Patchstack Claims “Vulnerability” in WordPress Plugin With 600,000+ Installs Was Fixed Despite No Changes Being Made
Partly because of the large number of false reports of vulnerabilities in WordPress plugins being put out by our competitors, we now put more focus on claims of vulnerabilities in plugins used by our customers. So once at least one of customers started using the plugin GA Google Analytics, our systems notified us we needed to review a report put out by one of the aforementioned competitors, Patchstack, last year on a claimed authenticated persistent cross-Site scripting (XSS) vulnerability the plugin.
The report is credited to “m0ze (Patchstack Red Team)”, so this was something coming directly from Patchstack, instead of just something they copied from somewhere else.
Patchstack provided little in the way of details, making it difficult to understand what was supposed to be at issue and how it was supposed to be resolved.
They did claim that the vulnerability existed in version 20210211 of the plugin and was fixed in version 20210719. The changelog entries for the version this was supposed to be fixed in suggest that not only was a vulnerability not fixed in that version, but no substantive changes were made:
- Improves readme/documentation
- Tests on WordPress 5.8
Looking at the changes made in that version, that is the case. The only changes made to the code in that version were to change version numbers.
They link to a YouTube video, which shows that the claimed vulnerability involves entering JavaScript code in to the following settings for the plugin, which are intended to contain JavaScript code:
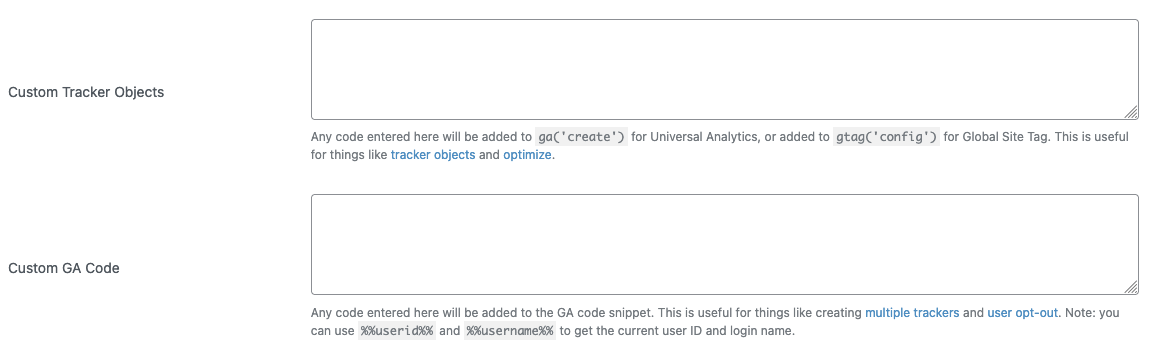
Access to the settings is limited to Administrators, who are allowed to do the equivalent of XSS:
87 | add_options_page($title_page, $title_menu, 'manage_options', 'ga-google-analytics', array($this, 'display_settings')); |
So that isn’t a vulnerability. But if it was, it still exists.
It is one thing to mistakenly claim that there is a vulnerability when there isn’t and or to mistakenly claim that a vulnerability has been fixed when there was an attempt to fix it was made, but what happened here seems indefensible. Making it worse, Patchstack market’s themselves as if they do the kind of work that we actually do with our dataset, while not appearing to not even trying to do the same:
Hand curated, verified and enriched vulnerability information by Patchstack security experts.