out on any vulnerabilities”. Updating in real-time wouldn’t mean that you wouldn’t miss out on any vulnerabilities since that would depend on the breadth of the data, not on how fast changes are applied. In reality you will actually miss out on many vulnerabilities.
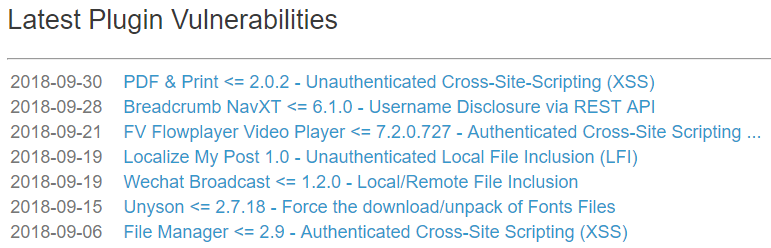
As reminder of the actual quality of their data, take a look at their current listing of the latest plugin vulnerabilities in their data set:
Out of those seven entries, one of them is labeled as the wrong type of vulnerability as we noted earlier this week and another really isn’t a vulnerability as we will be mentioning tomorrow in our weekly post on claimed vulnerabilities that are not really vulnerabilities.
What seems more important is the many vulnerabilities missing that have been publicly disclosed since the 6th. Since then for example we have disclosed ten vulnerabilities, among them a vulnerability of type likely to be exploited that we caught when it was added into the plugin. That type of vulnerability in a plugin with 9,000+ active installations, according to wordpress.org, seems like the kind of thing that would be important to include in such a data set. If you want to look at popularity instead of severity, last Tuesday we disclosed a minor vulnerability that was in a plugin with 700,000+ active installations.
Considering that we are a large discoverer of vulnerabilities missing all of ours seems like a good indication of the poor quality of their data, so it wouldn’t be surprising that vulnerabilities that others disclosed are also missing. Among those is a vulnerability that was disclosed in a plugin with 10,000+ active installations that was claimed to already being exploited (though we doubt that it was). At the time it was disclosed it hadn’t been fixed, so if it had really been being exploited that seems like something that people relying on their data would have wanted to know, but wouldn’t have.
By comparison we have added all of our own vulnerabilities (obviously) and quite a few others that are missing from their data set to the data set used for our service since the 6th.