Developer Outsourcing Security Reporting to Bugcrowd Has Left Insecure Library in WordPress Plugin for Nearly 5 Years
Last week someone checked a WordPress plugin through our Plugin Security Scorecard, which flagged the plugin for a variety of issues:
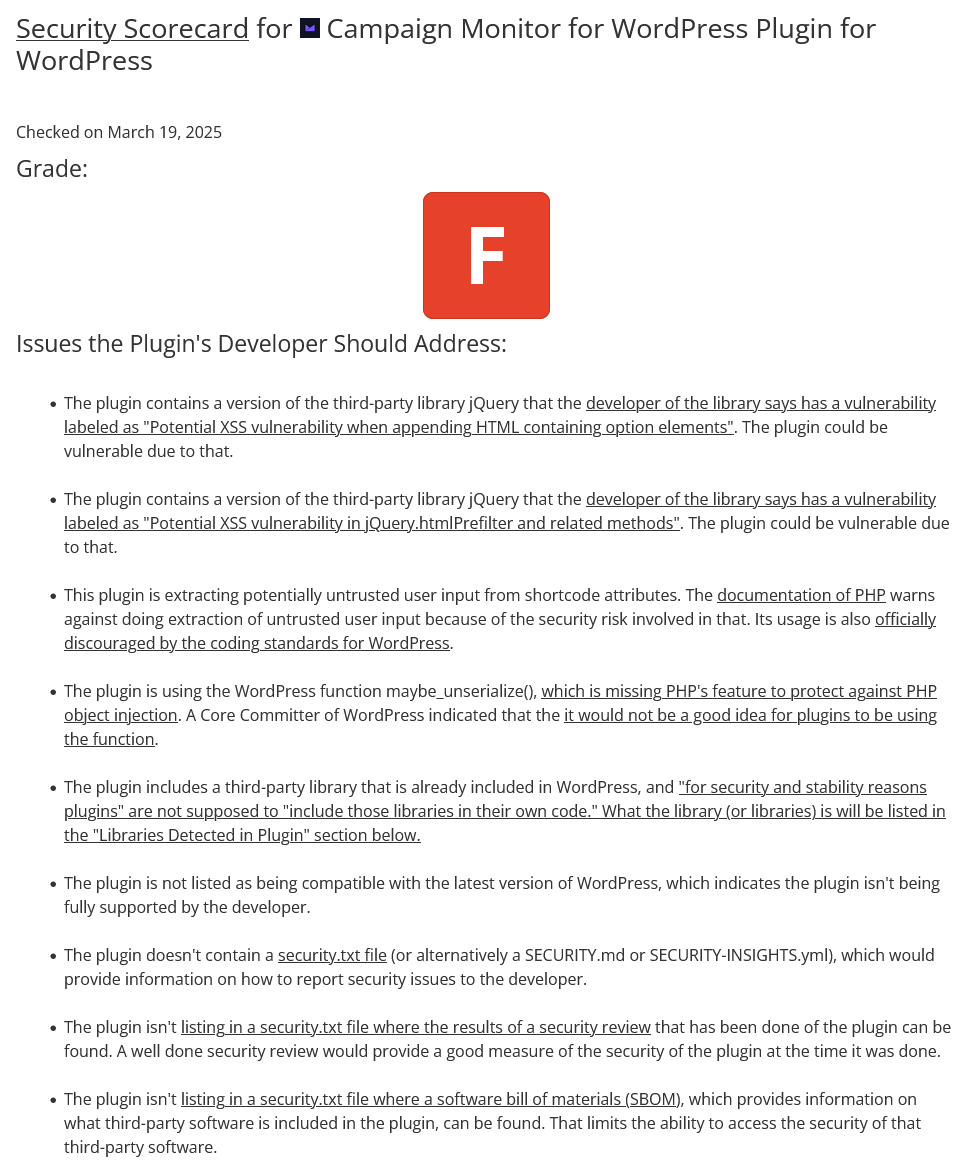
Three of the issues identified are related. The plugin includes the jQuery JavaScript library, despite that already being included in WordPress. As that is already included in WordPress, the rules of the WordPress Plugin directory state that for “security and stability reasons plugins may not include those libraries in their own code.” That seems like a good idea, as plugins keep getting flagged by the Plugin Security Scorecard as using known insecure versions of those included libraries. This plugin being another example. The developer disclosed two related security issues in the version of the library being used in April 2020.
After we were alerted to that situation, we preceded to see how we could get in touch with the developer, Campaign Monitor by Marigold. Surprisingly, considering the insecurity identified by the tool, their website contains a security.txt file with information on contacting them about security issues. In line with the insecurity, reports are being directed to Bugcrowd instead of handled by the developer. That shouldn’t be happening. As Bugcrowd can’t address the problem, they are an unnecessary intermediary here.
(While having a security.txt file is commendable, it has an expiration date of June of last year. The vulnerability disclosure policy link is to a Terms of Use of page, which isn’t what should be linked to, instead of to their Responsible Vulnerability Disclosure page linked on the vulnerability reporting page.)
As is common with bug bounty security companies, Bugcrowd are trying to mislead people in to believing that ineffective methods to secure software are not ineffective. For example, on their homepage, they claim that developers prove they are doing “everything possible to protect stakeholders by accepting vulnerability reports from the public:”

That doesn’t align with what has happened here. Being proactive about security instead of reactive would actually show everything possible is being done.
The homepage also heavily promotes that Bugcrowd is focused on finding hidden risks that other solutions miss:


As can be seen here, developers are not addressing non-hidden risks that could easily be addressed, so that should be focused on first. The likely explanation for promoting something else is that useful security work isn’t cheap for those providing it. While acting as an unnecessary intermediary can be very profitable.