Wordfence Claimed That 300,000+ WordPress Sites Contained a “Critical” Security Vulnerability, It Wasn’t True
On Monday, a report was posted on Packet Storm claiming that the latest version of the WordPress plugin Photo Gallery by 10Web, 1.8.0, had a reflected cross-site scripting (XSS) vulnerability. That type of vulnerability isn’t a major issue and isn’t something that would be expected to be exploited on a wide-scale, if exploited at all. The plugin does have 300,000+ active installations according to WordPress, so there still could be a lot of websites that would be impacted. That would be if there was a vulnerability, but there wasn’t.
It shouldn’t be hard to tell this is a false report.
Here are three of the earliest lines in the report:
Website : wordpress.org/plugins/
Vendor : Photo Gallery Team – wpsofts.com
Software : WordPress Photo Gallery 1.8.0
The website is the main address of the WordPress Plugin Directory, not the page for the plugin. The second lists a vendor, which isn’t the vendor of the plugin. The third line list the current version for the plugin, but the name doesn’t actually include “WordPress”.
Looking further through the report doesn’t detail the vulnerable code, but provides a proof of concept for exploiting this on a live website. That is a big warning sign for anyone that frequently reviews reports like this. The proof of concept is for the website listed as the vendor of the plugin (but isn’t the vendor):
https://wpsofts.com/grid-kit-demo/photo-gallery/?pid=47&pg=2&zdifv%2527%253e%253cscript%253ealert%25281%2529%253c%252fscript%253eh18n1=1
If you head to the homepage for that website, you find that the website is for a different plugin, named GridKit Portfolio Gallery.
It appears that the reporter here, for reasons we can’t explain, believed that because the URL of a demo for that plugin included “photo-gallery”, that meant there was a vulnerability in an unrelated plugin with the slug “photo-gallery”.
That isn’t newsworthy. What appears to have happened after that is.
“Critical” Security Vulnerability
The next day a topic was started on the support forum for Photo Gallery by 10Web asking about Wordfence, claiming there was a “critical” security vulnerability with the plugin, but without providing any details. The poster was asking the developer of the plugin for the details, which they didn’t have and they indicated they had not been contacted about this. Two others responded that the developer should contact Wordfence about this, which seems backwards. Shouldn’t Wordfence be contacting the developer?
Wordfence’s message claimed there was a “critical” security vulnerability and told people to remove the plugin until the unspecified issue was addressed:
To protect your site from this vulnerability, the safest option is to deactivate and completely remove “Photo Gallery” until a patched version is available.
Here is how that message looked in full in Wordfence Security:
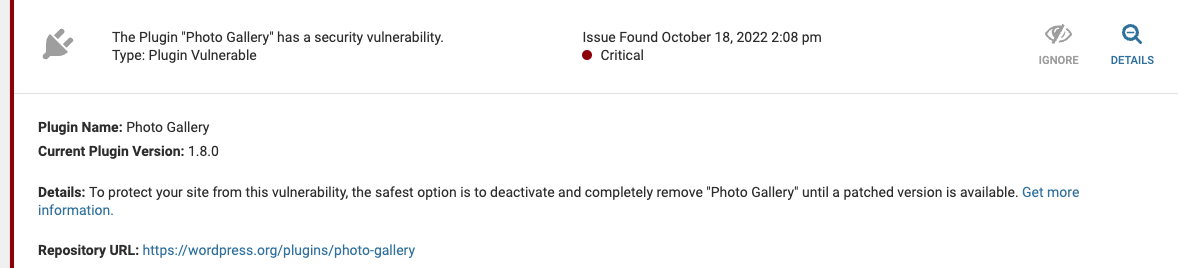
Wordfence’s actions there seem problematic, as they claim that there is a “critical” vulnerability, but didn’t provide a way for anyone to independently check on their serious claim.
The developer’s response in another topic about this raises even more questions about Wordfence’s conduct:
Thanks for your patience. We are happy to say that the alert was there by mistake.
WordFence has removed the vulnerability record, and it should no longer alert you in scan results.
I want to sincerely apologize for this incorrect reporting. If you have any further questions please let us know.
Have a great day!
So Wordfence appears to have gotten things wrong and yet the developer is the one apologizing.
The plugin is still at version 1.8.0, so the developer hasn’t made any changes that would explain Wordfence no longer claiming there is a vulnerability.
So what explains the mistake? Wordfence hasn’t provided a response, but based on the timing, the likely explanation is that they fell for this false report.
Even if the report were true, calling it a “critical” security vulnerability wouldn’t be an accurate assessment. In relation to claims about a vulnerability in another plugin, one of their users called this type of inflated severity rating, “demonstrably alarmist” and said it damaged Wordfence’s reputation in their view:
I am very disappointed with Wordfence because despite them also telling me that this is a very minor issue needing multiple event and highly unlikely to affect me, they still flag this issue as a critical issue in their scan. Their scan still recommends that I totally uninstall Tablepress until a patch is released.
This is demonstrably alarmist, and poor advice considering that they have conceded to several different people that it is not a critical issue. So course this damages Wordfence’s reputation for me. How do I know that they are not issuing alarmist warnings about other issues?