300,000 Install WordPress Plugin That Hasn’t Updated Insecure Library in 21 Months Claims Patchstack Ensures the Plugin is Secure
A week ago, someone checked the 300,000 install WordPress plugin FluentSMTP through our Plugin Security Scorecard. That identified multiple issues with the plugin:
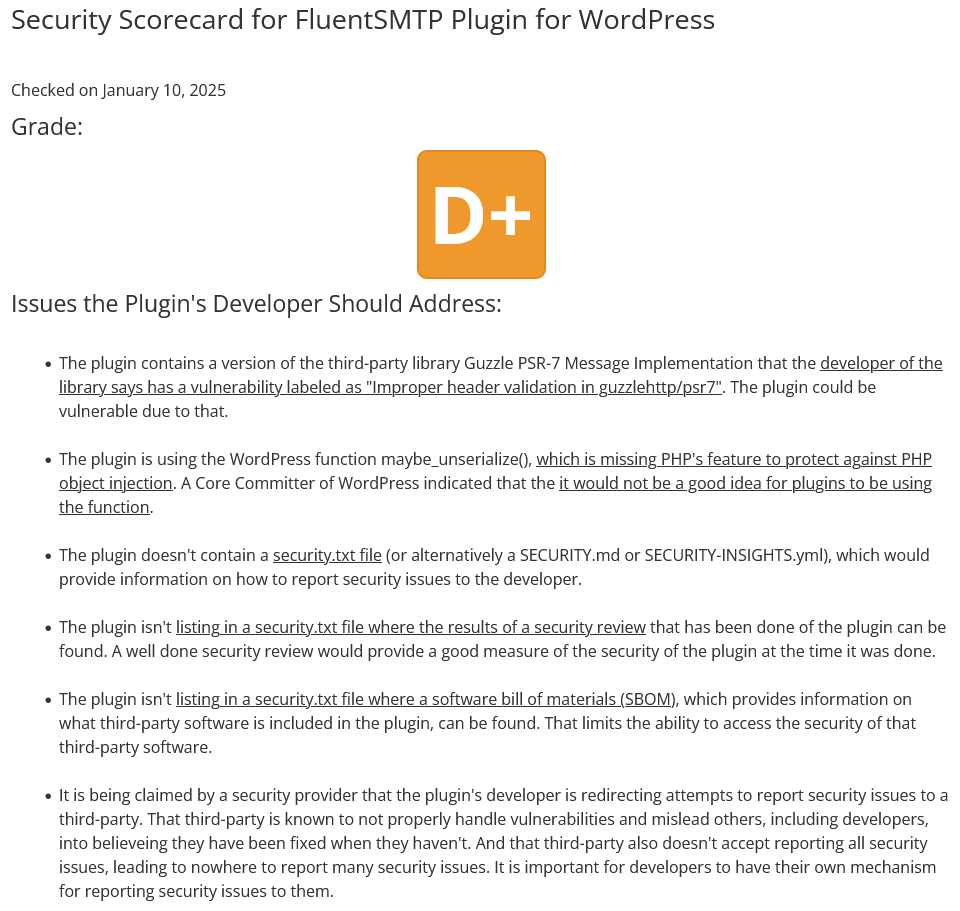
The top issue was flagged for us to check on, as it detected that the plugin was using a version of a library that the developer of the library says has a security issue. We confirmed that the plugin did in fact include the version of the library detected by the tool, which has the security issue. We promptly reached out to the developer about that. A week later, we have yet to hear back from them and there hasn’t been an update to the plugin to address this.
The developer of the library disclosed the issue in April 2023, so the developer has had plenty of time to address it already.
On the contact page for the plugin, there is this FAQ item:
Q. How secure is FluentSMTP?
FluentSMTP utilized API and OAuth 2.0 connections to deliver WordPress emails. These are highly-secure methods so all your emails will be encrypted. We also have a dedicated security partner to ensure FluentSMTP won’t make your website vulnerable.
There isn’t any further information provided there about who the security partner is or what it is they are supposed to be doing to ensure the plugin “won’t make your website vulnerable.” That claim doesn’t line up with the security issue that has long been in the plugin.
So who is this security partner? It is Patchstack. Looking at the FAQ on the plugin’s page on the WordPress Plugin Directory, we noticed it states at one point, “We use Patchstack to manage our security report. Please report in the patchstack page.” Following the link, you end up at a page where Patchstack wants you to direct vulnerabilities reports away from the developer to them. That is something that the head of Patchstack has acknowledged isn’t ethical. It also isn’t going to ensure that the plugin is secure, only that Patchstack gets someone else to do all the work for Patchstack in filing out their vulnerability report for them.
What explains the discrepancy between the developer’s claim and the reality there? It could be that Patchstack misled them as to what is going on. It could be that they are trying to mislead others as to their security (it wouldn’t be the first plugin to that.) It could be something else.
What our tool identified isn’t a vulnerability based on what we know about, only a security issue. It could be a vulnerability, but it isn’t our job to try to figure that out, only to report it to the developer. That can’t be done through Patchstack as they only accept certain reporting certain types of vulnerabilities. (This part of a wider problem that also affects WordPress.) Patchstack also requires agreeing to a legal agreement to report things that way, “I have read the Submission guidelines and accept the Terms of services & Privacy policy.” It is an odd thing to demand of someone trying to help the developer, but Patchstack doesn’t appear to be trying to do that. If they were, they could have identified this issue and let the developer know about, instead of trying to divert vulnerability reports to themselves.