Security Vulnerability Data Providers Didn’t Actually Check if WordPress Plugin Vulnerability Was Fixed
Two months ago, a review of the WordPress plugin Category Specific RSS feed Subscription was made with the title “Exploit?” with this information provided:
Lot’s of bots are looking for this file used with this plugin:
/wordpress/wp-content/plugins/category-specific-rss-feed-menu/wp_cat_rss_style.css
In looking over this at the time, we didn’t see a vulnerability in the current version that should explain this, but we have been warning our customers of an unfixed vulnerability in the plugin since June 7, 2019. More on that later.
A week ago, a reply to that review stated that there was unfixed vulnerability in the plugin:
You were right! I received the following message from my server security:
“WordPress Category Specific RSS feed Subscription plugin <= 2.0 – Cross-Site Request Forgery (CSRF) vulnerability”
I notice that this has been raised but has not been resolved by the author.
The title of the claimed vulnerability, though, wouldn’t necessarily indicate that a vulnerability an unresolved vulnerability exists in the plugin. As the affected versions listed is less than or equal to 2.0 and the current version is 2.1, which was released was released on May 31, 2019.
Based on the title used, that information is presumably coming from Patchstack. Their listing claims the issue was fixed in version 2.1:
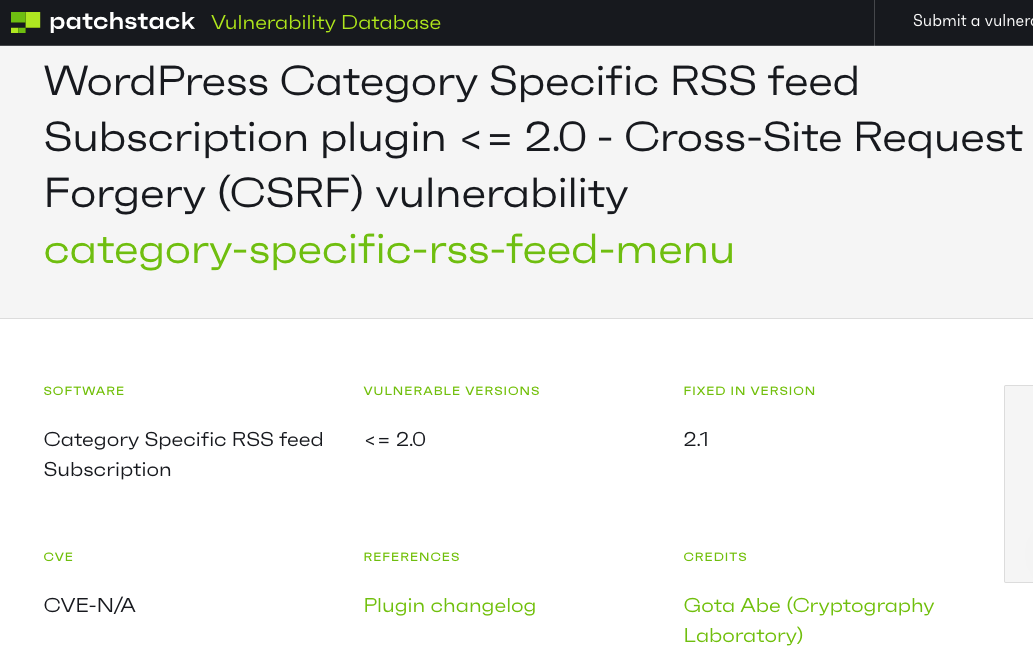
Based on the information provided in that reply, we don’t know if the information was presented in a way that made clear that the vulnerability was already supposed to be fixed, but even in cases where that is attempted, it is often missed.
Patchstack isn’t Verifying Vulnerabilities
Patchstack claims that they verify vulnerability information in their data set:
Hand curated, verified and enriched WordPress vulnerability information.
But as the situation is another example of, that often isn’t the case.
The changelog for version 2.1 of the plugin does indicate that a security improvement was made, but not for a CSRF vulnerability:
Sanitization work.
The changes made in that version are in line with that description. There isn’t even an attempt to address a CSRF vulnerability, so it would appear that Patchstack didn’t do any due diligence before claiming that there was a vulnerability and it was fixed. They are not alone in that.
WPScan Isn’t Verifying Vulnerabilities Either
Automattic’s WPScan, which is claimed to have “dedicated team of WordPress security experts”, also makes the same claim that there was a vulnerability and it was fixed, despite them clearly not checking on this either:
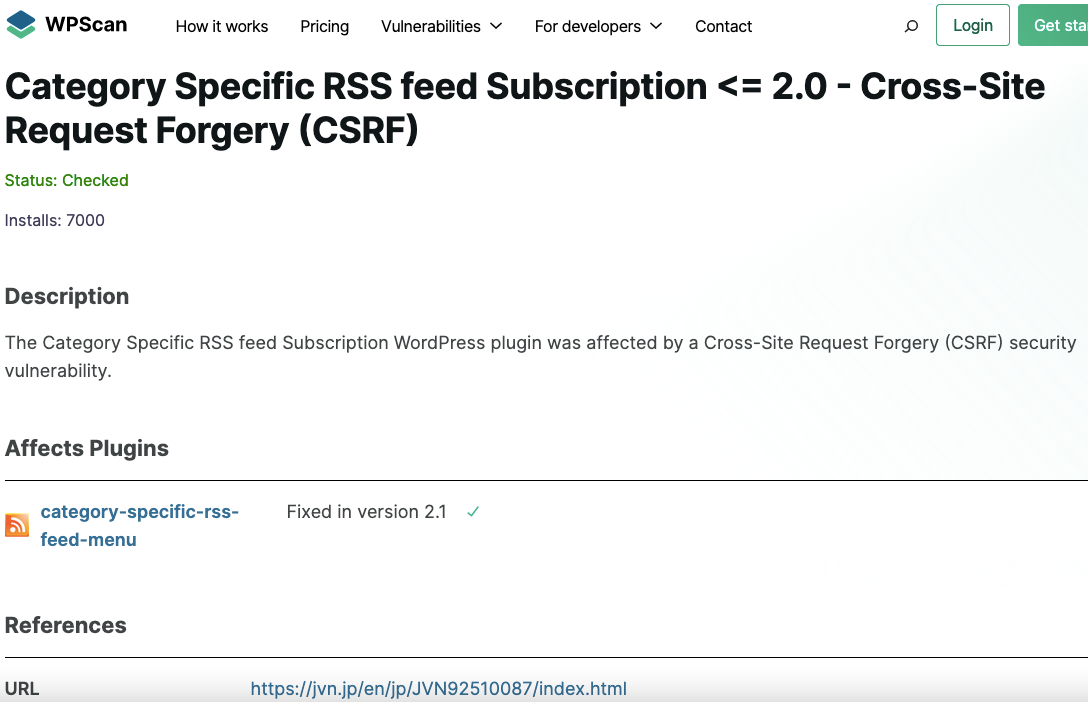
So both of these companies are providing people what is basically junk information, as they don’t check on the claims they are making and they are telling people that unfixed vulnerabilities have been fixed. Part of the problem is that other providers will pass along their information to their unsuspecting customers. Patchstack even touts those providers trust them:
Patchstack is trusted by the leading WordPress experts such as: Pagely, Cloudways, GridPane, Plesk and others!
Not the First to Know
In line with them not be concerned whether what they are saying is true, both claim that you are the first to know about vulnerabilities with them.
Here is WPScan:
Be the first to know about vulnerabilities affecting your WordPress installation, plugins, and themes.
And here is Patchstack:
Be the first to know about new vulnerabilities!
That isn’t actually true, not just because both of them couldn’t be first, but both of them were relying on another source for their claim, the JVN, which put out its information on this on July 18, 2019. That was twelve days after we had warned our customer about what had happened.
The Original Source Makes Qualified Claims, Unlike Patchstack and WPScan
The JVN is described this way:
JVN stands for “the Japan Vulnerability Notes.” It is a vulnerability information portal site designed to help ensure Internet security by providing vulnerability information and their solutions for software products used in Japan. JVN is operated jointly by the JPCERT Coordination Center and the Information-technology Promotion Agency (IPA).
Their listing in this case, unlike Patchstack’s and WPScan’s, does not claim the issue has been addressed, only that it has been claimed to have been addressed.
Update the plugin according to the information provided by the developer.
Gota Abe of Cryptography Laboratory,Department of Information and Communication Engineering,Tokyo Denki University directly reported this vulnerability to the developer and coordinated on his own.
After coordination was completed, this case was reported to IPA, and JPCERT/CC coordinated with the developer for the publication under Information Security Early Warning Partnership.
As we had noted to our customers before that was released, the cross-site request forgery (CSRF) vulnerability still existed in version 2.1. We notified the developer of that at the time, but they never addressed it.
The vulnerability exists in the first code that runs when accessing the plugin’s settings page:
244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 | function category_specific_option_page() { global $category_specific_rss_version; if (isset($_POST['info_update'])) { echo '<div id="message" class="updated fade"><p><strong>'; update_option('rss_widget_title_name', sanitize_text_field($_POST["rss_widget_title_name"])); update_option('cat_rss_all_cat', ($_POST['cat_rss_all_cat'] == '1') ? '1' : '-1' ); update_option('cat_rss_all_aut', ($_POST['cat_rss_all_aut'] == '1') ? '1' : '-1' ); update_option('cat_rss_show_post_count', ($_POST['cat_rss_show_post_count'] == '1') ? '1' : '-1' ); update_option('cat_rss_show_image_on_left', ($_POST['cat_rss_show_image_on_left'] == '1') ? '1' : '-1' ); update_option('cat_rss_custom', ($_POST['cat_rss_custom'] == '1') ? '1' : '-1' ); update_option('rss_category_1_name', sanitize_text_field($_POST["rss_category_1_name"])); update_option('rss_category_1_link', sanitize_text_field($_POST["rss_category_1_link"])); update_option('rss_category_2_name', sanitize_text_field($_POST["rss_category_2_name"])); update_option('rss_category_2_link', sanitize_text_field($_POST["rss_category_2_link"])); update_option('rss_category_3_name', sanitize_text_field($_POST["rss_category_3_name"])); update_option('rss_category_3_link', sanitize_text_field($_POST["rss_category_3_link"])); update_option('rss_category_4_name', sanitize_text_field($_POST["rss_category_4_name"])); update_option('rss_category_4_link', sanitize_text_field($_POST["rss_category_4_link"])); update_option('rss_category_5_name', sanitize_text_field($_POST["rss_category_5_name"])); update_option('rss_category_5_link', sanitize_text_field($_POST["rss_category_5_link"])); update_option('rss_category_6_name', sanitize_text_field($_POST["rss_category_6_name"])); update_option('rss_category_6_link', sanitize_text_field($_POST["rss_category_6_link"])); update_option('rss_category_7_name', sanitize_text_field($_POST["rss_category_7_name"])); update_option('rss_category_7_link', sanitize_text_field($_POST["rss_category_7_link"])); update_option('rss_category_8_name', sanitize_text_field($_POST["rss_category_8_name"])); update_option('rss_category_8_link', sanitize_text_field($_POST["rss_category_8_link"])); |
We have now notified the JVN that their listing contains inaccurate information.
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade