Hackers Probably Already Targeting Vulnerability Wordfence Disclosed Despite Fix Not Being Generally Available
Earlier today, Wordfence released an odd post on their blog. In the post they disclosed an incredibly easy to exploit a vulnerability in a WordPress plugin named Jupiter X Core, which allows anyone logged in to WordPress to change their role to Administrator. They claim to have engaged in “responsible disclosure” with this. While they didn’t provide what they labeled as a proof of concept, the information provides the equivalent of that. They are telling people to update version 2.0.8 of the plugin:
If you are running the JupiterX Core Plugin version 2.0.7 or below, you should immediately update it to version 2.0.8 or higher.
If you head over to the WordPress Plugin Directory, you see that something is off, as the latest version of the plugin is version 1.16.2:
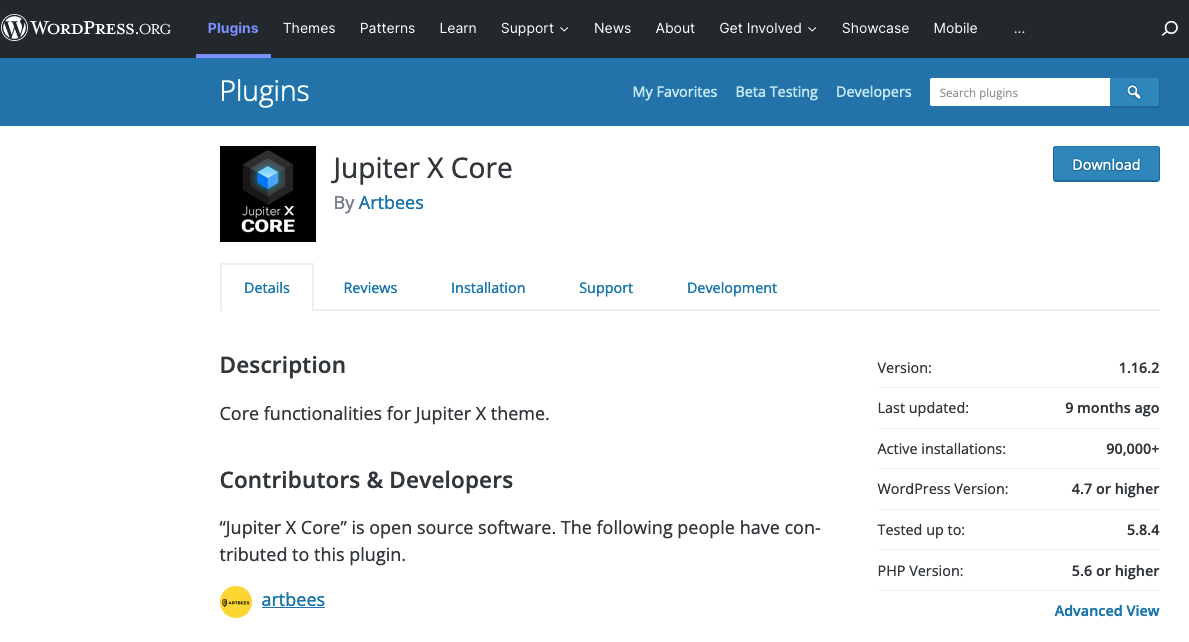
Their timeline says the vulnerability was addressed on May 10:
May 10, 2022 – Fully Patched versions of the Jupiter Theme and JupiterX Core plugin are released.
But the plugin was last updated 9 months ago.
Wordfence appears to be referring to a version of the plugin that isn’t available through the WordPress Plugin Directory. While we couldn’t find where that can be accessed, we did find release notes for the plugin that reference versions newer than 1.16.2. If someone knows where that can be accessed, please leave a comment below.
Wordfence’s post doesn’t address any of this, which is the odd part.
So there appears to be a new version of the plugin, but those who got the plugin through the WordPress Plugin Directory are not being provided with an update. That is a problem, as we have now confirmed that the vulnerability is at least exploitable when using version 1.16.2 of the plugin and the latest version of the free JupiterX Lite theme.
We are already seeing what appears to be hacker interest in exploiting this, as in the lasts couple of hours third-party data we monitor has recorded what probably are hackers probing for usage of the plugin by requesting this file from it:
/wp-content/plugins/jupiterx-core/assets/images/warning-badge.svg
We just contacted the developer of the plugin Artbees about the situation.
Based on our checking so far, some of the other vulnerabilities they claim are in the plugin don’t appear to exist as version 1.16.2.