A Hacker Is Looking For the Less Than 10 Websites Running a Vulnerable WordPress Plugin
One of the many ways that security companies try to sell people on using poor to useless security services is by selling people on the idea that their websites are under constant attack. They then promote their service as being a solution, but don’t actually present any evidence that there services are actually effective at protecting websites (and there is plenty of evidence that they are not effective). The reality is while there is in fact a pretty constant stream of hacking attempts, that is quite meaningless since the success rate is incredibly small. If these security companies actually knew and then told people how many successful attacks there were it would make people a lot less likely to purchase these types of services without evidence they can work well against the real threats. That in turn would likely improve security for everyone because of the work needed to provide effective services is likely to lead to catching and fixing issues sooner, which would in turn lessen the need for such services (it is unclear to us if these companies are doing things poorly intentionally to avoid that or not).
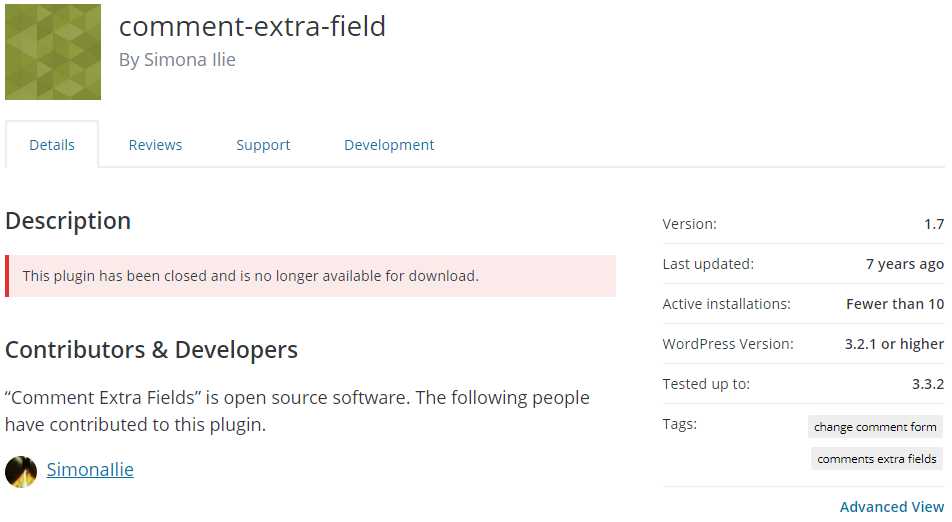
As an example of why the success rate is so small, a few days ago we had a request to this website probing for usage of the plugin Comment Extra Fields by way of a request for the readme.txt file in the directory the plugin would exist in if we had it installed. According to wordpress.org that plugin “has less than 10” active installations:
Our guess is the hacker would be looking to exploit an arbitrary file upload vulnerability that was disclosed by Sammy FORGIT over six years ago. That vulnerability is in the latest version of the plugin, but a hacker would likely have a hard time finding one of those less than 10 websites to exploit. Based on everything we have seen it looks like a lot of hackers are not aware of the ease that you can check how much usage WordPress plugins have and avoid wasting their time on something like this. Part of what gives that credence is that plenty of the attacks they launch on those unpopular plugins are done in way that have no chance of success and would indicate that no due diligence was done (which is good thing since it means less websites being hacked).
While in this case it looks like a hacker was checking if the plugin was installed first, we see many attempts were hackers skip past that step and just try exploiting a vulnerability in plugins that are used on almost no websites. That is the kind of thing that security companies likely would include in their stats, even if it is largely meaningless, especially when the attacks would never succeed even if a website was using a vulnerable version of the plugin.