We Warned About “Easily Exploitable Critical Vulnerabilities” in ProfilePress Nearly a Month Before Other Security Providers
Yesterday Wordfence disclosed vulnerabilities that existed in the WordPress plugin ProfilePress (previously WP User Avatar) that they described as “critical and easily exploitable security issues” that:
made it possible for an attacker to upload arbitrary files to a vulnerable site and register as an administrator on sites even if user registration was disabled, all without requiring any prior authentication
Well, they disclosed them for most people, but for our customer, they were warned about these vulnerabilities on June 1, 27 days earlier. Even before that, on May 25, we had warned that plugin was insecure and recommend not using it until the issues were addressed, after our proactive monitoring had detected another vulnerability in it:
The tool flags other possible security issues in the plugin, so we wouldn’t recommend using the plugin unless the security has more broadly been reviewed and corrected.
That was two days before Wordfence claims to have provided protection against some security issues in the plugin:
Wordfence Premium users received a firewall rule to protect against any exploits targeting these vulnerabilities on May 27, 2021.
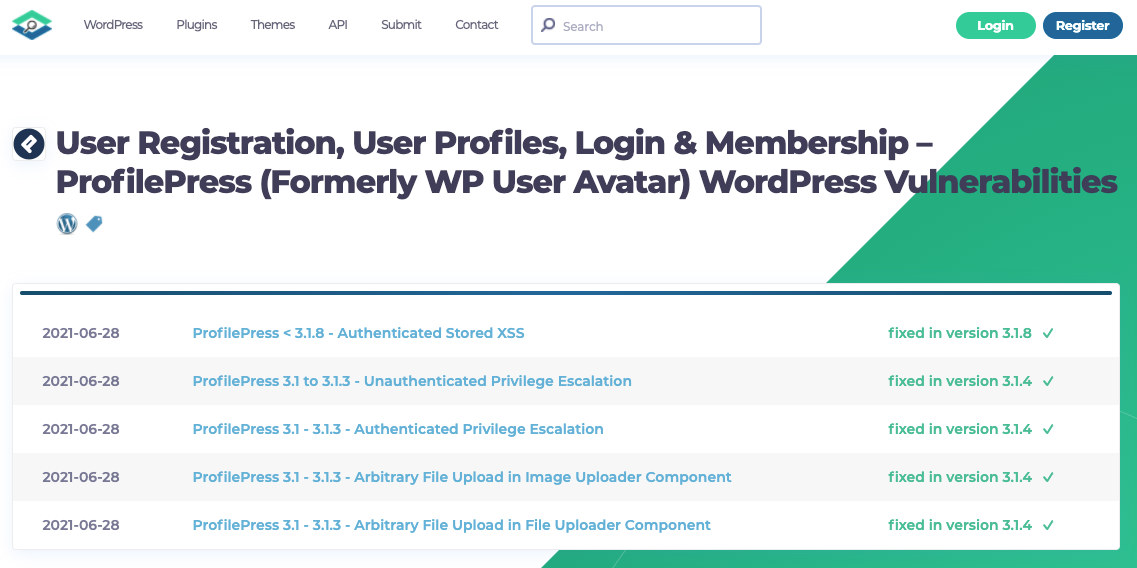
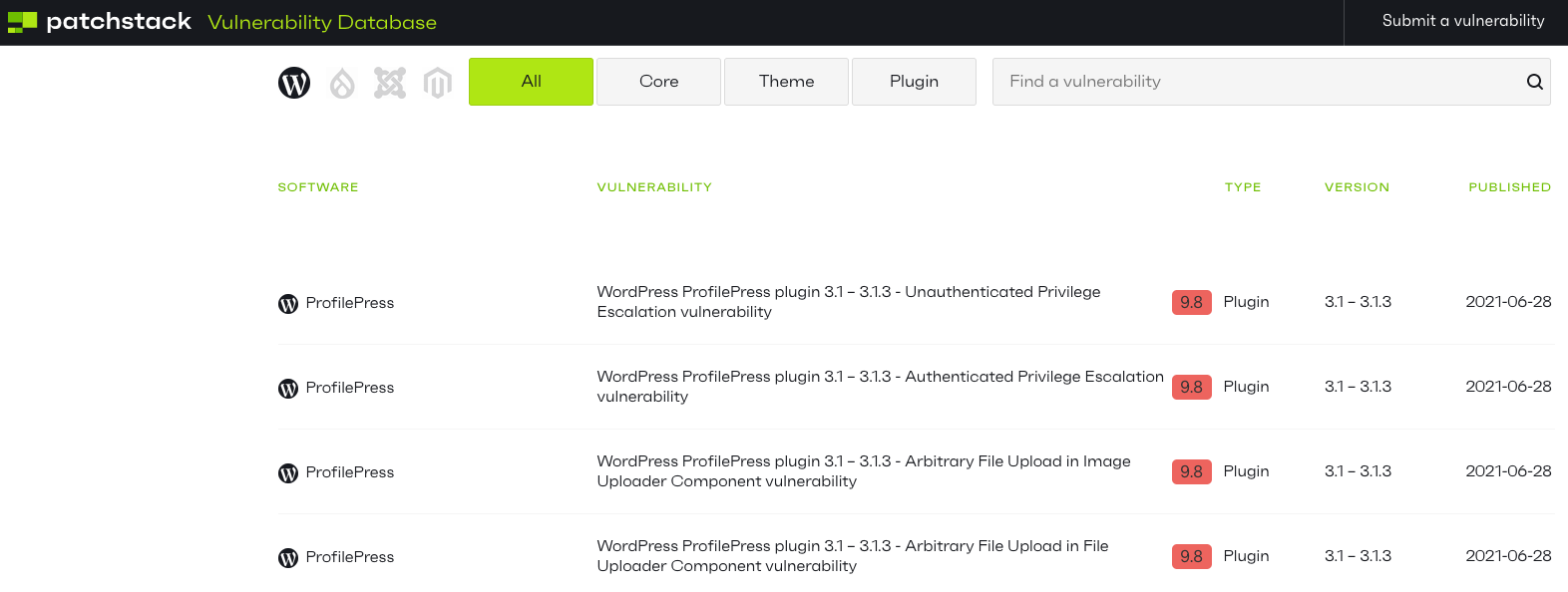
WPScan and Patchstack Well Behind and Get Wrong Versions
If you were relying on other data providers on vulnerabilities on WordPress plugins, you still haven’t been warned about the first vulnerability that was discovered by us in ProfilePress, and with the ones discovered by Wordfence, they only warned yesterday, instead at the beginning of the month.
Here is WPScan:
(The first entry looks like it is really isn’t a vulnerability, though we still need to confirm that.)
Here is Patchstack:
Inexplicably, they both got the versions affected wrong, as version 3.0 was the first version affected. That is strange since Wordfence’s post correctly identifies the versions affected:
immediately if you are running a vulnerable version of this plugin (3.0- 3.1.3).
What makes that odder is that they list the same versions as affected, perhaps one is copying from the other?
Update (6/29/2021): It turns that Wordfence first listed the wrong versions as being vulnerable, though they corrected their information. Neither of those other data sources checked things out for themselves, which you need to do since vulnerability reports are often inaccurate (and often in more substantive ways than it was here).
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade