Providers of WordPress Plugin Vulnerability Data Not Actually Verifying if Vulnerabilities Are Fixed
Recently, three ostensibly competing data providers for information on vulnerabilities in WordPress plugins all claimed that a vulnerability had been fixed in a certain version of the plugin Super Socializer.
Here was WPScan, the original source for the claim:
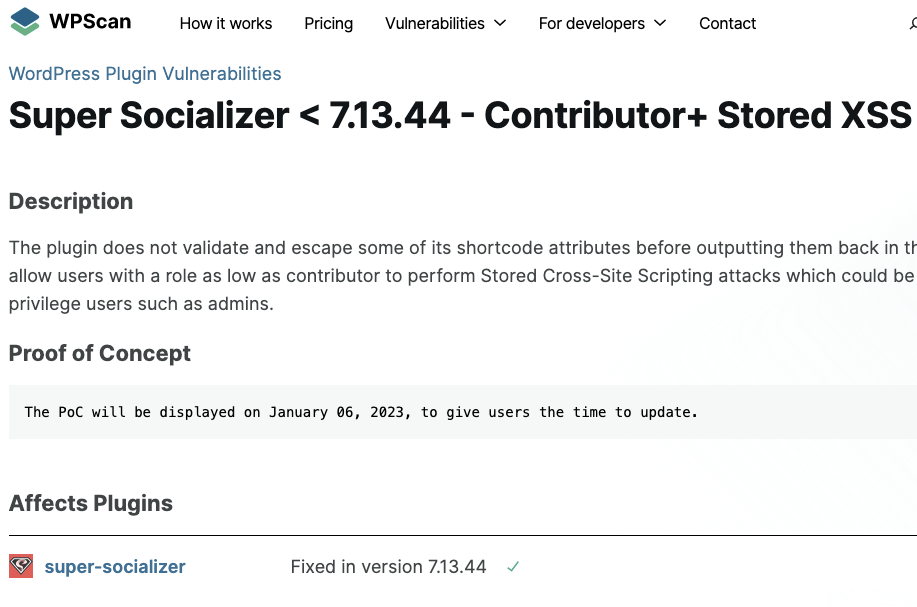
Here is Patchstack making the same claim copied from WPScan:

And finally, Wordfence:
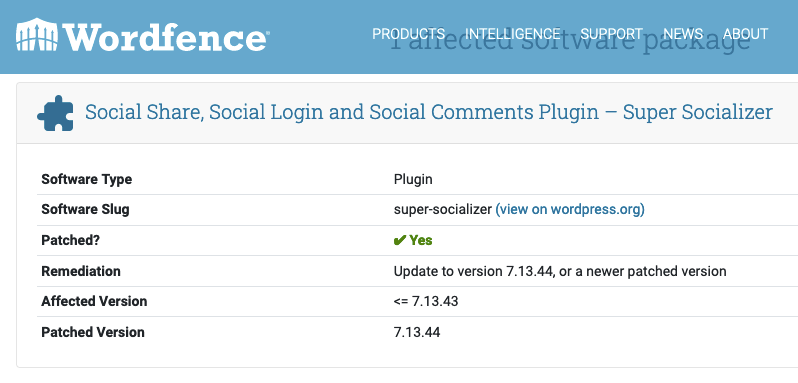
The changelog for the plugin appears to contradict their claim. It states that in version 7.13.44, the described cross-site scripting (XSS) vulnerability in shortcodes was fixed:
[Security] Fixed Cross-Site Scripting vulnerability exploit in the shortcodes
But five days later, the changelog for 7.13.45 claims to have taken more action related to that:
[Security] Fixed Cross-Site Scripting vulnerability exploit in the “type” attribute of [TheChamp-Counter] shortcode
While it isn’t stated there, we know that the version 7.13.44 didn’t fully address the vulnerability, and that caused the second attempt, as we reviewed the attempted fix in 7.13.44, as at least one of our customers was using the plugin, and found that it was incomplete. The developer promptly addressed the remaining issue.
Both Patchstack and Wordfence don’t market themselves as simply copying inaccurate information from another provider, despite doing that here. Patchstack instead markets their data this way:
Hand curated, verified and enriched vulnerability information by Patchstack security experts
And Wordfence this way:
This database is actively maintained by some of the top WordPress vulnerability researchers in the industry.
Not Every Incomplete Fix Gets Addressed Like This
In this situation, the damage from the inaccurate data from those other providers is limited, since we checked over the plugin, caught the issue, and the developer addressed it. Those things are often not true. Since we mainly check over plugins used by our customers and the most serious vulnerabilities in other plugins. And developers often don’t address incomplete fixes in a timely manner, if at all. The lack of timely fix has been the case so far, with two plugins used by at least 400,000+ websites that we warned a week ago had incomplete fixes. Also with those, despite having changelogs indicating security fixes, none of those other providers have even warned about the vulnerabilities at all so far.
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade