Patchstack Causes Developer of 600,000+ Install WordPress Plugin to Release Phantom Security Update
In February of last year, we tried to work with the developer of the Freemius library, which is widely used in WordPress plugins, to address a number of security issues that came up during a security review of a plugin using it. Instead of them working with us, they incompletely addressed the issues on their own. We told them that the fix was incomplete, but they didn’t address things. Earlier this month they were claiming in a blog post that we did “not cooperate” with them in that situation, despite linking to a post about the previous situation where they stated they went “into a ‘silent mode’ and ke[pt] interactions to a minimum”. Also earlier this month, they finally addressed an issue we had warned them about at the time. That has led to a mess for developers and users of plugins using the library (and some not even using it). That mess includes the developer of a plugin with 600,000+ installs to have to release a phantom security update to stop Patchstack from falsely claiming the plugin was still vulnerable.
While Patchstack has caused problems for various developers in this situation (and many others), Freemius is claiming that it is “a security company that truly cares about website security and works with you in full cooperation and coordination”.
The 600,000+ install plugin is Shortcode Ultimate, which addressed the Freemius security issue in version 5.13.1. That version was released on July 2. The changelog for that reads “This update features security improvements and is recommended for all users”.
The release on that date doesn’t match Freemius’ claims surrounding the release of the fix:
In coordination with Patchstack, we decided developers would release a patched version exactly on July 5th (the 4th of July was already taken ????), and the public disclosure would follow on July 18th, giving two additional weeks for users to update.
Things worked precisely as planned! We emailed the patch to the relevant developers and asked them to patch it on July 5th.
Despite the vulnerability having been fixed weeks ago after the issue was re-disclosed, people started complaining to the developer that the vulnerability existed in version 5.13.1. As is often the case, the moderators of the WordPress support forum deleted a lot of the messages from the discussion about that, but can still see some of that here.
One of the now deleted messages from the previously linked discussion said this:
This is direst from iThemes Security support after I asked them about this and about the fact that this has supposedly been patched:
“Unfortunately, the vulnerability is showing as active in the Patchstack Database.
The developer will need to contact patchstack and request they update the database to reflect they’ve issued a patch to resolve the vulnerability.”
Dev- can you please do this?
(What possible reason could there be to delete that?)
Here is Patchstack’s listing at the time, which indeed claimed the fixed version was vulnerable:

It makes no sense that a provider, iThemes, that is falsely claiming that there still was a vulnerability wasn’t fixing their data or dealing with their partner, Patchstack, behind the false claim. But they didn’t, requiring the developer to do that:
I’ve contacted Patchstack today. Their chatbot have promised that they will reply on Monday. I hope they will fix this asap.
Yesterday, the developer responded this way:
Well, it seems Patchstack’s support decided not to respond.
I’m releasing a new version (5.13.2) to suppress security alerts. This should solve the issue.
Patchstack’s lack of a response hardly sounds like “a security company that truly cares about website security” and one that works with others “in full cooperation and coordination”.
The developer did release a new version after that. Now Patchstack is claiming that version fixed this:
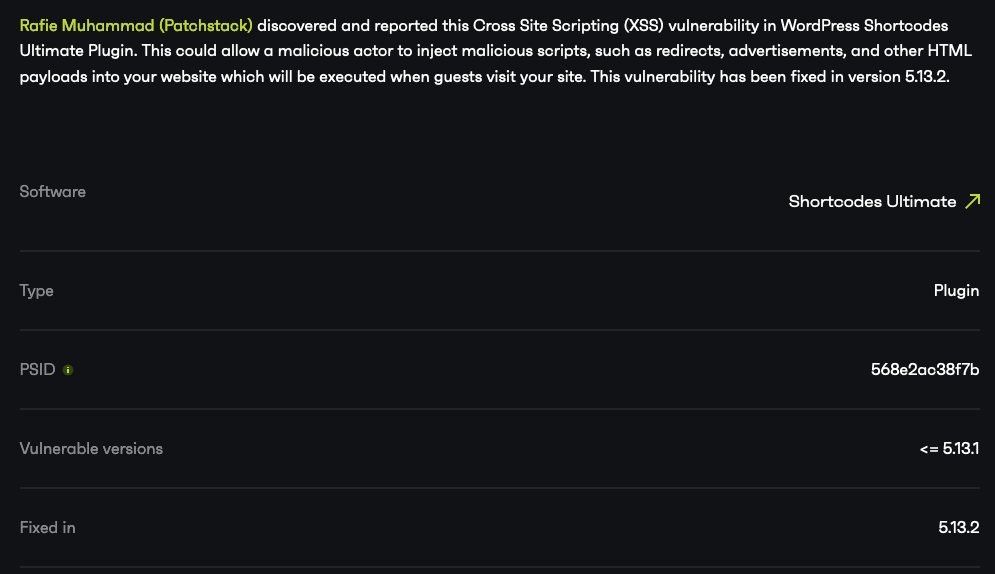
If you look at the changes made in that version, no changes were made to Freemius (we compared the tagged versions of 5.13.1 and 5.13.2 to be sure of that). So this couldn’t have been fixed in that version, meaning either the issue hasn’t been fixed or it was already fixed.
Phantom Vulnerabilities
With another plugin developer, Patchstack is claiming the latest version of a plugin with 20,000+ installs and another with 10,000+ installs are vulnerable despite not even having Freemius in them.
Blaming the Victim
Shortcodes Ultimate recently received a 3 star review that starts this way:
Sorry, but I keep getting this message from my site’s security plugin. This is not good, you need to fix it immediately. Your add-on does its job well and does what it promises, but the security of our corporate sites is paramount.
As you now know, the problem here isn’t with that plugin, but with the inaccurate information from the security plugin they are using. This is not a new problem, for years and years security providers have been falsely claiming that plugins contain vulnerabilities and it hasn’t led to repercussion for those security providers, while causing problems for everybody else.