WordPress Security Header Plugins Still Claiming to Provide Protection With Headers That Web Browsers Long Ago Stopped Supporting
In looking into complaints about the search functionality of the WordPress Plugin Directory recently, a common complaint we saw is that new plugins don’t get promoted. As part of an alternative search functionality we have been putting together, we decided to try to address that in part by including a new plugin after the first ten results for queries. When doing a search on “security,” that currently highlights a security headers plugin:
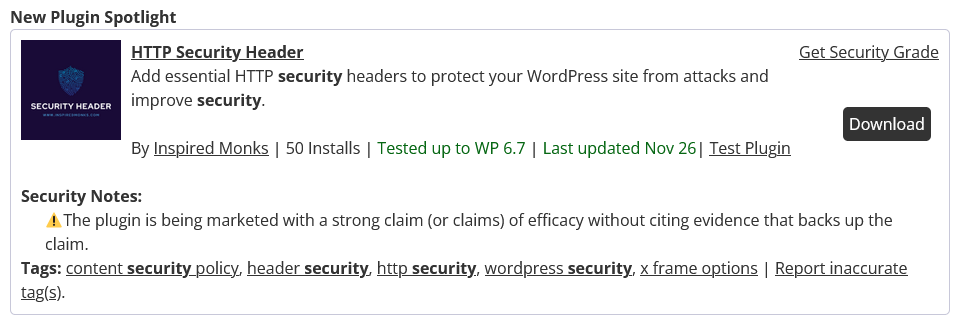
The listing for that plugin, HTTP Security Header, now includes a warning about the plugin “being marketed with a strong claim (or claims) of efficacy without citing evidence that backs up the claim.” That is in reference to this claim made on the plugin’s page on the plugin directory:
Security headers are essential for protecting your WordPress website against common attacks, including cross-site scripting (XSS), clickjacking, content sniffing, and certificate transparency issues.
There is no evidence provided to support the claim. It also isn’t true. One security header could, if configured correctly, provide real security. (That header isn’t easily to broadly implement in an automated fashion.) But others don’t provide any practical security to the average WordPress website.
Among the reasons why these headers are of limited value is that headers tell web browsers to do or not do things. They don’t stop an attacker from taking actions, since they can just ignore them. They can only stop a victim from being exploited, assuming they would stop an attack that is actually happening.
Another issue is that if these headers were actually essential for the security of WordPress websites, why isn’t the developer pushing for WordPress to implement those instead of suggesting installing their plugin? That is a broader issue in the WordPress space, that is conspicuously ignored by supposed journalists and others.
It would appear the developer of the plugin doesn’t have even a basic understanding of those security headers, as at least two of the headers their plugin adds to the website have not been supported by web browsers for years.
Here is a note that Mozilla provides for one of those, Expect-CT:
Note: The
Expect-CTis mostly obsolete since June 2021. Since May 2018, all new TLS certificates are expected to support SCTs by default. Certificates issued before March 2018 were allowed to have a lifetime of 39 months, so they had expired in June 2021. Chromium plans to deprecateExpect-CTheader and to eventually remove it.
The note is outdated, as Chromium removed the code for this in December 2022 (it was already disabled).
With the other header, X-XSS-Protection, Mozilla has this warning that the header can actually create vulnerabilities:
Warning: Even though this feature can protect users of older web browsers that don’t support CSP, in some cases,
X-XSS-Protectioncan create XSS vulnerabilities in otherwise safe websites. See the Security considerations section below for more information.
The Chrome web browser removed support for the header in October 2019. Firefox never supported it.
The plugin does have a glowing review that it improved the security of someone’s website:
I recently integrated the Security Header plugin into my WordPress site, and it has significantly improved my website’s security posture. The user-friendly interface made it easy to enable essential HTTP security headers with just a few clicks.
It was left by the developer of the plugin!
securityheaders.com Strikes Again
The idea that security headers are actually important for protecting WordPress websites seems to often trace back to a website that provides grades based on usage of security headers, securityheaders.com, without providing evidence that these grades actually correlate with improved real world security. Worse still, the developer has actually removed checks for headers they previously claimed were important.
This plugin looks to trace back to that as well, as the screenshots shown for the plugin are of grades on that website.
Other Plugins Also Include These Headers
This plugin isn’t alone in making unsupported claims about security headers and promoting using headers that are no longer supported by web browsers. A quick look showed that plugins with 100,000+, 70,000+ installs, and 50,000+ installs are still promoting the Expect-CT header despite it not serving a purpose at this point. Among other plugins, a million+ install security plugin from a major web host includes tfhe X-XSS-Protection header and claims it provides “Advanced XSS Protection.” That the developer, Siteground, is doing that is likely explained by their utter lack of understanding of security.