WordPress Enterprise Agencies Own Guide Suggest Their Security Handling is Not Extremely Vigilant and Highly Competent
Last week, we wrote about how a group of WordPress agencies had released a guide for promoting WordPress to enterprises had provided a misleading view of the security of WordPress. The information provided also suggest they might not have a great grasp of security either. One paragraph in particular stood out, which suggests they are not handling security for their customers well. Under the heading “Enterprise expertise” they wrote this:
Combined, these issues might suggest that WordPress security is lacking, however for large- scale brands that simply isn’t the case. In addition to utilising specialist tools that mitigate the vast majority of security challenges – such as WPScan which quickly flags up vulnerabilities -enterprise agencies are extremely vigilant and highly competent when it comes to protecting clients and site users.
WPScan, which is owned by a company run by the head of WordPress, can only flag publicly known vulnerabilities. So saying it “quickly flags up vulnerabilities” is somewhat misleading based on what it even tries to accomplish, but how about the actual results it delivers?
A month ago, we wrote about a fairly serious vulnerability in a WordPress plugin with 300,000+ installs. One of the notable aspects of that vulnerability was that code that led to the vulnerability had been in the plugin for five months, without apparently being noticed by anyone other than us (the developer of the plugin is a major WordPress security provider). For months, the code wasn’t accessible. Once it was, we confirmed that there was a vulnerability and publicly warned about it. A month on from that, WPScan isn’t warning about it:
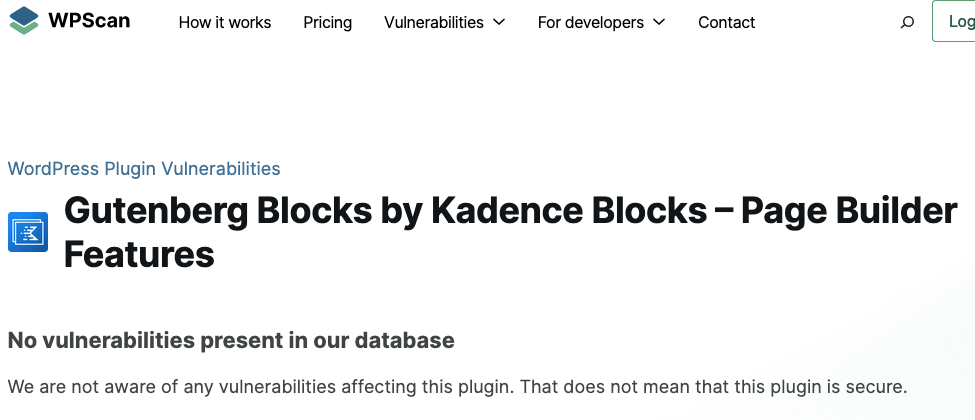
We have seen hackers probing for usage of the plugin since the vulnerability became active, so it definitely should be something they warned about.
With another recent similar and exploitable vulnerability, where we have seen hackers probing for usage of the plugin, WPScan says it took them more than three weeks to warn about it after its public disclosure:
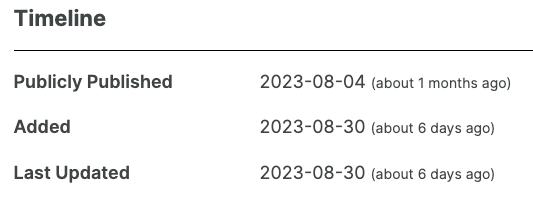
So WPScan isn’t actually doing a good job of quickly flagging publicly known vulnerabilities, even more serious ones.
Doing something quickly isn’t necessarily a good idea. If, say, you are warning about a vulnerability, but incorrectly saying the vulnerability has been fixed when it hasn’t, that could actually make the situation worse. As we have found over and over, WPScan doesn’t actually do the verification work they claim to do with vulnerabilities, leading to repeated claiming unfixed vulnerabilities have been fixed. In one instance we documented, a vulnerability they claimed had been fixed was widely exploited months afterwards, while still unfixed.
It’s hard to believe that “enterprise agencies are extremely vigilant and highly competent when it comes to protecting clients and site users” as the guide claims, when they seem to be unaware that they are touting a tool that does such a bad job at what they are claiming it does.