WP Cerber Competitors Automattic and Patchstack Also Spread False Claim of Vulnerability in the Plugin
Earlier in the week, we detailed what looks to be going on with the closure of the popular WordPress security plugin WP Cerber on WordPress’ plugin directory. What seems like it could have started the closure was a claim made by a competing plugin, Wordfence, of a vulnerability in the plugin.
Here is how Wordfence described the issue:
The WP Cerber Security plugin for WordPress is vulnerable to security protection bypass in versions up to, and including 9.0, that makes user enumeration possible. This is due to improper validation on the value supplied through the ‘author’ parameter found in the ~/cerber-load.php file. In vulnerable versions, the plugin only blocks requests if the value supplied is numeric, making it possible for attackers to supply additional non-numeric characters to bypass the protection. The non-numeric characters are stripped and the user requested is displayed. This can be used by unauthenticated attackers to gather information about users that can targeted in further attacks.
Here is how we explained why that wasn’t a vulnerability:
Usernames are not considered a secret in WordPress, so it wouldn’t be a vulnerability for them to be shown. So there isn’t a vulnerability here, but WP Cerber itself is claiming that hiding the username is a security feature, when it isn’t.
Part of the problem with that is that the false claim of a vulnerability didn’t stay with Wordfence. The CVE system allowed them to include that false report, with entry ID, CVE-2022-2939. That entry only has two references. One is a link to a page on Wordfence’s website and the other is a link to a change being made in the plugin. That is despite the developer of WP Cerber stating that this isn’t a vulnerability:
I would prefer that some “security experts” (not WordFence) do their jobs more responsibly. I saw a report regarding a WP Cerber bug that is claimed as a vulnerability but it’s not a vulnerability per se. It’s a built-in WordPress feature. I really appreciate and thankful to people reporting bugs and other issues, but this time it’s not what it’s claimed. WP Cerber users, as always, can sleep calmly.
P.S. The reported bug has been fixed in WP Cerber 9.1.
In addition to CVE, two additional competitors to WP Cerber are also claiming there had been a vulnerability. One of them being the developer of the Jetpack security plugin, Automattic, that added this entry to their WPScan database:
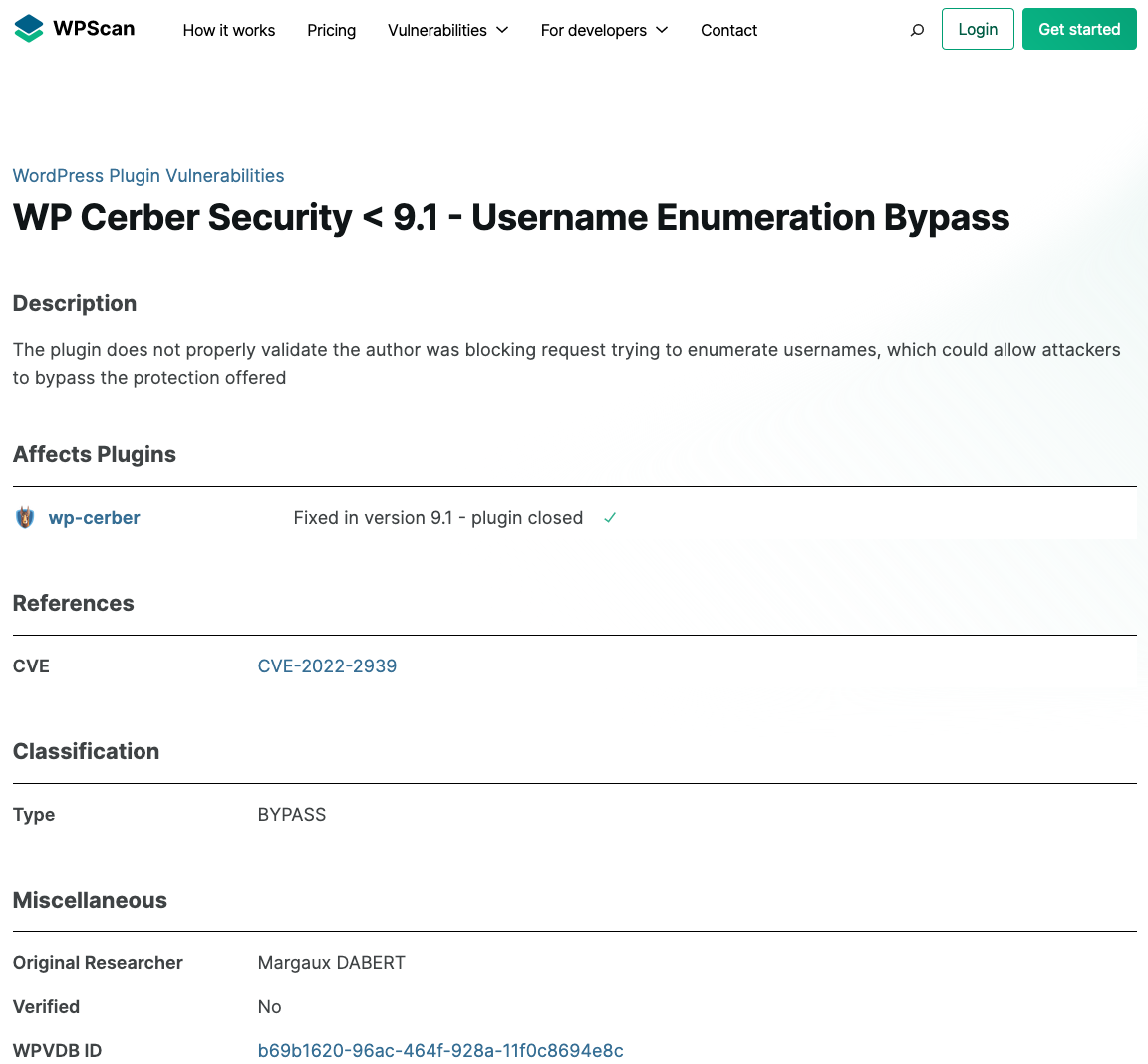
Strangely, they claim the vulnerability hasn’t been verified, but also that it has been fixed. How can they say it has been fixed without verifying it?
At least here you could try to make an argument that there really was a vulnerability. But in April we noted an instance where Automattic’s WPScan was the original source for a claim of a vulnerability in another competing security plugin that didn’t exist at all. CVE had also allowed that false information in their system. (We noted yet another situation with Automattic falsely claiming there was a vulnerability in another competing security plugin the next month.)
As with the situation in April, another competitor, Patchstack, is also spreading a false claim about a competitor:
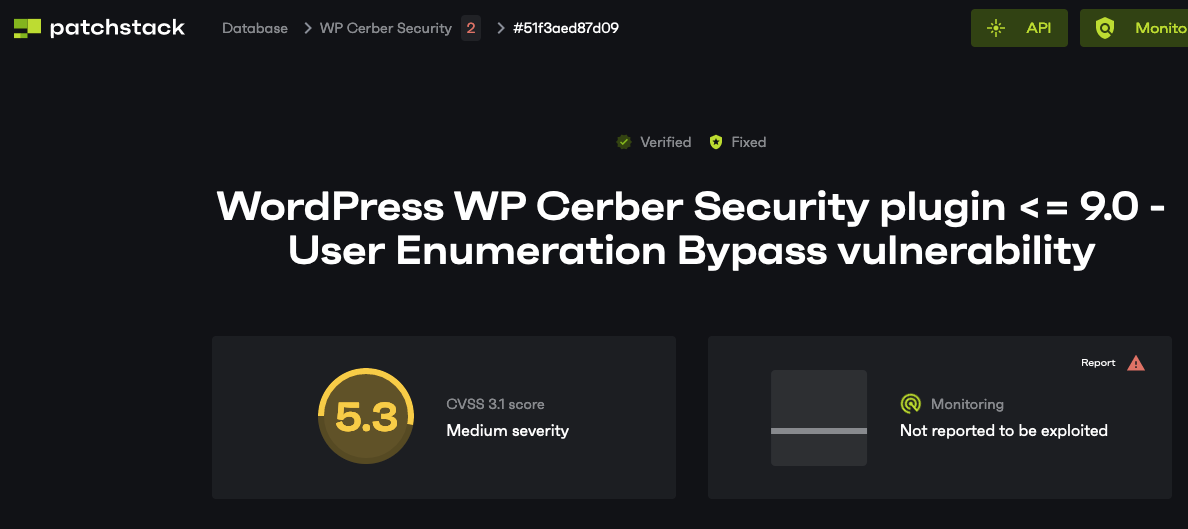
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade