Hacker Tried to Exploit Our Website Based on Fake Vulnerability Claim From Patchstack
One differentiation between our WordPress firewall plugin and other firewall plugins is that we try to provide users with a good understanding of the risk posed by attacks, instead of scaring people unnecessarily. That issue with lack of respect for users from other providers extends to other areas, particularly with false claims that other WordPress plugins contain vulnerabilities. Those two issues came together recently, when we were checking on a hacker’s attempt to exploit a vulnerability on our own website.
In August of last year, Patchstack claimed that there had been a vulnerability in the WordPress plugin Stock Ticker. They claimed it was “moderately dangerous” and “expected to become exploited:”
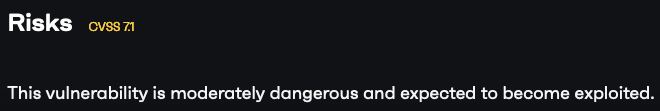
They also claimed that addressing it was of medium priority and they provided the fastest mitigation:
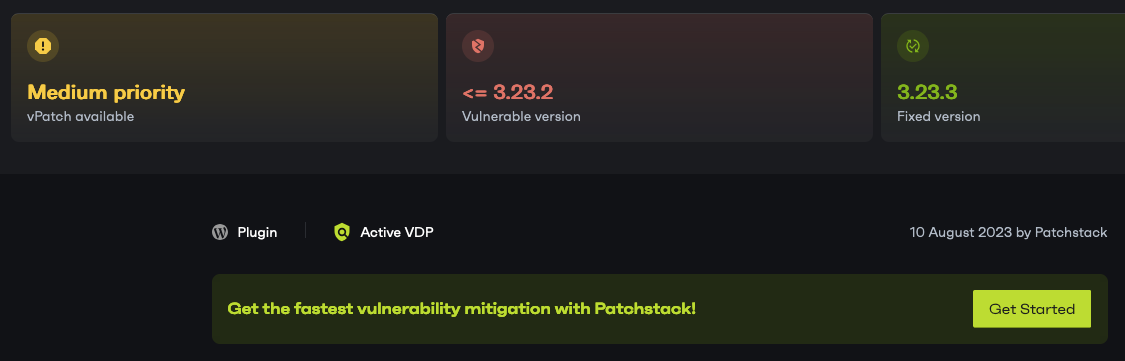
While making those fairly serious claims, they failed to provide any evidence whatsoever that any of that was true.
At best, you could look at the version they claimed the vulnerability was fixed in and try to work back from that.
It appears a not very competent hacker tried to do that, as recently our firewall plugin blocked this exploit attempt on our website:
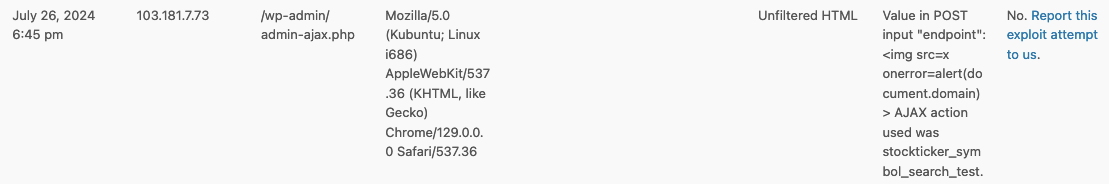
That relates to code that was changed in the version that Patchstack claimed fixed this, but there is an obvious problem. Right above the code that was supposed to fix the issue, were already a capability check to limit access to only certain users logged in to WordPress and a nonce check:
552 553 554 555 556 557 | function ajax_stockticker_symbol_search_test() { // Check permission and validate ajax nonce if ( ! current_user_can( 'manage_options' ) ) { wp_die( -1, 403 ); } check_ajax_referer( 'stock-ticker-js', 'nonce' ); |
An attacker wouldn’t have the needed nonce to pass that check, so there couldn’t be a vulnerability there. It appears that Patchstack didn’t actually vet things, which isn’t all that surprising considering how often they have got basic information about claimed vulnerabilities wrong.
Looking back at previous versions of the plugin, there really had been a vulnerability in the code in the past, but it was already fixed (without the change being disclosed as addressing this vulnerability). But even in the previous versions, the exploit attempt made by the hacker wouldn’t have worked either (due to how the relevant user input is output).
We were never even using the plugin, which is yet another reminder that hackers will try to exploit vulnerabilities without bothering to check if you are even using the vulnerable software. That is something that WordPress security providers are known to claim isn’t happening.
Other Providers as Well
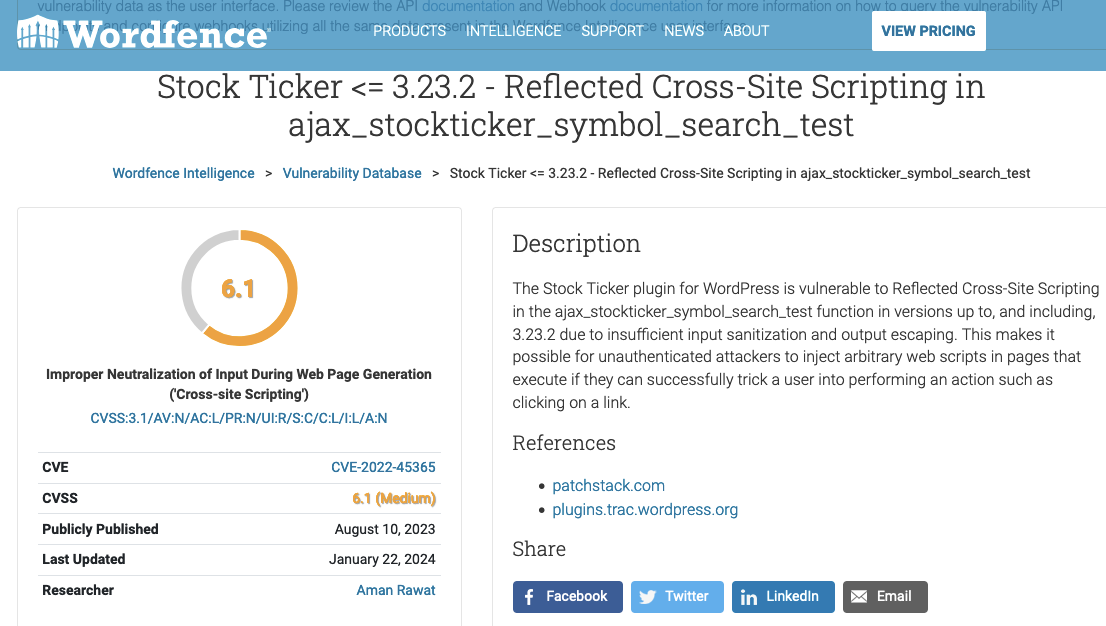
Patchstack isn’t alone in having spread misinformation of the vulnerability having existed in the version it didn’t. Here is Wordfence having copied Patchstack’s misinformation:
And WPScan:
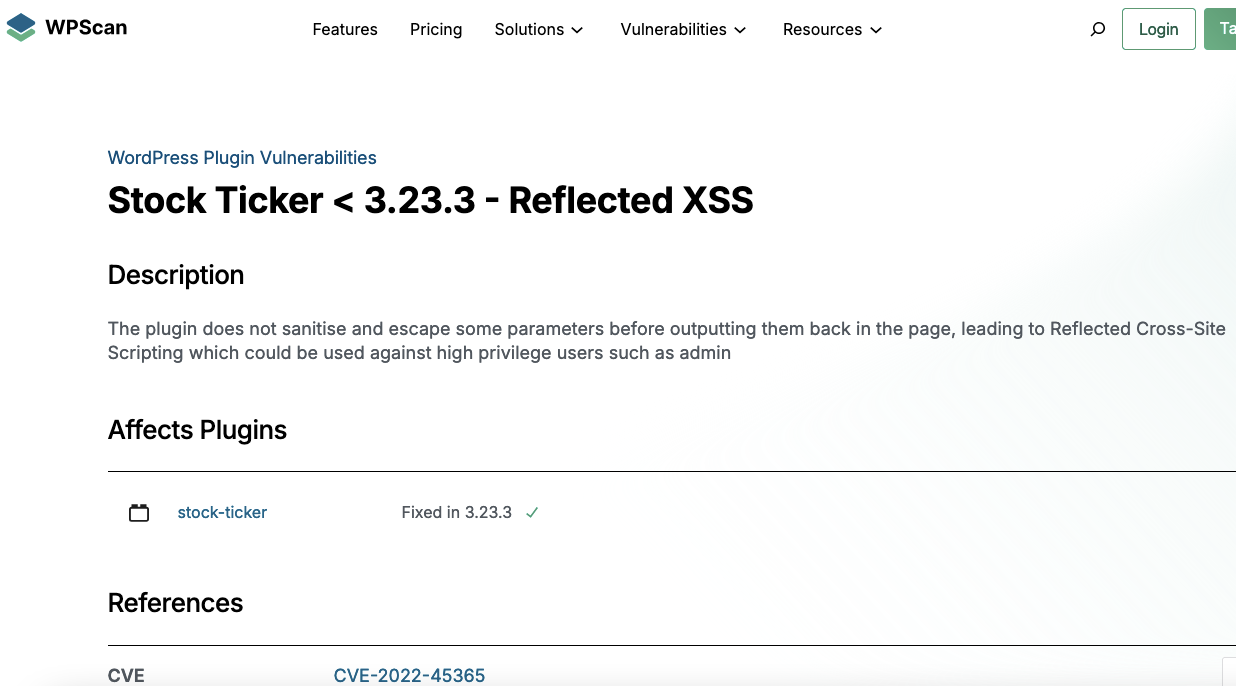
From there, it got spread by other providers who use data that comes from one of those three providers. They often don’t disclose the source and definitely don’t warn people that their data isn’t reliable, despite it being long known those sources are not reliable.
Our new Plugin Security Scorecard does warn of security plugins that are known to utilize unreliable data without disclosing that it is unreliable. We would recommend avoiding any security plugin that applies to.
Faster Mitigation Than Patchstack
While Patchstack claimed to have the fastest mitigation against the vulnerability, as can be seen by the block made by our firewall there, a well-developed WordPress firewall plugin can stop this type of attack without even having to be aware of it. So that would actually be the fastest mitigation. Meanwhile, Patchstack’s own “most advanced on the market” firewall was found to be far from that when an in-depth review was done.
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade