Automattic’s WPScan Failed to Catch That WordPress VIP’s Co-Authors Plus Plugin is Still Disclosing Email Addresses
During the summer, one arm of the company closely associated with WordPress, Automattic, WPScan disclosed a vulnerability in plugin, Co-Authors Plus, maintained by another arm of Automattic. WPScan and others in Automattic appear to have failed to look all that closely at the issue, as the plugin still has a closely related vulnerability.
According to the documentation for the plugin, it is maintained by WordPress VIP:
Co-Authors Plus is a plugin maintained by VIP
That is an entity that is supposed to provide the best security:
WordPress VIP offers the highest level of WordPress security. Built with multiple levels of security controls and protection—including edge protection, secure networking, robust access controls, continuous security monitoring, and code scanning—WordPress VIP meets the most exacting security requirements. That’s why it is trusted by customers in industries such as banking, pharmaceuticals, public utilities, and government. It is the only WordPress platform to achieve FedRAMP Authority to Operate (ATO).
Checking Public Rest API Routes
WPScan’s description of the vulnerability was:
The plugin introduced an information disclosure vulnerability (specifically, the e-mails of guest authors) via a public REST endpoint accessible without any authentication
What we found looking over things is that the version that was supposed to address it only partially addressed the issue.
In response to what we saw there, we have created a simple new tool that allows anyone to see what public REST API routes are available on WordPress websites.
If you were to run a website using only the previous version of the plugin through that tool, you get this result:
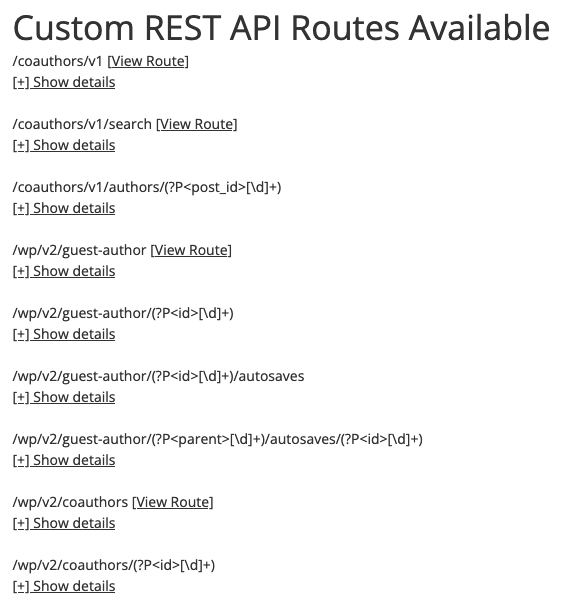
Running the version that was supposed to address the issue through it, you can see that some of the routes have been removed, but most of the publicly available rest routes are still there:
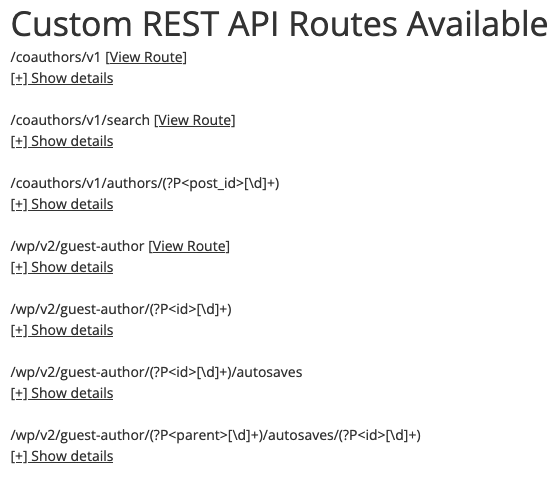
That isn’t a problem on its own, but it wasn’t hard to find that another route isn’t properly secured.
As detailed separately in a more technical post, low level WordPress users are able to use one of the remaining routes to get the email addresses of guests authors, even though they don’t appear to be intended to do that. It appears the problem relates to mixing up two WordPress capabilities, “edit_posts” and “edit_others_posts”.
Automattic Needs to Better Review the Security of Their Plugins
Last month we covered a serious vulnerability that had just been introduced in a plugin identified as coming directly from WordPress, which was in fact developed by Automattic employees. So it appears there is a broader problem with Automattic’s handling of the security of their plugins, despite their claim to “take security seriously“.
It seems like that shouldn’t be happening as they own WPScan, which claims to have a “dedicated team of WordPress security experts”. In reality, their team have shown themselves to have a very limited grasp of security.
If you are relying on software or services from Automattic and security matters to you, it might be a good time to get independent security evaluations done of those to make sure that they are actually secure. If you find additional issues, we would be interested in covering those.