What Is Going on With the Closure of the WordPress Security Plugin WP Cerber?
The WordPress security plugin WP Cerber is marketed as if it protects websites from being hacked:
Defends WordPress against hacker attacks, spam, trojans, and malware.
Though, as we discussed in June, it actually could have been the cause of websites being hacked, as the developer had fixed a serious exploitable vulnerability in it earlier this year. More troublingly, the developer didn’t acknowledge that they had fixed a vulnerability. The plugin also failed to protect against exploitation of the vulnerability. It wasn’t alone, as only 2 of 30 WordPress security plugins we tested provided protection.
On August 18, the plugin was closed on the WordPress’ plugin directory. Oddly enough, while the plugin has remained closed since then, it currently is listed as being closed on September 22:

The graph of downloads shows they dropped off starting on August 18 and haven’t returned through today:
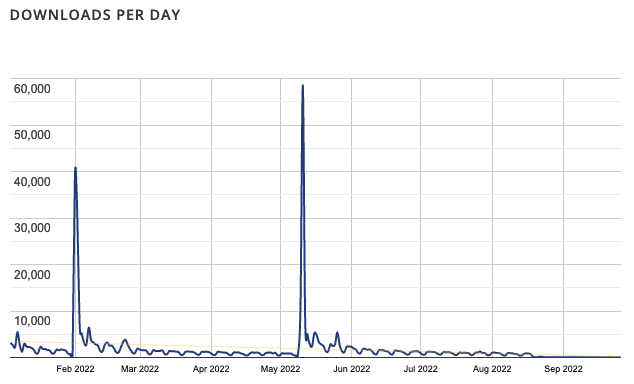
So what happened? Well that isn’t totally clear, but let’s take a look at what appears to be going on.
Wordfence’s False Claim of a Security Vulnerability
The starting point for the closure appears to be based on a claim of a vulnerability in the plugin from the developer of a competing plugin, Wordfence. Here is how the developer of WP Cerber responded to them making such a claim:
Hi! There is no unpatched vulnerabilities in the WP Cerber. Please ask the Wordfence team for detailed clarifications regarding that unverified claim.
In a follow up they wrote this:
I would prefer that some “security experts” (not WordFence) do their jobs more responsibly. I saw a report regarding a WP Cerber bug that is claimed as a vulnerability but it’s not a vulnerability per se. It’s a built-in WordPress feature. I really appreciate and thankful to people reporting bugs and other issues, but this time it’s not what it’s claimed. WP Cerber users, as always, can sleep calmly.
P.S. The reported bug has been fixed in WP Cerber 9.1.
So who is right there? It seems no one. Here is what Wordfence claimed was a vulnerability:
The WP Cerber Security plugin for WordPress is vulnerable to security protection bypass in versions up to, and including 9.0, that makes user enumeration possible. This is due to improper validation on the value supplied through the ‘author’ parameter found in the ~/cerber-load.php file. In vulnerable versions, the plugin only blocks requests if the value supplied is numeric, making it possible for attackers to supply additional non-numeric characters to bypass the protection. The non-numeric characters are stripped and the user requested is displayed. This can be used by unauthenticated attackers to gather information about users that can targeted in further attacks.
Usernames are not considered a secret in WordPress, so it wouldn’t be a vulnerability for them to be shown. So there isn’t a vulnerability here, but WP Cerber itself is claiming that hiding the username is a security feature, when it isn’t.
That issue was claimed by Wordfence to have been resolved in version 9.1 of the plugin, which was submitted to the plugin directory on August 20. But the plugin wasn’t re-opened after that. The developer made this claim as to the cause of it:
A new, internal plugin inspection guideline for moderators has recently been enforced. Some plugins require to be refactored due to new limitations and policies.
So it would appear that a false report of a vulnerability from a competitor led to the developer being required to make additional changes to the plugin to simply allow it to be in the plugin directory, when it otherwise would have still been there.
A Real Security Vulnerability and No Update Available?
On September 9, a new version, 9.2, was submitted to the plugin directory with a concerning changelog entry:
Fixed A critical XSS vulnerability.
In a blog post, the developer wrote this about the new version:
This is an important security update containing a vulnerability fix. Please install it as soon as possible by downloading the new version of WP Cerber from our website or the plugin wordpress.org repository.
Since the plugin continues to be closed on the plugin directory, the 200,000+ websites using it can not install that update trough the normal update mechanism. That is a general problem, that already has a solution, though one WordPress has refused to simply use.
As we don’t currently have any customers using the plugin and no report has been released about this claimed vulnerability, we can’t say whether it really exists, it has been fixed, and is critical.
Version 9.2 Introduces Problematic Changes
Looking at the recent support forum topics, it appears that version 9.2 is broken for some people. That would appear to be caused by this change:
Implemented Content-Security-Policy HTTP header as an extra layer of protection for the WP Cerber admin pages. This also means no support for unsecure HTTP connections to WP Cerber admin pages anymore.
A bigger issue is that version 9.2 made this change:
Implemented support for a new WP Cerber software repository. The software repository is our special website where we publish updates to our plugins and add-ons allowing you our customers update them from within WordPress dashboard. The use of the repository can be disabled in the settings.
That appears to be a clear violation of the guidelines for the plugin directory, as it states the following is not allowed:
Serving updates or otherwise installing plugins, themes, or add-ons from servers other than WordPress.org’s
There is good reason for that restriction, as that type of functionality was abused to add malicious code on to websites using one of the 1,000 most popular WordPress plugins not that long ago. (The restriction was in place before that occurred and didn’t stop that situation.)
What to Do if You Use WP Cerber
For those already using WP Cerber, what should they do about the situation? The best answer seems to be to switch to other solutions for security features you actually need, as there are ongoing problems with the plugin and its developer that shouldn’t exist.
A lot of what WP Cerber provides isn’t actually needed and in some cases causes unnecessary problems. If you don’t know if you need a security feature, there is a good chance you don’t.
If you are looking for a WordPress security plugin that really “[d]efends WordPress against hacker attacks”, unlike WP Cerber, you can check out our testing of WordPress security firewall plugins for better options.