WordPress Security Plugins Failed to Protect Against Vulnerability When Using Gutenberg Editor
In WordPress 5.0, which was released in December 2018, a new editor was introduced, known as the block editor or Gutenberg. In our latest test of WordPress security plugins to see if they can protect against vulnerabilities, we found no plugins provided protection against a vulnerability when exploited through that editor. Further testing confirmed that two of the plugins that would likely provide protection against that type of vulnerability did when using the Classic editor. The other plugins that would likely to provide protection didn’t provide protection even with Classic editor, but further testing confirmed that it also fails to provide the same protection with the Gutenberg editor that it would provide when using the Classic editor.
The type of vulnerability used in the test is being found in WordPress plugins quite often recently. It is an authenticated persistent cross-site scripting (XSS) vulnerability caused by a lack of proper security handling of shortcode attributes. That would allow an attacker to cause arbitrary JavaScript code to run on frontend pages of the website. These are not a serious issue, since the attacker would need be able to generate content that includes a shortcode, which would normally require access to a WordPress account that can create a post. Making those of more a concern though is that we have been finding recently that developers are failing in attempts to fix those, as we found, for example, with a plugin with 200,000+ installs.
The vulnerability being used exists in the current version, 2.0.5, of the plugin CookieYes GDPR Cookie Consent & Compliance Notice, which has 1+ million installs. We found that vulnerability while looking in to insecure usage of the extract() function in the most popular WordPress plugins.
Normally we do vulnerability testing using the Classic editor, but when for our security plugin testing environment we would have to install that, so we used the default Gutenberg editor instead. That created a problem for our upcoming WordPress firewall plugin, as we hadn’t added protection for when data is transmitted in the way it is by the Gutenberg editor. So the protection we provide against this type of vulnerability didn’t work, unless the Classic editor was used.
That our plugin didn’t provide protection is bad, but our plugin has yet to be released and has only been in development for a fairly short time. The same can’t be said for the other two plugins that in our testing have provide the most protection NinjaFirewall and Wordfence Security.
NinjaFirewall did protect against this vulnerability when using the Classic editor, but it didn’t with Gutenberg editor.
Wordfence Security is even worse, as it didn’t provided protection even with the Classic editor. Using something else that Wordfence Security would block when using the Classic editor, we were able to confirm that it also fails to provide the same protection when using the Gutenberg editor.
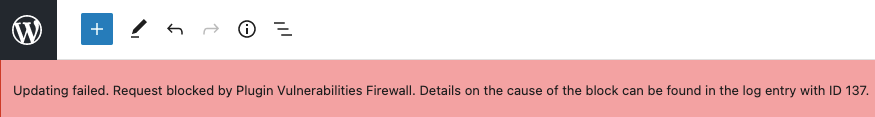
Upon realizing the problem, we updated our plugin to provide protection when using the Gutenberg editor. We even have added a customized block response so that the editor clearly explains what is going on when trying to save or publish a post that contain content blocked by our firewall:
Testing Procedure
For each of the tested plugin, we set up an install of WordPress 5.8.1, installed version 2.0.5 of CookieYes GDPR Cookie Consent & Compliance Notice and installed the latest version of the security plugin. We tried to enable any feature of the plugin that could possibly have an impact on stopping exploitation of the vulnerability. We didn’t set up any additional service connected with the plugins.
We used the proof of concept provided in our post on the vulnerability for the exploit attempts.
The 25 plugins we tested include the security plugins listed in the Popular plugins section of the Plugin Directory and some others that look to be intended or marketed to prevent this type of situation. If you would like to see an additional plugin included in future testing, please leave a comment on the post or contact us.
Results
None of the plugins provided protection when using the Gutenberg editor.
The full results are below:
All In One WP Security & Firewall
- WordPress.org Plugin Directory page
- Active Installs: 900,000+
- Version Tested: 4.4.9
Result: Failed to prevent exploitation.
Anti-Malware Security and Brute-Force Firewall
- WordPress.org Plugin Directory page
- Active Installs: 200,000+
- Version Tested: 4.20.72
Result: Failed to prevent exploitation.
AntiHacker
- WordPress.org Plugin Directory page
- Active Installs: 1,000+
- Version Tested: 3.26
Result: Failed to prevent exploitation.
BBQ Firewall
- WordPress.org Plugin Directory page
- Active Installs: 100,000+
- Version Tested: 20210719
Result: Failed to prevent exploitation.
BulletProof Security
- WordPress.org Plugin Directory page
- Active Installs: 50,000+
- Version Tested: 5.2
Result: Failed to prevent exploitation.
Clearfy
- WordPress.org Plugin Directory page
- Active Installs: 100,000+
- Version Tested: 1.9.6
Result: Failed to prevent exploitation.
Defender
- WordPress.org Plugin Directory page
- Active Installs: 60,000+
- Version Tested: 2.5.7
Result: Failed to prevent exploitation.
Hide My WP Ghost Lite
- WordPress.org Plugin Directory page
- Active Installs: 100,000+
- Version Tested: 4.1.09
Result: Failed to prevent exploitation.
iThemes Security
- WordPress.org Plugin Directory page
- Active Installs: 1+ Million
- Version Tested: 8.0.2
Result: Failed to prevent exploitation.
Jetpack
- WordPress.org Plugin Directory page
- Active Installs: 5+ Million
- Version Tested: 10.1
Result: Failed to prevent exploitation.
MalCare Security
- WordPress.org Plugin Directory page
- Active Installs: 100,000+
- Version Tested: 4.63
Result: Failed to prevent exploitation.
NinjaFirewall
- WordPress.org Plugin Directory page
- Active Installs: 70,000+
- Version Tested: 4.4.2
Result: Failed to prevent exploitation.
Plugin Vulnerabilities Firewall
- Page on our website
- Active Installs: N/A
- Version Tested: Beta
Result: Failed to prevent exploitation.
SecuPress Free
- WordPress.org Plugin Directory page
- Active Installs: 30,000+
- Version Tested: 2.0.3
Result: Failed to prevent exploitation.
Security by CleanTalk
- WordPress.org Plugin Directory page
- Active Installs: 10,000+
- Version Tested: 2.72.2
Result: Failed to prevent exploitation.
Security Ninja
- WordPress.org Plugin Directory page
- Active Installs: 10,000+
- Version Tested: 5.124
Result: Failed to prevent exploitation.
Shield Security
- WordPress.org Plugin Directory page
- Active Installs: 60,000+
- Version Tested: 12.0.8
Result: Failed to prevent exploitation.
SiteGround Security
- WordPress.org Plugin Directory page
- Active Installs: 100,000+
- Version Tested: 1.1.2
Result: Failed to prevent exploitation.
SiteGuard WP Plugin
- WordPress.org Plugin Directory page
- Active Installs: 400,000+
- Version Tested: 1.6.0
Result: Failed to prevent exploitation.
Sucuri Security
- WordPress.org Plugin Directory page
- Active Installs: 800,000+
- Version Tested: 1.8.28
Result: Failed to prevent exploitation.
Titan Anti-spam & Security
- WordPress.org Plugin Directory page
- Active Installs: 100,000+
- Version Tested: 7.2.8
Result: Failed to prevent exploitation.
Wordfence Security
- WordPress.org Plugin Directory page
- Active Installs: 4+ Million
- Version Tested: 7.5.5
Result: Failed to prevent exploitation.
WP Cerber Security, Anti-spam & Malware Scan
- WordPress.org Plugin Directory page
- Active Installs: 200,000+
- Version Tested: 8.9.3
Result: Failed to prevent exploitation.
WP Hardening
- WordPress.org Plugin Directory page
- Active Installs: 6,000+
- Version Tested: 1.2.2
Result: Failed to prevent exploitation.
WP Hide & Security Enhancer
- WordPress.org Plugin Directory page
- Active Installs: 80,000+
- Version Tested: 1.6.3.9
Result: Failed to prevent exploitation.
Plugin Security Scorecard Grade for BBQ Firewall
Checked on June 17, 2025See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for BulletProof Security
Checked on June 12, 2025See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for Clearfy
Checked on August 20, 2024See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for Defender
Checked on November 20, 2024See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for Jetpack
Checked on November 24, 2024See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for MalCare Security
Checked on November 7, 2024See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for NinjaFirewall
Checked on June 12, 2025See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for Security Ninja
Checked on April 1, 2025See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for Shield Security
Checked on January 19, 2025See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for Sucuri Security
Checked on June 14, 2025See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for Titan Anti-spam & Security
Checked on June 20, 2025See issues causing the plugin to get less than A+ grade