WPScan Issues Two CVE IDs for Same Vulnerability While Failing to Warn for 7 Months That It Was Unfixed
On August 9, 2021, a security update was released for the WordPress plugin Favicon by RealFaviconGenerator, which has 200,000+ installs. The changelog for that was:
Fix XSS security issue, reported by WPSpan.com. See https://wpscan.com/vulnerability/ed9d26be-cc96-4274-a05b-0b7ad9d8cfd9?fbclid=IwAR2aRMXRjbGm9ppoI9tM-OHm26Q0ax4yt0MkcP5sp0-pz9D4eVIEHQwvG1Y
The same day, though, we detailed for our customers that vulnerability had not actually been fixed. We also notified the developer of that. The developer only got around to fixing this on Friday of last week.
If you were to rely on information from one of our competitors, WPScan, which is owned by the company closely associated with WordPress, Automattic, you wouldn’t have known that. Instead, they claimed the vulnerability had been fixed in August:
![]()
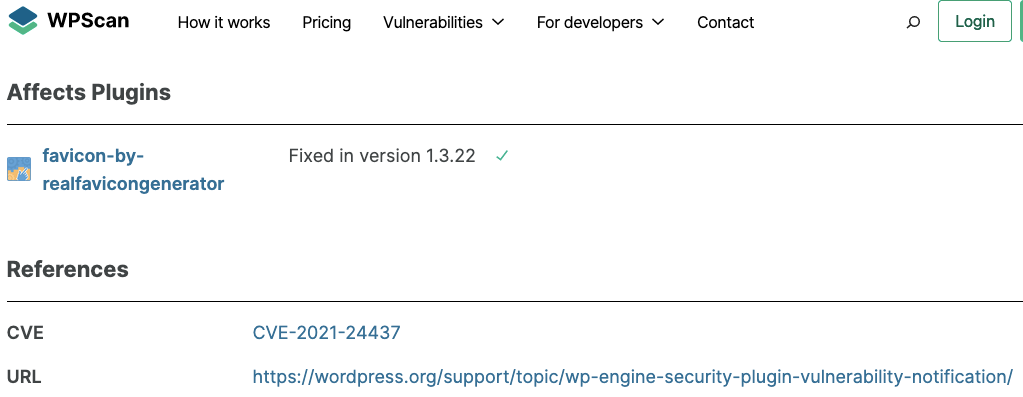
Last week they created another listing for the same vulnerability claiming that it had only been fixed in the version also released last week:
![]()
With the second listing, the description is this:
The plugin does not properly sanitise and escape the json_result_url parameter before outputting it back in the Favicon admin dashboard, leading to a Reflected Cross-Site Scripting issue
The proof of concept for the first references the same parameter as that description (as this is the same vulnerability):
Affected parameter: json_result_url
https://example.com/wp-admin/themes.php?page=favicon-by-realfavicongenerator%2Fadmin%2Fclass-favicon-by-realfavicongenerator-admin.phpfavicon_appearance_menu&json_result_url=%3Cimg%20src=x%20onerror=alert(document.domain)%3E
That they got this wrong isn’t a one off issue with incorrectly claiming that vulenrabilities have been fixed, but a frequent issue. Less than a week ago. we detailed another example of that we happened to look back at.
Many Problems with WPScan Being a CVE Numbering Authorities (CNA)
If you look at security coverage of vulnerabilities, you will often to see CVE IDs for them mentioned and they seem to be treated by journalists and others as having some sort of significance. But as we have recently noted, though, WPScan has been issuing them for non-vulnerabilities. They can do that because they are CVE Number Authority (CNA). CVE describe those in this way:
In general, CNAs are vendors or other seasoned organizations with a record of researching vulnerabilities and demonstrating security advisory capabilities. They commonly have an established user base, and their security information is regularly consulted by researchers and vendors. They may also be well-established bug bounty hunters.
An onboarding process has been established to ensure that CNAs meet the standards of the CVE program. Potential CVE analysts and CNA candidates are given strict instructions for vetting vulnerabilities, including a wide range of examples and exercises. Should a CNA demonstrate the appropriate level of expertise and communication required, they are approved and become operational.
By any reasonable measure, that doesn’t describe WPScan or other CNAs we have run across.
More problematically, WPScan is listed as the CNA for “WordPress core, plugins, and themes”, despite being not being the relevant party for that and with CVE listing their organization type as “Vendors and Projects”, despite being an unrelated third-party to WordPress. That predates Automattic’s ownership of it. We contacted CVE about this a while ago and they didn’t correct that or even acknowlege that they are not the vendor or project for those things, which was very odd.
CVE IDs are supposed to be “unique, common identifiers for publicly known cybersecurity vulnerabilities”, which doesn’t end up being true when you have a entity that doesn’t do the vetting they are supposed to, as WPScan has issue two CVE IDs for this vulnerabilty.

Patchstack Didn’t Verify This Either
Another one of our competitors in this space, Patchstack, which is also a CNA, claims, like WPScan does, that they verify vulnerabilities being added to their data set:
Hand curated, verified and enriched WordPress vulnerability information.
Yet they also have two listings for this vulnerability, with the first one also inaccurately claiming the vulnerability was fixed when it hadn’t:
![]()
![]()
Like a lot of other instances, it appears they simply copied WPScan’s information, which runs contrary to how they market what they are providing, and produces poor results.
Plugin Security Scorecard Grade for Favicon by RealFaviconGenerator
Checked on September 16, 2024See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade