CVE Rule Allows MITRE to Hide When They Are Failing to Provide Timely Information on Vulnerabilities
The CVE system is treated as a reliable source of information on vulnerabilities, both in WordPress plugins, but also more broadly. It isn’t. It also is failing with a more basic element, actually having the records for claimed vulnerabilities. On Friday of last week, a source of security exploit attempt data we recently started monitoring was showing that a vulnerability identified as CVE-2024-48248 was receiving exploit attempts. What was odd about that is the CVE entry for that ID was empty. It looked like this at the time:
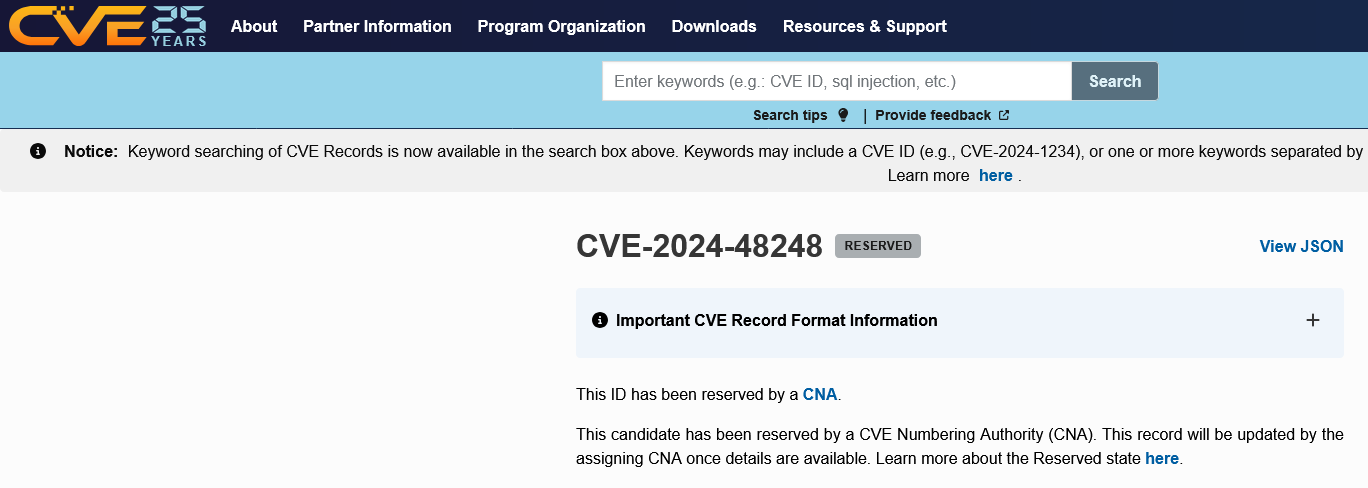
It stated that “This candidate has been reserved by a CVE Numbering Authority (CNA). This record will be updated by the assigning CNA once details are available.” It wasn’t stated who the CNA was, which we will come back to. The claim that it would be updated “once details are available” didn’t make sense as two days before that, a security provider had published a post titled “The Best Security Is When We All Agree To Keep Everything Secret (Except The Secrets) – NAKIVO Backup & Replication (CVE-2024-48248).”
If you contact the entity that runs the CVE System, MITRE about problems with CVE, their response is that they can’t do anything about it, because their rules must be followed. Maybe they are sticklers for rules? That turns out to not be the case, as when the rules are violated, it doesn’t lead to action and the rules are full of holes, so it would be hard to violate the rules. As an example of that, look at the rules related to publishing records:
4.5.1.3 CNAs SHOULD publish a CVE Record to the CVE List within 24 hours of Publicly Disclosing a CVE ID assigned by the CNA. CNAs MAY publish or update CVE Records as part of the CNA’s processes to manage Vulnerability advisories or other public information that references the CVE ID.
4.5.1.4 CNAs MUST publish a CVE Record to the CVE List within 72 hours of Publicly Disclosing a CVE ID assigned by the CNA. If the CNA does not publish within 72 hours, then the CNA’s Root MAY direct the appropriate CNA-LR to publish a CVE Record for the assigned CVE ID. Ownership of the CVE Record MAY be transferred. See also 4.2.1.2.
4.5.1.5 In exigent circumstances, for Publicly Disclosed Vulnerabilities, when a CNA with appropriate scope has not published a CVE Record, an appropriate TL-Root MAY direct an appropriate CNA-LR to publish a CVE Record. Ownership of the CVE Record SHOULD be transferred.
4.5.1.6 CNAs SHOULD publish CVE Records within 72 hours of becoming aware that a CVE ID assigned by the CNA has been Publicly Disclosed by a party other than the CNA.
Rule 4.5.1.4 says that something “MUST” be done, but if it isn’t, then things “MAY” be done.
As of Monday, the record still hadn’t been published, despite the rules stating that should have happened in 72 hours. Who was the CNA who hadn’t published the record they had issued? For some reason, that information is hidden. The rules actually require that to be hidden:
4.5.1.7 The Secretariat MAY publicly identify the CNA who reserved the CVE ID 24 hours after a CVE ID has been Publicly Disclosed. Otherwise, the Secretariat SHOULD NOT publicly identify the CNA until the CVE Record has been published.
For some unexplained reason, there is a restriction on disclosing the information, as it says the CNA “SHOULD NOT” be identified, unless a certain situation occurs, but even then, it only is something “MAY” be done. We contacted MITRE through the CVE website on Monday. We haven’t received a response yet, but the next day the record was published and it turns out the tardy CNA was none other than MITRE:
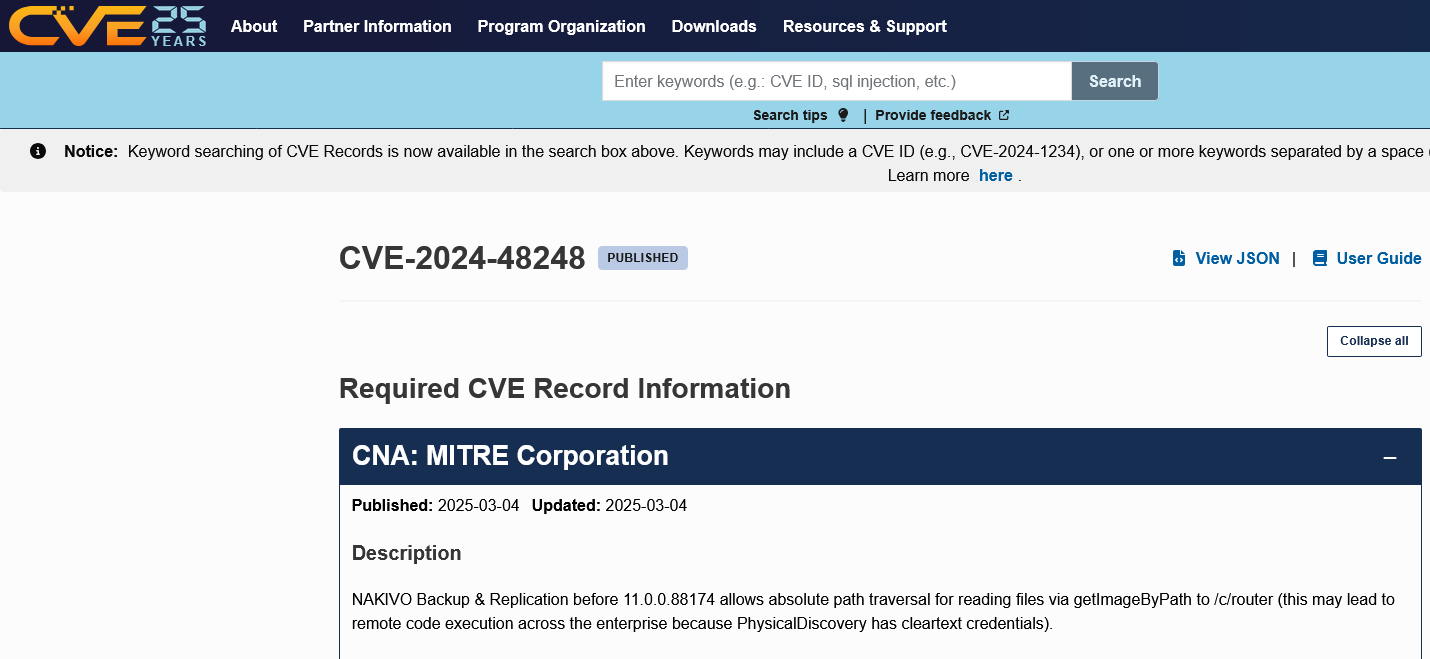
If the CNA was identified, that would make it clearer who is not doing what they are supposed to with the CVE system. Considering it was the entity running CVE here, that might explain why it is hidden.