Wordfence Intelligence Community Edition Data Falsely Claims That Unfixed Plugin Vulnerability Was Fixed Twice
In what appears to be a significant setback for Wordfence, but promoted as “a gift to the community”, they announced they are now giving away data on vulnerabilities in WordPress plugins they have been trying to sell access to since August, as part of Wordfence Intelligence (which we previously discussed, wasn’t delivering on its promises). They are now branding this data as Wordfence Intelligence Community Edition.
Before the data was publicly available, we had been running across indications it was of rather poor quality, including falsely claiming a plugin contained a “critical” vulnerability because they confused it with another plugin, claiming another plugin contained “critical” vulnerability despite having no idea if that was true, and other apparent instances of false claims of vulnerabilities. Now that their data set is out in the open, we can get a better look at it and the first things we went to check on showed that the quality is indeed rather poor. Which makes providing it for free make more sense, but it joins a crowded field of at least partially free options with quality issues of their own.
Falsely Claiming a Vulnerability Was Fixed Twice
On November 7, we warned our customers that the developer of the 300,000+ install WordPress plugin Photo Gallery had failed in an attempt to fix an open redirect vulnerability in the plugin. We notified the developer that they had failed to fix that at the time. On November 23, they made a second failed attempt to fix it in version 1.8.3. On November 30, they finally got back to us and told it had been fixed in version 1.8.3, which we replied back was not correct. So far, they have not fixed the issue or gotten back to us.
(Based on continued inability to handle security properly by the developer, 10Web, we also released a developer security advisory for them in November.)
Wordfence, by comparison, has claimed the vulnerability has been fixed twice. Here is their entry on the first attempt:

Here is the entry on the second attempt:
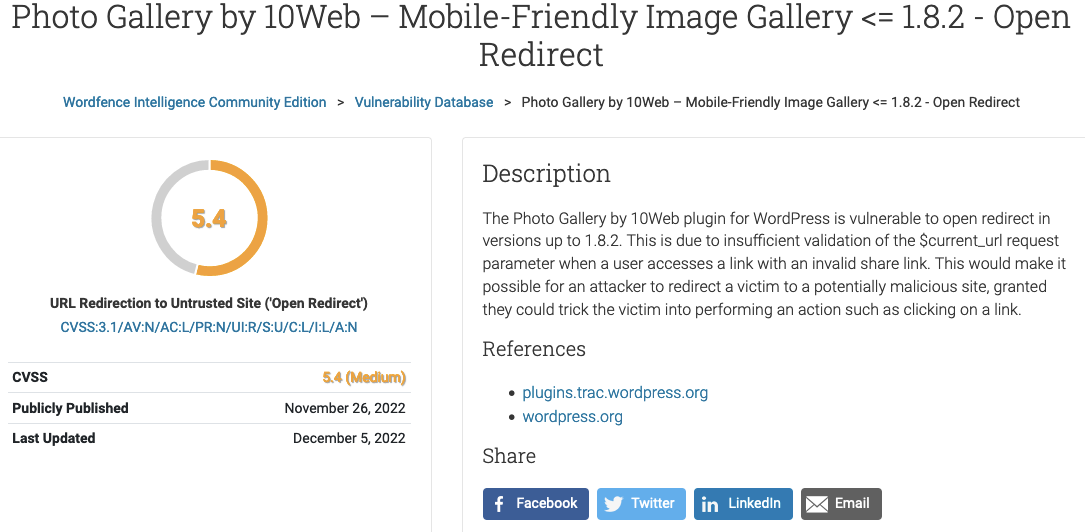
The description for each is identical, except for the version number mentioned.
Clearly, they didn’t actually check over this, as if they had done that, they would have seen, as we did, it hadn’t been addressed. Somehow, they also missed that they were claiming it had been fixed twice.
Missing Details Needed To Confirm Their Claims
Wordfence says their “hope” is that “hosting companies, software developers and security providers will turn this data into free and commercial security products that will improve the security of the WordPress community”, but looking over their entries, there is a lack of basic details needed to check if their information is incorrect, as it was above. That would normally come in the form of a proof of concept or the relevant code. Without that, there is a limited ability for other to check on their claims, and catch when the data is wrong.
Late Warning for Probable Zero-Day
Part of their marketing of this data claims that others can “respond to threats in a timely manner”:
Our goal is to provide site owners with as much information needed to effectively secure their WordPress websites while also providing security analysts and researchers the information needed to be able monitor the WordPress threat landscape so they can respond to threats in a timely manner and provide their insights back to the community.
Something else we checked on in their data showed that not to be true.
On November 28, we warned of what appeared to be a zero-day vulnerability in a WordPress plugin that we noticed because a hacker had been probing for the plugin several days before that. We also noted that other providers were not already warning about that, despite having had days to have done that.
Wordfence apparently only started warning about that over a week later on December 7:
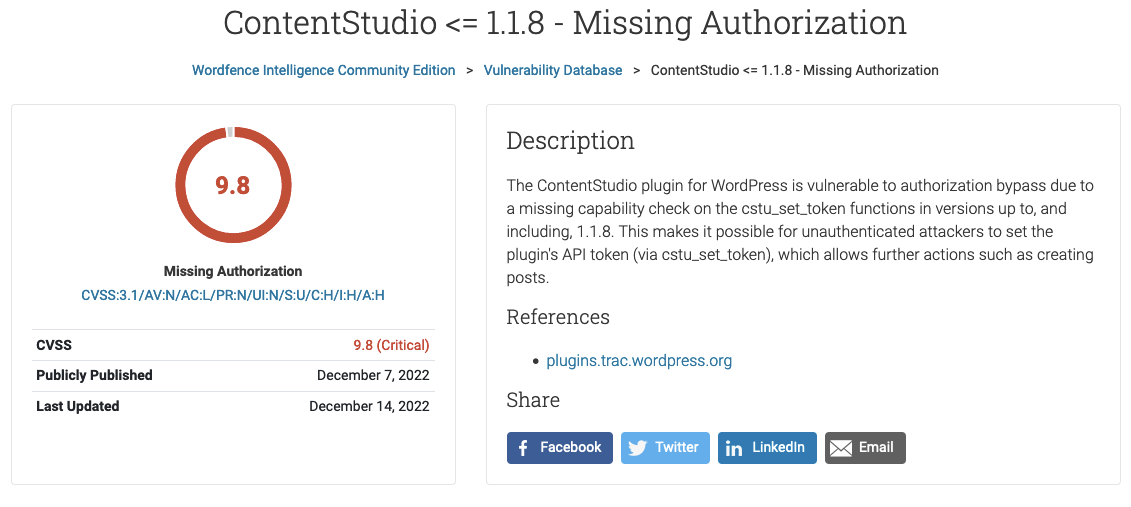
No Warning Yet
At another point, they claim they claim to have the most “current vulnerability database”:
We will continue to populate historical vulnerability data while also ensuring we have the most comprehensive and current vulnerability database on the market for the community to use.
Elsewhere, they claim to be “adding new vulnerabilities as soon as they are discovered”:
We are investing heavily in this database by growing the team, maintaining and curating the existing data, and adding new vulnerabilities as soon as they are discovered.
There is no delay on how quickly we add vulnerabilities to this free database. As soon as a vulnerability is disclosed, we add it.
That couldn’t be true, since they would have to be discovering them themselves to do that, but was that zero-day we mentioned a fluke of them not failing to warn promptly? No. Yesterday, we warned our customers about a developer’s only partially successful attempt to address vulnerabilities in their plugins. Wordfence’s data has yet to warn about those, much less note the incomplete fix.
Free Labor for Wordfence
Based on their post, what this appears to be about, in part, is getting free labor. As they are trying to get people to submit information on vulnerabilities to them for free instead of Wordfence doing the work themselves. This is a common practice among low quality data sources like this. As we recently highlighted with another of these, WPScan, the quality of the results is in line with what you would get when you don’t spend money on your data gathering.
Paying for Verified Data Pays Off
As can be seen with the examples above, you do get what you can now pay for when it comes to data on vulnerabilities in WordPress plugins from Wordfence. If you need accurate data on vulnerabilities (and what else would you want), you should look for a paid source that actually verifies the information they are providing, instead of looking for others to do the work for them for free because the results from those have consistently been bad. Otherwise, you are giving yourself a false sense of security at best and getting hacked because of an issue you should have known about at worst.