WordPress Plugin Includes Version of Third-Party Library That Was Publicly Known to Be Vulnerable Years Before Plugin Was Even Released
As part of providing a more comprehensive view of the handling of the security of WordPress plugins through our Plugin Security Scorecard tool, we have been expanding the number of third-party libraries it can detect in plugins. If developers of those libraries disclose security advisories on GitHub for those libraries, we incorporate them into the results of the tool as well. Last week we added detection for the jQuery UI JavaScript library. It has already had someone run a plugin through the updated tool that caught the plugin containing a version of a library that contains multiple vulnerability according to the developer:
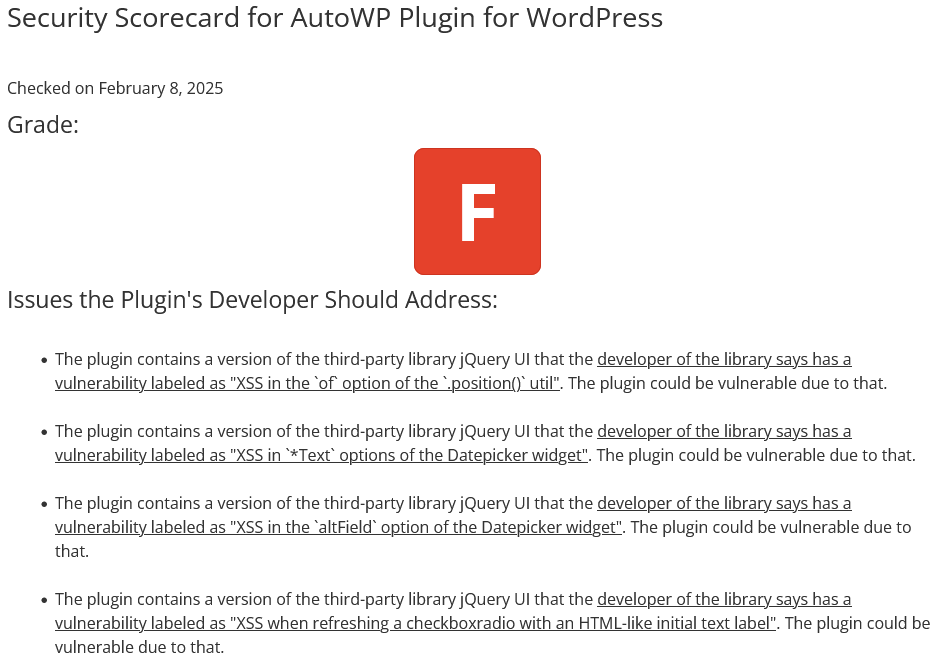
What makes that more notable is that this isn’t the case of a developer failing to keep the library up to date, but including a really out of date version in the when they first added it to the plugin. The plugin, AutoWP, was only released in February of last year and the library was first included in September. Three of the four vulnerabilities were disclosed by the developer in October 2021 and the other in July 2022.
It isn’t a situation where the developer wouldn’t aware it is a really old version of the library, as the first line of the file in the plugin lists the date the version was released, September 14, 2016:
1 | /*! jQuery UI - v1.12.1 - 2016-09-14 |
We tried to contact the developer about that issue, but their only contact method is WhatsApp, despite charging over a $100 a month for a service connected with the plugin.
The developer isn’t exactly honest. As while doing some research on the plugin, we found a post they left on Reddit claiming “While browsing the wordpress directory, I discovered a wordpress plugin called autowp.”
WordPress Plugin Directory Should Catch This
This isn’t the first time recently that the tool has detected known vulnerable versions of libraries being used in WordPress plugins. This is impacting even some of the most popular WordPress plugins. They are not always being fixed (when they are, it isn’t always being disclosed). This is really isn’t something that should require a third-party tool to catch going on with plugins in the WordPress Plugin Directory. We would be happy to work with the team running that if they finally want to work with others to address security problems like this (so far they have been hostile to offers of help to attempt to fix avoidable problems like this). In the meantime, anyone can check plugins through the Plugin Security Checker to see if they are using an increasing number of known vulnerable libraries.