WPScan Vulnerability Database Weeks Behind in Warning About Exploited Vulnerability in WordPress Plugin
On Friday we noted that during the month of November we not only added many more new vulnerabilities in WordPress plugins to our data set than the widely used WPScan Vulnerability Database (50 to 11), but we actually disclosed more vulnerabilities ourselves than they added in total during the month (21 to 11). Considering that all the vulnerabilities we discover are publicly disclosed and you can even access a RSS feed just of them, it doesn’t speak highly of the quality of their data set to be missing them.
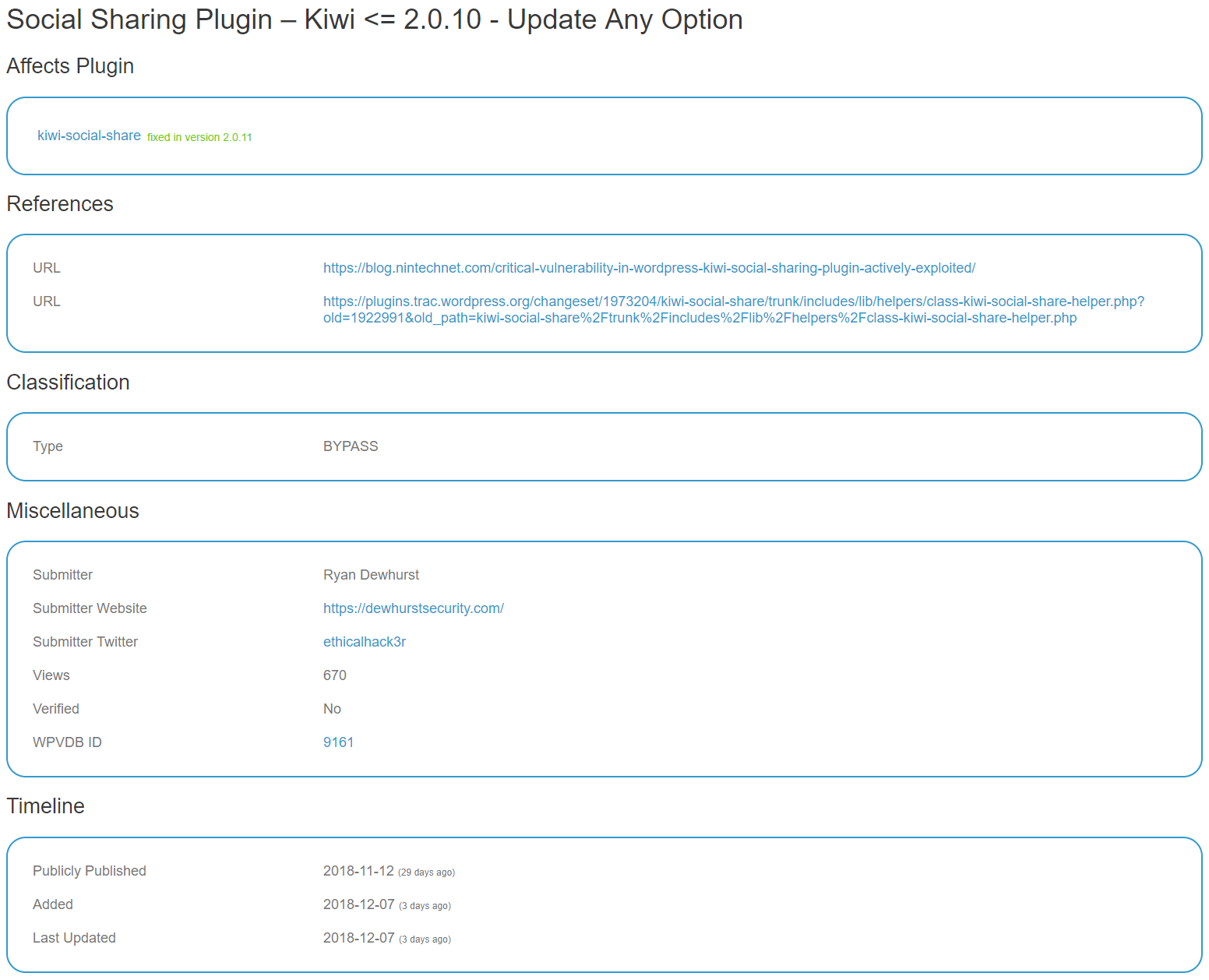
The handling of one of the vulnerabilities we disclosed is of particular concern for anyone relying on their data, as it was an option update vulnerability we disclosed on November 12 that looks to have been on hackers’ radar by at least November 15. It was only added to WPScan’s data on the December 7th:
That kind of thing has wider repercussions as you have people that unknowingly rely on their data in deciding whether to update plugins and wouldn’t even know about the limits of their data since they are not being properly warned about by companies reusing the data (it gets as worse as one company not warning their customers about the quality of the data actually goes further by lying and claiming that the WPScan data is “confirmed/validated” when it explicitly isn’t).
Also noticeable in that listing is that they fail to credit us, which isn’t a one off issue.
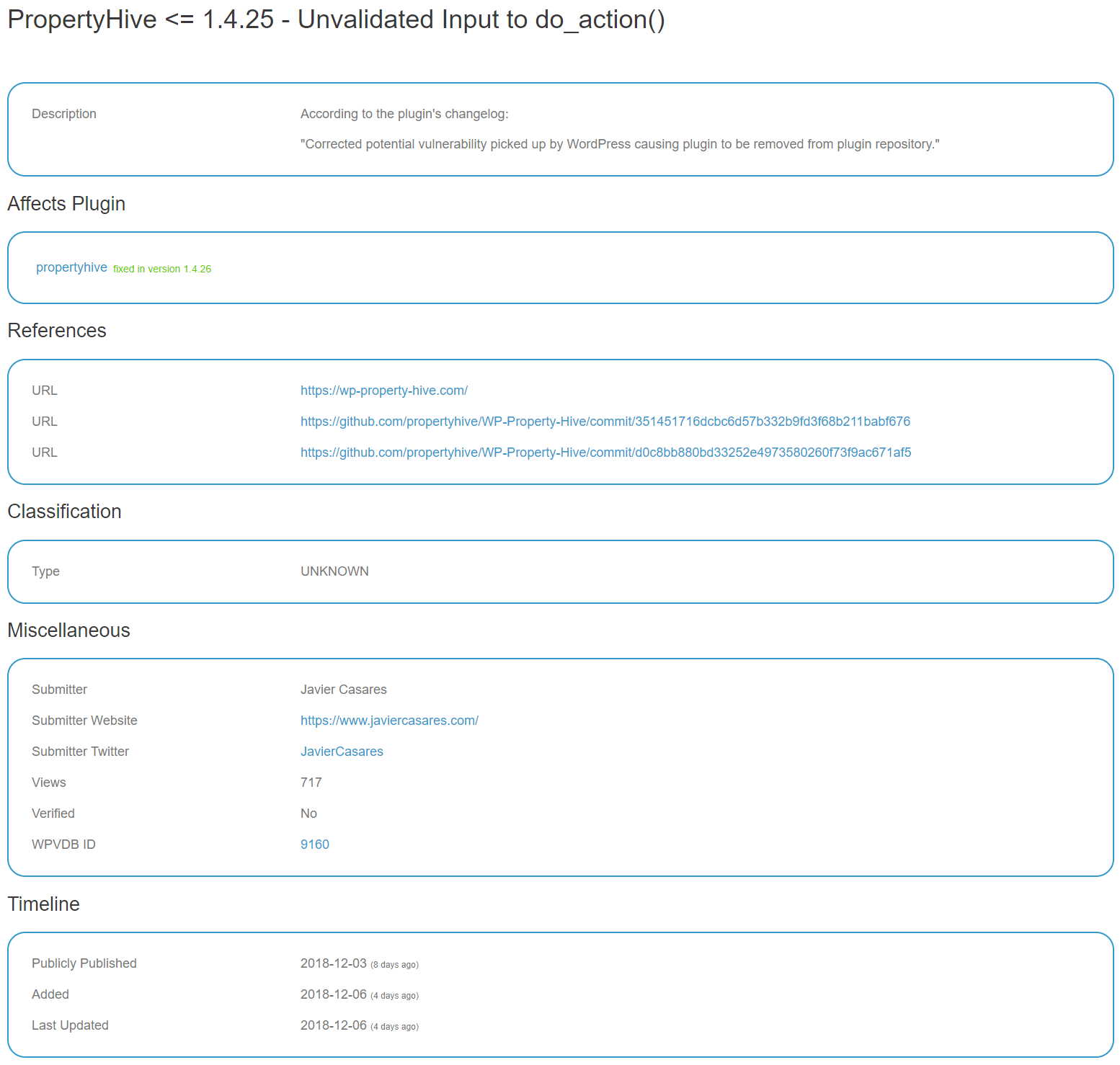
We disclosed a remote code execution (RCE) vulnerability on November 30, which WPScan falsely claims was publicly published on December 3 and which they only got around to adding on December 6:
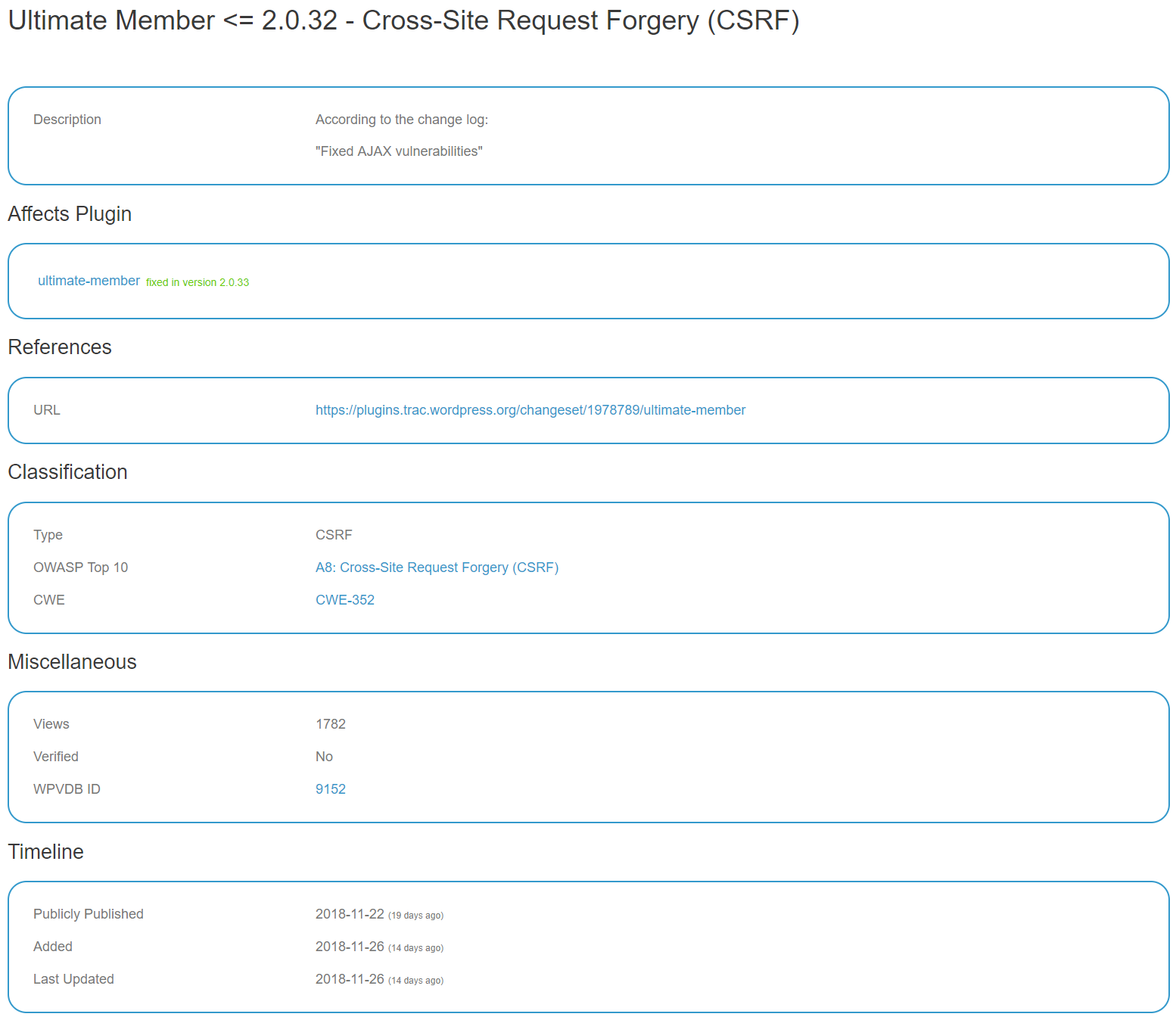
The last of our recently disclosed vulnerabilities they managed to add seems to be missing more important information than attribution to us, as they list a vulnerability in Ultimate Member as being a cross-site request forgery (CSRF) vulnerability:
CSRF, involves causing someone else to take an action they didn’t intend to, so what you can do with that is rather important. For example, disabling an advertising notice in a plugin wouldn’t really be something anyone would care about. In this case though it would have allowed remote code execution (RCE), which is a fairly serious issue.