Automattic’s Idea of Coopetition Involves Copying Data From Competitors Without Credit
Companies operating in the WordPress space have to deal with a problematic situation. While WordPress is promoted as an open source community, the head of WordPress, Matt Mullenweg, uses his various entities to exert control and influence over the community to the benefit of his business interests. One of those entities is the news outlet the WP Tavern, which, when covering him, doesn’t disclose it is owned by him and its writers work for him. That lack of disclosure occurred again with a recent story about one of his employees causing WordPress to hide information useful to competing companies .
In the story, it also wasn’t disclosed that one of the quoted sources, Josepha Haden Chomphosy, is an employee of Matt Mulleweg’s company Automattic, instead incompletely describing her as “WordPress Executive Director”. She was quoted saying that there should be a focus on coopetition mindset in terms of data access:
WordPress Executive Director Josepha Haden-Chomphosy joined the discussion in the channel but had very little information to offer about why this change was made without any public discussion.
“The data shared is always a bit obfuscated so that it’s harder to ‘game the system’—the same reason we don’t have running leaderboards for contributions,” Haden-Chomphosy said.
“Suggestions are welcome for how to get some data for you all while doing our best to stick with a ‘co-opetition‘ mindset.”
Co-opetition is a term coined to meld the concepts of cooperation and competition to create a system where different vendors cooperate for the benefit of the system while still competing. Haden-Chomphosy did not elaborate but it seems that obfuscating data had been deemed a necessary sacrifice for the sake of co-opetition.
That is a curious position considering that Automattic isn’t very cooperative when it comes to data coming from competitors.
Copying Without Credit
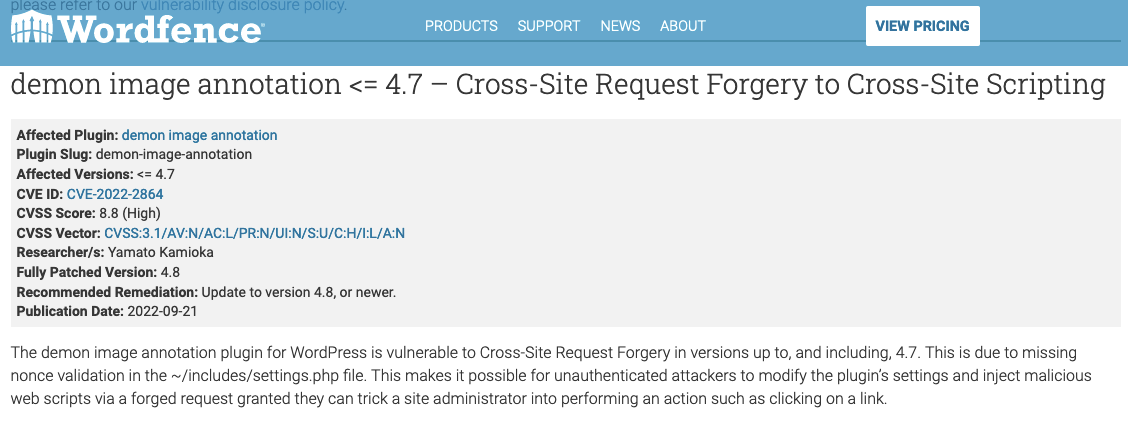
Last week we discovered and disclosed a serious vulnerability in a plugin that is developed, though not disclosed to be developed, by Automattic. Automattic then included that vulnerability in the competing WPScan’s data set without crediting us (they also managed to misspell “upload”):
That lack of credit isn’t surprising since WPScan has long have had a hostile attitude towards us. (That has led to bad results for their customers since they often don’t warn them they may have already been exploited through zero-day vulnerabilities we have run across.) But it now isn’t only us they are doing that with.
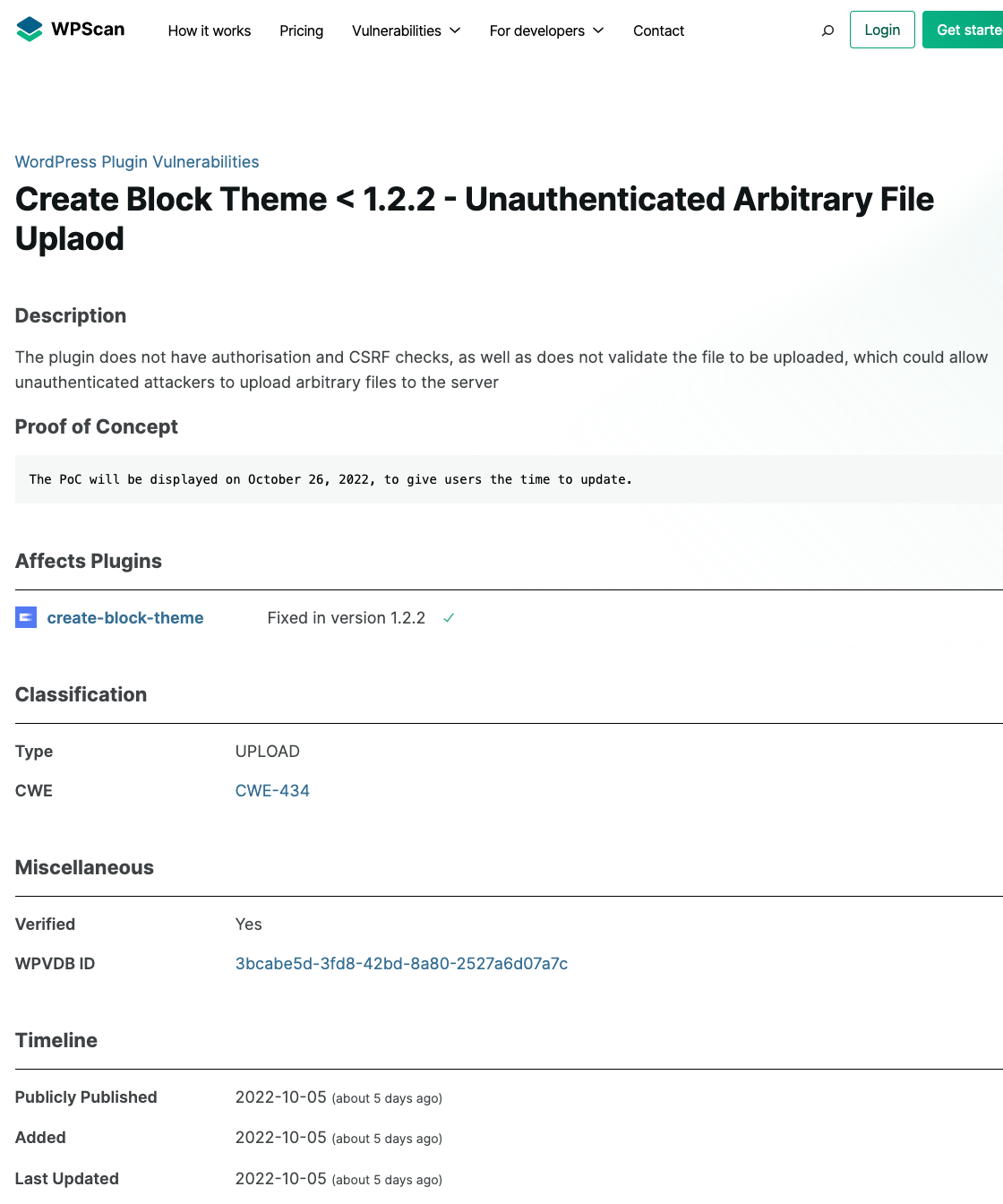
Copying From Wordfence Without Credit as Well
Here is an entry for a vulnerability recently discovered by another competitor, Wordfence, which doesn’t credit them either:
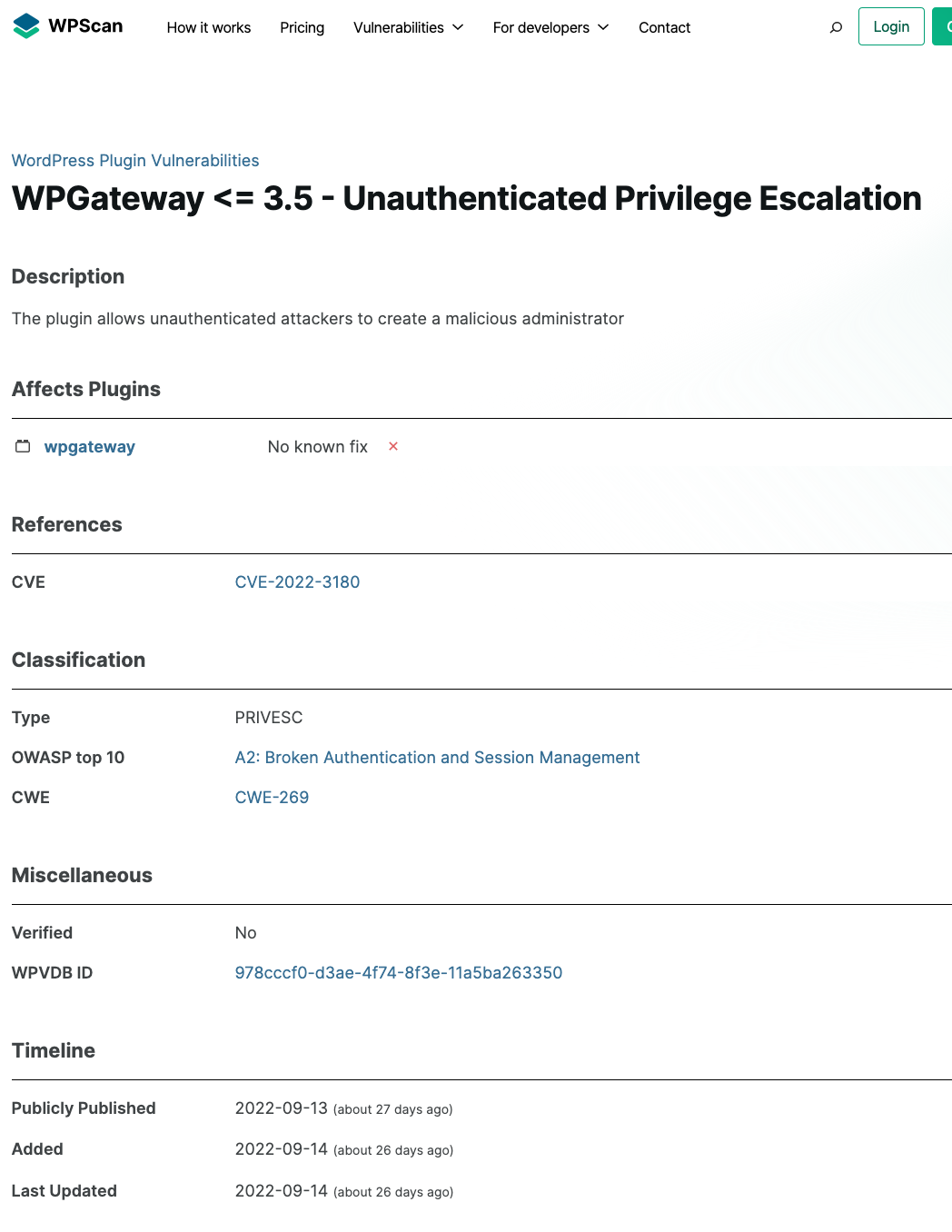
The only listed reference is to a CVE entry, which is currently empty and therefore couldn’t be the source:
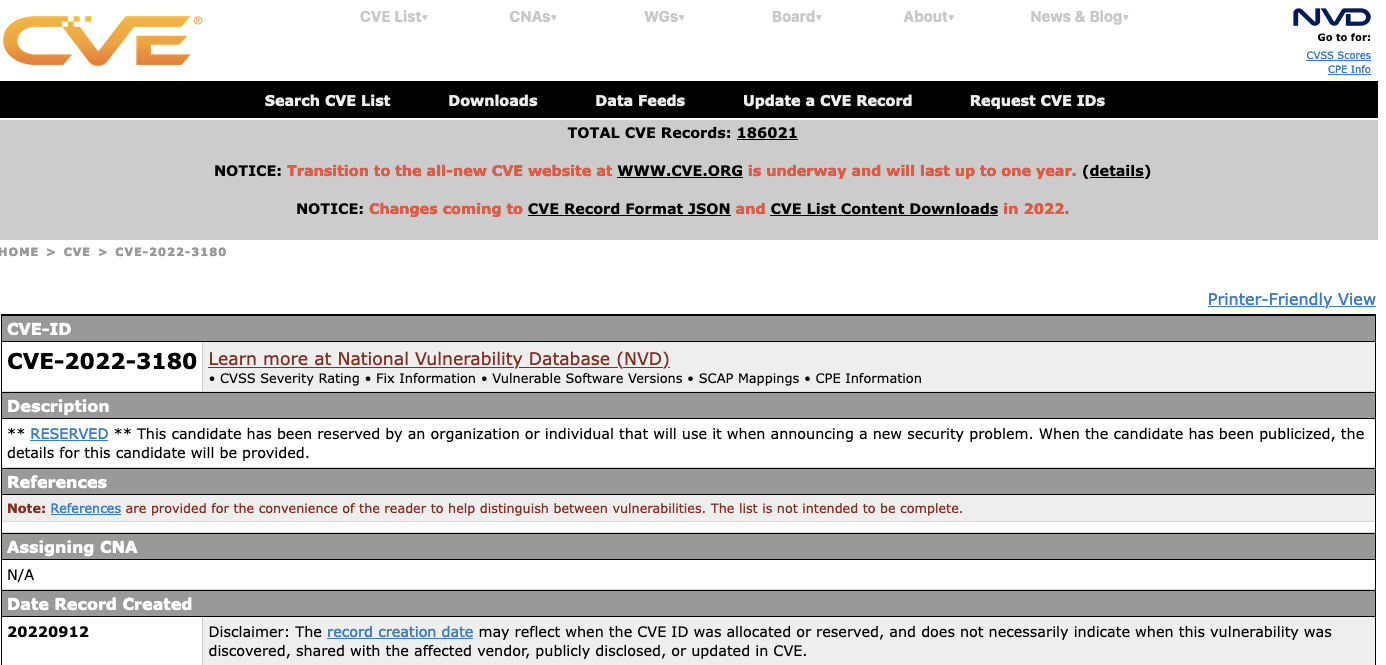
Here is another recent entry:
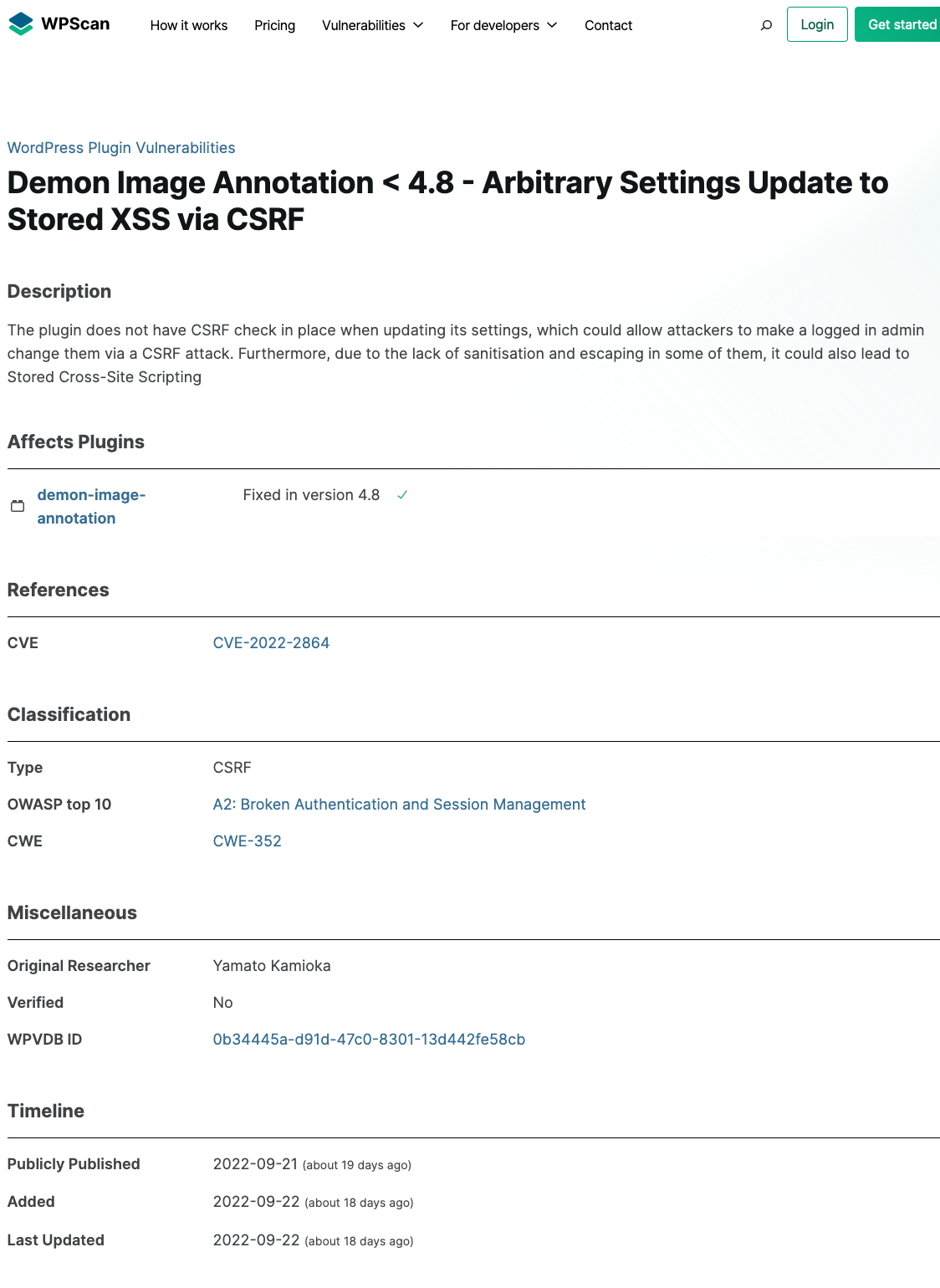
That mention’s a discoverer, but again, the only reference is a CVE entry that is currently empty:
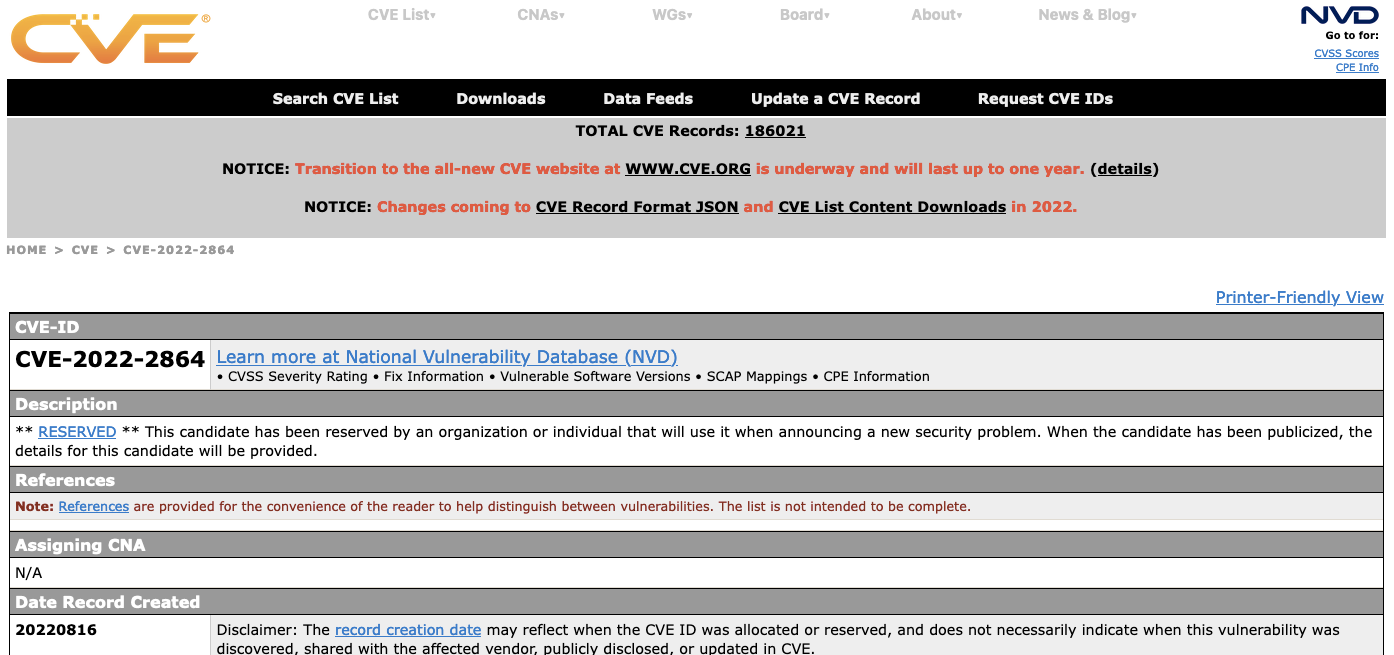
So that clearly can’t be the source. The actual source is Wordfence’s website: