Very Vulnerable WordPress Plugin Returns to Plugin Directory Without Being Fixed
When we discover a vulnerability in a plugin we can help protect the customers of our service by alerting them to the issue and they can then take the action they feel appropriate (we can also assist them in determining what is the appropriate action to take). For plugins that we seeing exploitation attempts against them, we also include the data on the vulnerabilities in the companion Plugin Vulnerabilities plugin, so even those who haven’t signed up the service get notified. But the best thing that can happens is that the developer of the plugin fixes the vulnerability to insure that everyone can get protected without having to do anything more than update the plugin.
After discovering a vulnerability we notify the developer of the plugin about the vulnerability and offer to help them fix it, but often we don’t even hear anything back from them and the vulnerability isn’t fixed. When that happens the last thing we can do is notify the Plugin Directory about the issue. For most vulnerabilities they will then pull the plugin from the Plugin Directory pending it being fixed.
Far too often having a plugin removed from the Plugin Directory will be the only thing that will get a developer to fix a vulnerability. In one recent case of this, the developer was posting comments on our post about a vulnerability in their plugin, claiming that there wasn’t actually a vulnerability, as they were fixing the vulnerability.
Unfortunately as we have found again the Plugin Directory doesn’t always make sure the at vulnerabilities have actually been fixed before returning to the Plugin Directory. This time it involves two vulnerabilities we discovered in the plugin BePro Listings at the beginning of the month. After seeing what look to be someone probing for usage of the plugin on one of our websites (we were not alone in seeing requests for this plugin), probably looking to exploit something in the plugin, we found that plugin had an arbitrary file upload vulnerability and a post deletion vulnerability. The post deletion vulnerability would allow anyone to delete any post or page on the website, without it being sent to the trash, so it could do a lot of damage, but it isn’t the type of vulnerability we see much in the way of exploit attempts. The arbitrary file upload vulnerability, which could allow a hacker to almost anything with the website, is the kind of vulnerability that hackers are often trying to exploit.
We contacted the developer of the plugin about the issue, but still have never heard back from them. Due to serious nature of the vulnerabilities and the fact that someone was likely looking to exploit them or something else in the plugin, we quickly notified the Plugin Directory and the plugin was removed. The plugin has returned after changes were made, but ones that did not fix the issues.
To see what went wrong let’s take a look at what was done.
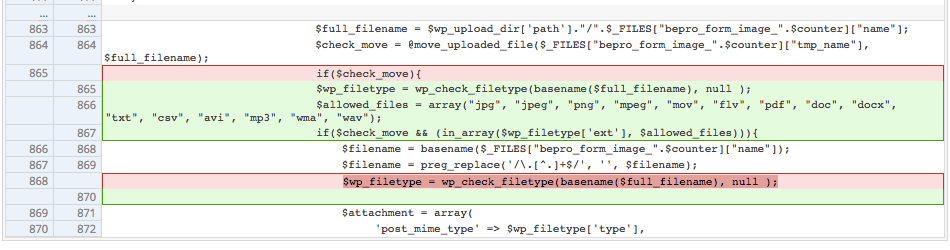
For the arbitrary file upload vulnerability from doing a diff from the development log you can see a change made to restrict what file extensions can be uploaded, which in a quick glance would look like it could fix the issue.
But by testing out the vulnerability with our proof of concept you would see that the file is still successfully uploaded. That is due to the fact that the code that restricts the file extension runs after the code that saves the uploaded file to the file system:
$check_move = @move_uploaded_file($_FILES["bepro_form_image_".$counter]["tmp_name"], $full_filename); |
For the post deletion vulnerability we are not sure how the change done was meant to fix the vulnerability. That vulnerability was due in large part due to the misuse of the function is_admin() and not limiting who could access the function that does the deleting. Nothing was done to fix either of those issue, instead a nonce check was added. Since that nonce is accessible on any listing created by the plugin, it has little impact on someone being able to exploit it.
Now we need to restart the process and notify the developer that issues still exist, hopefully the will get back to us this time so we can help them resolve this.