Wordfence Doesn’t Appear to Understand the Security Implications of a Backup Plugin
A little over a month ago we noted that Automattic’s WPScan didn’t appear to understand the concept of a backup plugin, as they claimed that 4+ million install WordPress backup plugin, All-in-One WP Migration, contained a vulnerability that:
allows administrators to upload PHP files on their site
The plugin explicitly allows backing up PHP files (as plugins contain PHP files):
Hit the export button to bundle your database, media files, plugins, and themes into one tidy file.
And it allows restoring them.
While WPScan claimed the vulnerability had been fixed, the new version of the plugin still “allows administrators to upload PHP files on their site”, because that is intended functionality of the plugin.
Maybe, another WordPress security provider, Wordfence, was feeling left out, so they made this claim yesterday:
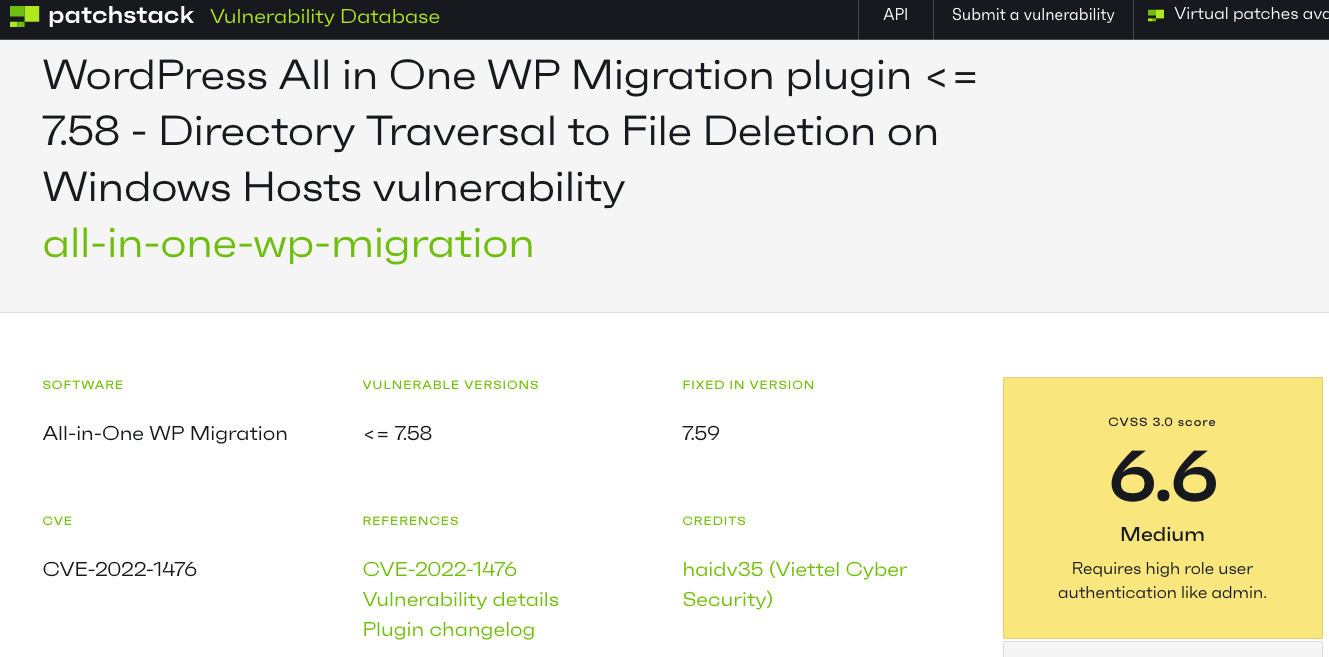
The All-in-One WP Migration plugin for WordPress is vulnerable to arbitrary file deletion via directory traversal due to insufficient file validation via the ~/lib/model/class-ai1wm-backups.php file, in versions up to, and including, 7.58. This can be exploited by administrative users, and users who have access to the site’s secret key on WordPress instances with Windows hosts.
The new version of the plugin did restrict what files can be deleted through functionality that is intended to delete backup files, which is a good idea. That doesn’t make it a vulnerability, as someone with access to the backup plugin functionality can, among other things, load up arbitrary PHP files on the website and use them to delete files or do just about anything else. Even if you didn’t understand the concept of a backup plugin, a WordPress security company should understand the implication of a WordPress user having the Administrator role.
The developer of the plugin provided an accurate description of the change and didn’t claim there was a vulnerability:
Fix a flaw in which the admin user has the ability to remove files other than backups
WPScan and Patchstack Spread This False Claim as Well
Wordfence isn’t the only one providing false information on this. Here is an entry from WPScan about this:

And another security provider, Patchstack:
Why is Wordfence a CVE Number Authority (CNA)?
Wordfence issued a CVE entry, CVE-2022-1476, for this false report.
Wordfence could create a CVE entry because they are CVE Number Authority (CNA). CVE describe those in this way:
In general, CNAs are vendors or other seasoned organizations with a record of researching vulnerabilities and demonstrating security advisory capabilities. They commonly have an established user base, and their security information is regularly consulted by researchers and vendors. They may also be well-established bug bounty hunters.
An onboarding process has been established to ensure that CNAs meet the standards of the CVE program. Potential CVE analysts and CNA candidates are given strict instructions for vetting vulnerabilities, including a wide range of examples and exercises. Should a CNA demonstrate the appropriate level of expertise and communication required, they are approved and become operational.
By any reasonable measure, that doesn’t describe Wordfence based on this situation or other CNAs we have run across. Nor does it describe WPScan or Patchstack, which are also CNAs.
Plugin Security Scorecard Grade for All-in-One WP Migration
Checked on November 22, 2024See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade